IPv6/MAC Spoofing Attacks
This section describes IPv6/MAC spoofing attacks and provides the corresponding attack defense solutions.
Attack Mechanism
- IPv6/MAC spoofing attack
This type of spoofing attack forges the data of authorized users, allowing attackers to masquerade as authorized users and use network services, while authorized users themselves fail to obtain services.
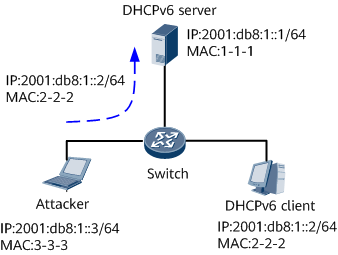
Specifically, an attacker sends a packet carrying the IPv6 address and MAC address of an authorized user to the server, which in turn mistakenly considers that it has learned the IPv6 address and MAC address of the authorized user. The server then sends valid information to the attacker, whereas the authorized user cannot obtain services from the server. Figure 1 illustrates an IPv6/MAC spoofing attack.
Solution
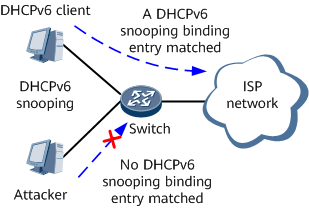
A DHCPv6 snooping binding table can be used to effectively prevent IPv6/MAC spoofing attacks, as shown in Figure 2.
Attack Packet |
Relevant Feature |
Function |
|---|---|---|
Bogus IPv6 packet |
DHCPv6 snooping |
If no DHCPv6 snooping binding entry is found based on the source IPv6 address, prefix, VLAN ID, and VPN information in an IPv6 packet, the IPv6 packet is simply discarded. If a DHCPv6 snooping binding entry is found based on the source IPv6 address, prefix, VLAN ID, and VPN information in the IPv6 packet but the source MAC address and interface information in this binding entry do not match those in the IPv6 packet, this packet is also discarded. |

If a user is configured with a static IPv6 address, there will be no corresponding DHCPv6 snooping binding entry because this IPv6 address is not obtained through a DHCPv6 request. Therefore, the IPv6 packets sent by this user will be discarded. To prevent this, you can configure only a static binding table, allowing the authorized static users to access the network while preventing access by unauthorized users.
If a user unexpectedly goes offline after obtaining an IPv6 address, the user cannot send a DHCPv6 Release message to release the requested IPv6 address. In this case, you can enable association between ND probe and DHCPv6 snooping. The system will then perform ND probe on the IPv6 addresses that have reached the aging time in the corresponding DHCPv6 snooping entries but do not exist in the corresponding ND entries. If the user cannot be detected within the specified number of probes, the system will delete the DHCPv6 binding entry and notify the DHCPv6 server of releasing the IPv6 address.