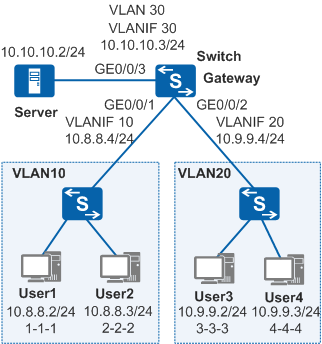
Example for Configuring ARP Security Functions
Networking Requirements
- Attackers send bogus ARP packets or bogus gratuitous ARP packets to the switch. ARP entries on the switch are modified, leading to packet sending and receiving failures.
- Attackers send a large number of IP packets with unresolvable destination IP addresses to the switch, leading to CPU overload.
- User1 sends a large number of ARP packets with fixed MAC addresses but variable source IP addresses to the switch. As a result, ARP entries on the switch are exhausted and the CPU cannot process other services.
- User3 sends a large number of ARP packets with fixed source IP addresses to the switch. As a result, the CPU of the switch is insufficient to process other services.
Configuration Roadmap
- Configure strict ARP learning and ARP entry fixing to prevent ARP entries from being modified by bogus ARP packets.
- Configure rate-limiting on ARP Miss messages based on source IP addresses. This function defends against attacks from ARP Miss messages triggered by a large number of IP packets with unresolvable IP addresses. At the same time, the switch must have the capability to process a large number of ARP Miss packets from the server to ensure network communication.
- Configure ARP entry limiting on a per-interface basis and rate-limiting on ARP packets based on source MAC addresses. These functions defend against ARP flood attacks caused by a large number of ARP packets with fixed MAC addresses but variable IP addresses and prevent ARP entries from being exhausted and CPU overload.
- Configure rate-limiting on ARP packets based on source IP addresses. This function defends against ARP flood attacks from User3 with a fixed IP address and prevents CPU overload.
Procedure
- Create VLANs, add interfaces to the VLANs, and configure
VLANIF interfaces.
# Create VLAN 10, VLAN 20, VLAN 30, and add GE0/0/1 to VLAN 10, GE0/0/2 to VLAN 20, and GE0/0/3 to VLAN 30.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] vlan batch 10 20 30 [Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] port link-type trunk [Switch-GigabitEthernet0/0/1] port trunk allow-pass vlan 10 [Switch-GigabitEthernet0/0/1] quit [Switch] interface gigabitethernet 0/0/2 [Switch-GigabitEthernet0/0/2] port link-type trunk [Switch-GigabitEthernet0/0/2] port trunk allow-pass vlan 20 [Switch-GigabitEthernet0/0/2] quit [Switch] interface gigabitethernet 0/0/3 [Switch-GigabitEthernet0/0/3] port link-type trunk [Switch-GigabitEthernet0/0/3] port trunk allow-pass vlan 30 [Switch-GigabitEthernet0/0/3] quit
# Create VLANIF 10, VLANIF 20, and VLANIF 30, and assign IP addresses to them.
[Switch] interface vlanif 10 [Switch-Vlanif10] ip address 10.8.8.4 24 [Switch-Vlanif10] quit [Switch] interface vlanif 20 [Switch-Vlanif20] ip address 10.9.9.4 24 [Switch-Vlanif20] quit [Switch] interface vlanif 30 [Switch-Vlanif30] ip address 10.10.10.3 24 [Switch-Vlanif30] quit
- Configure strict ARP learning.
[Switch] arp learning strict - Configure ARP entry fixing.
# Set the ARP entry fixing mode to fixed-mac.
[Switch] arp anti-attack entry-check fixed-mac enable - Configure
rate-limiting on ARP Miss messages based on source IP addresses.
# Set the maximum rate of ARP Miss messages triggered by the server (IP address 10.10.10.2) to 40 pps, and set the maximum rate of ARP Miss messages triggered by other user hosts to 20 pps.
[Switch] arp-miss speed-limit source-ip maximum 20 [Switch] arp-miss speed-limit source-ip 10.10.10.2 maximum 40
- Configure interface-based ARP entry limiting.
