RADIUS Server Status Detection
Availability and maintainability of a RADIUS server are the prerequisites of user access authentication. If a device cannot communicate with the RADIUS server, the server cannot perform authentication or authorization for users. To resolve this issue, the device supports the user escape function upon transition of the RADIUS server status to Down. To be specific, if the RADIUS server goes Down, users cannot be authorized by the server but still have certain network access rights.
The user escape function upon transition of the RADIUS server status to Down can be enabled only after the device marks the RADIUS server status as Down. If the RADIUS server status is not marked as Down and the device cannot communicate with the RADIUS server, users cannot be authorized by the server and the escape function is also unavailable. As a result, users have no network access rights. Therefore, the device must be capable of detecting the RADIUS server status in a timely manner. If the device detects that the RADIUS server status transitions to Down, users can obtain escape rights; if the device detects that the RADIUS server status reverts to Up, escape rights are removed from the users and the users are reauthenticated.
RADIUS Server Status
A device can mark the RADIUS server status as Up, Down, or Force-up. The following table lists descriptions of the three RADIUS server status and their corresponding scenarios.
Status |
Whether the RADIUS Server Is Available |
Condition for Switching the Server Status |
|---|---|---|
Up |
The RADIUS server is available. |
|
Down |
The RADIUS server is unavailable. |
The conditions for marking the RADIUS server status as Down are met. |
Force-up |
When no RADIUS server is available, the device selects the RADIUS server in Force-up status. |
The device marks the RADIUS server status as Force-up if the timer specified by dead-time expires. |
The RADIUS server status is initially marked as Up. After a RADIUS Access-Request packet is received and the conditions for marking the RADIUS server status as Down are met, the RADIUS server status transitions to Down. The RADIUS Access-Request packet that triggers the server status transition can be sent during user authentication or constructed by the administrator. For example, the RADIUS Access-Request packet can be a test packet sent when the test-aaa command is run or detection packet sent during automatic detection.
- Down to Force-up: The timer specified by dead-time starts after the device marks the RADIUS server status as Down. The timer indicates the duration for which the server status remains Down. After the timer expires, the device marks the RADIUS server status as Force-up. If a new user needs to be authenticated in RADIUS mode and no RADIUS server is available, the device attempts to re-establish a connection with a RADIUS server in Force-up status.
- Down to Up: After receiving packets from the RADIUS server, the device changes the RADIUS server status from Down to Up. For example, after automatic detection is configured, the device receives response packets from the RADIUS server.
Conditions for Marking the RADIUS Server Status as Down
Whether the status of a RADIUS server can be marked as Down depends on the following factors:
- Longest unresponsive interval of the RADIUS server (value of max-unresponsive-interval)
- Number of times the RADIUS Access-Request packet is sent
- Interval of sending the RADIUS Access-Request packet
- Interval of detecting the RADIUS server status
- Number of RADIUS server detection interval cycles
- Maximum number of consecutive unacknowledged packets in each detection interval
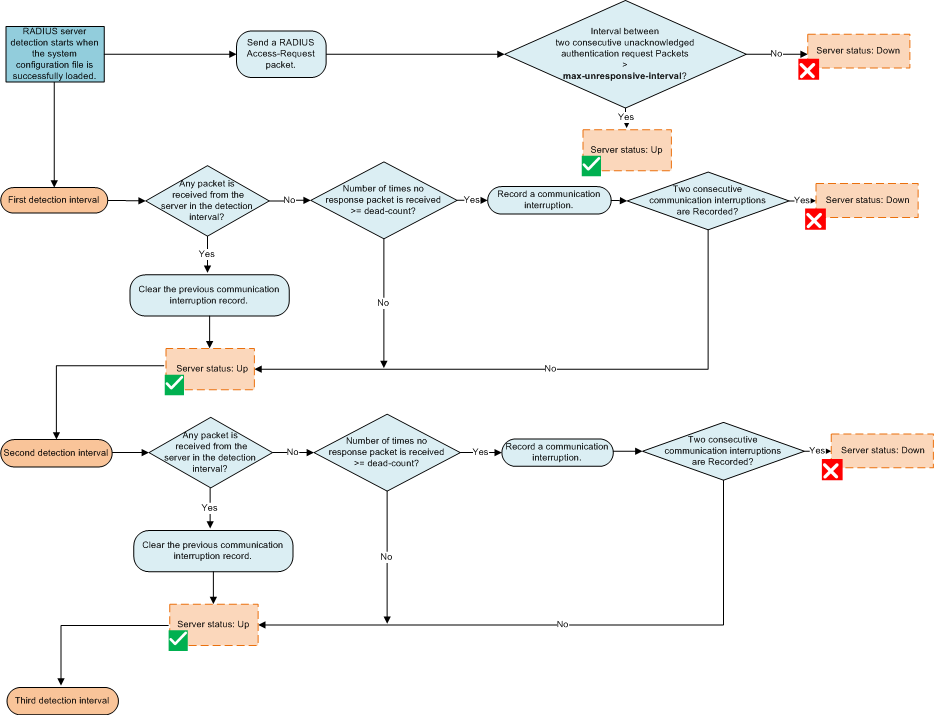
The device marks the RADIUS server status as Down during the RADIUS server status detection.
After the system starts, the RADIUS server status detection timer runs. If the device does not receive any packet from the RADIUS server after sending the first RADIUS Access-Request packet to the server and the condition that the number of times the device does not receive any packet from the server (n) is greater than or equal to the maximum number of consecutive unacknowledged packets (dead-count) is met in a detection interval, a communication interruption is recorded. If the device still does not receive any packet from the RADIUS server, the device marks the RADIUS server status as Down when recording the communication interruption for the same times as the detection interval cycles.

