SELinux
Security-Enhanced Linux (SELinux) is a security module of the Linux kernel. It provides the mandatory access control (MAC) mechanism to protect sensitive or important files based on customized requirements in the Linux system.
SELinux adopts user-defined rules to restrict users' access permissions during program running. This mechanism is independent of other secure access control mechanisms of the Linux kernel and is a powerful supplement to the discretionary access control (DAC) mechanism.
Background
Traditional UNIX permission access control is based on the DAC mechanism, which can determine permissions based on the runtime identity. Generally, the file system restricts permissions based on the r (read), w (write), and x (delete) of the owner, group, and other permission groups. Due to lack of detailed permission classification, permissions cannot be restricted for different processes. If all programs are authorized to access a file, malicious programs may have the same access permission, which poses security risks. Compared with the DAC mechanism, the MAC mechanism provided by SELinux offers additional control over the permissions on specific items, covering the file system, files, directories, processes, file descriptors, ports, messages, and network interfaces.
Related Concepts
DAC is an access control mode in which an access permission is determined based on runtime identity.
The MAC mechanism completely controls access and can control access permissions on specific items based on the DAC mechanism.
Fundamentals
SELinux performs the MAC security mechanism based on the domain-type model. A process is defined as a subject, resources (such as files and directories) to be accessed are defined as objects, and a series of permission access rules for the subject domain accessing the object types are defined based on the security context. In this way, access control is implemented. With SELinux used, even if a restricted process is compromised by an attacker, the attacker can access resources only within the specified permission range, limiting the damage scope.
The SELinux mechanism involves the following parts:
- Subject and object: A subject refers to a visitor (usually a process), and an object refers to an accessed resource.
- Security context: extended attribute, including the user, role, domain, type identifier, or any combination of them. Each subject/object has a security context associated with it.
- Domain and type: An item is assigned a domain or type. A domain corresponds to a subject, and a type corresponds to an object.
- SELinux policy: An SELinux policy is a set of access restrictions between a subject and an object. All access control is based on policies. These policies are set by the administrator and cannot be changed by common users. A SELinux policy grants a subject domain the permission to access a type of object based on the security context by using an allow rule. An allow rule is in the following format: allow subject-type object-type:object-class {allowed-operation-set (such as read-only, read and write, and delete)} To improve efficiency of SELinux policy compilation, some attributes are defined. The permission shared by a class of types (objects) is extracted and associated with an attribute. The association enables the allow rule to be set based on the associated attribute. The advantages of this method are as follows:
- If you need to modify a shared permission, you only need to modify the permission of the associated attribute.
- When a new type in a class is defined, you can associate the new type with the attributes of the class.
- AVC logs: The system records all access operations that are not allowed by policies in AVC messages and stores the AVC messages in the /var/log/audit/audit.log file.
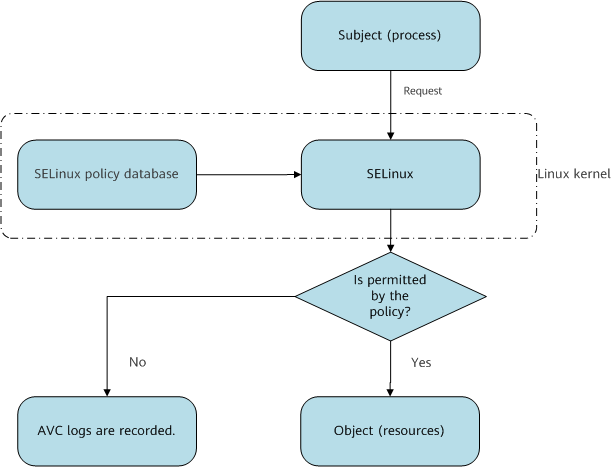
As shown in Figure 1, if a subject (process) wants to access a target object (resource file), the subject (process) sends a request to the SELinux component of the Linux kernel. After receiving the request, the SELinux component must analyze the policy rule and compare the security contexts of the subject domain and object type. If the security context complies with the allow rule in the SELinux policy database, the process is allowed to access the target resource. SELinux supports permissive and enforcing modes. In permissive mode, if access operations are not allowed by a policy, the system does not reject them but can record these operations. In enforcing mode, the system rejects the operations that are not allowed by a policy. Currently, the VRPv8 system uses the enforcing mode.
Benefits
SELinux uses user-defined rules to restrict users' access permissions during program running, reducing the impact and loss caused by attacks.