# Set the maximum number of ARP entries that GE0/0/1 dynamically learns to 20.
[Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] arp-limit vlan 10 maximum 20 [Switch-GigabitEthernet0/0/1] quit
- Configure
rate-limiting on ARP packets based on source MAC addresses.
# Set the maximum rate of ARP packets from User1 with the source MAC address 1-1-1 to 10 pps.
[Switch] arp speed-limit source-mac 1-1-1 maximum 10 - Configure rate-limiting on ARP packets based on source
IP addresses.
# Set the maximum rate of ARP packets from User3 with the source IP address 10.9.9.2 to 10 pps.
[Switch] arp speed-limit source-ip 10.9.9.2 maximum 10 - Verify the configuration.
# Run the display arp learning strict command to check the global configuration of strict ARP entry learning.
[Switch] display arp learning strict The global configuration:arp learning strict Interface LearningStrictState ------------------------------------------------------------ ------------------------------------------------------------ Total:0 Force-enable:0 Force-disable:0# Run the display arp-limit command to check the maximum number of ARP entries that the interface can dynamically learn.
[Switch] display arp-limit interface gigabitethernet 0/0/1 Interface LimitNum VlanID LearnedNum(Mainboard) --------------------------------------------------------------------------- GigabitEthernet0/0/1 20 10 0 --------------------------------------------------------------------------- Total:1
# Run the display arp anti-attack configuration all command to check the configuration of ARP anti-attack.
[Switch] display arp anti-attack configuration all ...... ARP anti-attack entry-check mode: Vlanif Mode ------------------------------------------------------------------------------- All fixed-mac ------------------------------------------------------------------------------- ...... ARP speed-limit for source-MAC configuration: MAC-address suppress-rate(pps)(rate=0 means function disabled) ------------------------------------------------------------------------------- 0001-0001-0001 10 Others 0 ------------------------------------------------------------------------------- The number of configured specified MAC address(es) is 1, spec is 512. ARP speed-limit for source-IP configuration: IP-address suppress-rate(pps)(rate=0 means function disabled) ------------------------------------------------------------------------------- 10.9.9.2 10 Others 0 ------------------------------------------------------------------------------- The number of configured specified IP address(es) is 1, spec is 512. ARP miss speed-limit for source-IP configuration: IP-address suppress-rate(pps)(rate=0 means function disabled) ------------------------------------------------------------------------------- 10.10.10.2/32 40 Others 20 ------------------------------------------------------------------------------- The number of configured specified IP address(es) is 1, spec is 512.
# Run the display arp packet statistics command to check statistics on ARP packets.
[Switch] display arp packet statistics ARP Pkt Received: sum 8678904 ARP-Miss Msg Received: sum 183 ARP Learnt Count: sum 37 ARP Pkt Discard For Limit: sum 146 ARP Pkt Discard For SpeedLimit: sum 40529 ARP Pkt Discard For Proxy Suppress: sum 0 ARP Pkt Discard For Other: sum 8367601 ARP-Miss Msg Discard For SpeedLimit: sum 20 ARP-Miss Msg Discard For Other: sum 104In the preceding command output, the numbers of ARP packets and ARP Miss messages discarded by the switch are displayed, indicating that the ARP security functions have taken effect.
Configuration File
Switch configuration file
# sysname Switch # vlan batch 10 20 30 # arp learning strict # arp-miss speed-limit source-ip 10.10.10.2 maximum 40 arp speed-limit source-ip 10.9.9.2 maximum 10 arp speed-limit source-mac 0001-0001-0001 maximum 10 arp anti-attack entry-check fixed-mac enable # arp-miss speed-limit source-ip maximum 20 # interface Vlanif10 ip address 10.8.8.4 255.255.255.0 # interface Vlanif20 ip address 10.9.9.4 255.255.255.0 # interface Vlanif30 ip address 10.10.10.3 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 10 arp-limit vlan 10 maximum 20 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 20 # interface GigabitEthernet0/0/3 port link-type trunk port trunk allow-pass vlan 30 # return