RADIUS CoA/DM
RADIUS CoA/DM packet
Table 1 describes types of the CoA/DM packets.
Packet Name |
Description |
|---|---|
CoA-Request |
When an administrator needs to modify the rights of an online user (for example, prohibit the user from accessing a website), the RADIUS server sends this packet to the RADIUS client, requesting the client to modify the user rights. |
CoA-ACK |
If the RADIUS client successfully modifies the user rights, it returns this packet to the RADIUS server. |
CoA-NAK |
If the RADIUS client fails to modify the user rights, it returns this packet to the RADIUS server. |
DM-Request |
When an administrator needs to disconnect a user, the server sends this packet to the RADIUS client, requesting the client to disconnect the user. |
DM-ACK |
If the RADIUS client has disconnected the user, it returns this packet to the RADIUS server. |
DM-NAK |
If the RADIUS client fails to disconnect the user, it returns this packet to the RADIUS server. |
Exchange Procedure
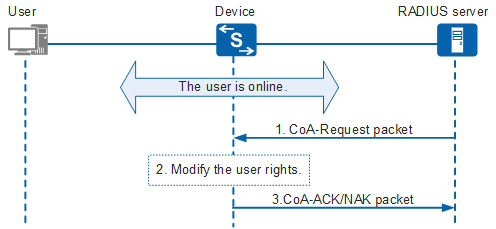
CoA allows the administrator to change the rights of an online user or perform reauthentication for the user through RADIUS after the user passes authentication. Figure 1 shows the CoA interaction process.
- The RADIUS server sends a CoA-Request packet to the device according to service information, requesting the device to modify user authorization information. This packet can contain authorization information including the ACL.
- Upon receiving the CoA-Request packet, the device performs a match check between the packet and user information on the device to identify the user. If the match succeeds, the device modifies authorization information of the user. Otherwise, the device retains the original authorization information of the user.
- The device returns a CoA-ACK or CoA-NAK packet as follows:
- If authorization information is successfully modified, the device sends a CoA-ACK packet to the RADIUS server.
- If authorization information fails to be modified, the device sends a CoA-NAK packet to the RADIUS server.
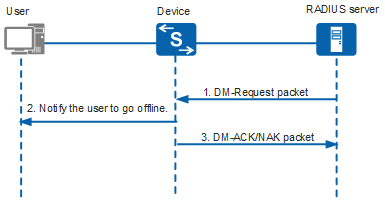
When a user needs to be disconnected forcibly, the RADIUS server sends a DM packet to the device. Figure 2 shows the DM interaction process.
- The administrator forcibly disconnects a user on the RADIUS server. The RADIUS server sends a DM-Request packet to the device, requesting the device to disconnect the user.
- Upon receiving the DM-Request packet, the device performs a match check between the packet and user information on the device to identify the user. If the match succeeds, the user is notified to go offline. Otherwise, the user remains online.
The device returns a DM-ACK or DM-NAK packet as follows:
- If the user successfully goes offline, the device sends a DM-ACK packet to the RADIUS server.
- Otherwise, the device sends a DM-NAK packet to the RADIUS server.
Different from the process in which authorization is performed for an online user or a user proactively goes offline, the server sends a request packet and the device sends a response packet in the CoA/DM process. If CoA/DM succeeds, the device returns an ACK packet. Otherwise, the device returns a NAK packet.
Session Identification
Each service provided by the NAS to a user constitutes a session, with the beginning of the session defined as the point where service is first provided and the end of the session defined as the point where service is ended.
- User-Name (IETF attribute #1)
- Acct-Session-ID (IETF attribute #4)
- Framed-IP-Address (IETF attribute #8)
- Calling-Station-Id (IETF attribute #31)
The match methods are as follows:
any method
The device performs a match check between an attribute and user information on the device. The priority for identifying the RADIUS attributes used by the users is as follows: Acct-Session-ID (4) > Calling-Station-Id (31) > Framed-IP-Address (8). The device searches for the attributes in the request packet based on the priority, and performs a match check between the first found attribute and user information on the device. If the attribute is successfully matched, the device responds with an ACK packet; otherwise, the device responds with a NAK packet.
all method
The device performs a match check between all attributes and user information on the device. The device identifies the following RADIUS attributes used by the users: Acct-Session-ID (4), Calling-Station-Id (31), Framed-IP-Address (8), and User-Name (1). The device performs a match check between all the preceding attributes in the Request packet and user information on the device. If all the preceding attributes are successfully matched, the device responds with an ACK packet; otherwise, the device responds with a NAK packet.
Error Code Description
When the CoA-Request or DM-Request packet from the RADIUS server fails to match user information on the device, the device describes the failure cause using the error code in the CoA-NAK or DM-NAK packet. For the error code description, see Table 2 and Table 3.
Name |
Value |
Description |
|---|---|---|
| RD_DM_ERRCODE_MISSING_ATTRIBUTE | 402 | The request packet lacks key attributes, so that the integrity check of the RADIUS attributes fails. |
| RD_DM_ERRCODE_INVALID_REQUEST | 404 | Parsing the attributes in the request packet fails. |
| RD_DM_ERRCODE_INVALID_ATTRIBUTE_VALUE | 407 | The request packet contains attributes that are not supported
by the device or do not exist, so that the attribute check fails. Contents of the authorization check include VLAN, ACL, CAR, number of the ACL used for redirection, and whether Huawei RADIUS extended attributes RD_hw_URL_Flag and RD_hw_Portal_URL can be authorized to the interface-based authenticated user. Errors that may occur are as follows:
|
| RD_DM_ERRCODE_SESSION_CONTEXT_NOT_FOUND | 503 | The session request fails. The cause includes:
|
| RD_DM_ERRCODE_RESOURCES_UNAVAILABLE | 506 | This error code is used for other authorization failures. |