If the device does not record any communication interruption in a detection interval, all the previous communication interruption records are cleared.
The device marks the status of a RADIUS server as Down if no response is received from the server for a long period of time.
If the user access frequency is low, the device receives only a few RADIUS Access-Request packets from users, conditions for marking the RADIUS server status as Down during the RADIUS server status detection cannot be met, and the interval for sending two consecutive unacknowledged RADIUS Access-Request packets is greater than the value of max-unresponsive-interval, the device marks the RADIUS server status as Down. This mechanism ensures that users can obtain escape authorization.
If multiple servers are configured in the RADIUS server template, the overall status detection time is related to the number of servers and the server selection algorithm. If a user terminal uses the client software for authentication and the timeout period of the terminal client software is less than the summary of all the status detection time, the terminal client software may dial up repeatedly and cannot access the network. If the user escape function is configured, the summary of all the status detection time must be less than the timeout period of the terminal client software to ensure that escape rights can be added to the users.
The following table lists the related commands.
Command |
Description |
|---|---|
radius-server { dead-interval dead-interval | dead-count dead-count | detect-cycle detect-cycle } |
Configures conditions for marking the RADIUS server status as Down during the RADIUS server status detection.
|
radius-server max-unresponsive-interval interval |
Configures the longest unresponsive interval of the RADIUS server. The default value is 300 seconds. If the interval for sending two consecutive RADIUS Access-Request packets is greater than the value of max-unresponsive-interval, the device marks the RADIUS server status as Down. |
radius-server dead-time dead-time |
Configures the duration for which the RADIUS server status remains Down. dead-time: Specifies the duration for which the RADIUS server status remains Down after the server status is marked as Down. After the duration expires, the device marks the server status as Force-up. The default value is 5 minutes. |
Automatic Detection
After the RADIUS server status is marked as Down, you can configure the automatic detection function to test the RADIUS server reachability.
The automatic detection function needs to be manually enabled. The automatic server status detection function can be enabled only if the user name and password for automatic detection are configured in the RADIUS server template view on the device rather than on the RADIUS server. Authentication success is not mandatory. If the device can receive the authentication failure response packet, the RADIUS server is properly working and the device marks the RADIUS server status as Up. If the device cannot receive the response packet, the RADIUS server is unavailable and the device marks the RADIUS server status as Down.
Server Status |
Whether Automatic Detection Is Supported |
Time When an Automatic Detection Packet Is Sent |
Condition for Switching the Server Status |
|---|---|---|---|
Down |
Automatic detection is supported by default. |
An automatic detection packet is sent after the automatic detection period expires. |
If the device receives a response packet from the RADIUS server within the timeout period for detection packets, the device marks the RADIUS server status as Up; otherwise, the RADIUS server status remains Down. |
Up |
Automatic detection can be enabled using the radius-server detect-server up-server interval command. |
An automatic detection packet is sent after the automatic detection period expires. |
If the conditions for marking the RADIUS server status as Down are met, the device marks the RADIUS server status as Down; otherwise, the RADIUS server status remains Up. |
Force-up |
Automatic detection is supported by default. |
An automatic detection packet is sent immediately. |
If the device receives a packet from the RADIUS server within the timeout period, the device marks the RADIUS server status as Up; otherwise, the device marks the RADIUS server status as Down. |

On a large-scale network, you are not advised to enable automatic detection for RADIUS servers in Up status. This is because if automatic detection is enabled on multiple NAS devices, the RADIUS server periodically receives a large number of detection packets when processing RADIUS Access-Request packets source from users, which may deteriorate processing performance of the RADIUS server.
The following table lists commands related to automatic detection.
Command |
Description |
|---|---|
radius-server testuser username user-name password cipher password |
Enables the automatic detection function.
|
radius-server detect-server interval interval |
Specifies the automatic detection interval for RADIUS servers in Down status. The default value is 60 seconds. |
radius-server detect-server up-server interval interval |
Enables the automatic detection function for the RADIUS server in Up status and configures the automatic detection interval. The default value is 0 seconds; that is, the device does not automatically detect RADIUS servers in Up status. |
radius-server detect-server timeout time-value |
Specifies the timeout period for automatic detection packets. The default value is 3 seconds. |
Consecutive Processing After the RADIUS Server Status Is Marked as Down
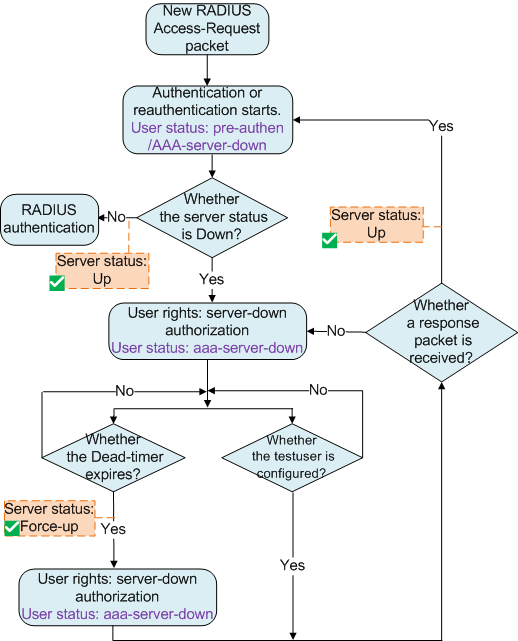
After the device marks the RADIUS server status as Down, you can configure the escape function to make users obtain escape authorization. After the device detects that the RADIUS server status reverts to Up, you can configure the reauthentication function to make users obtain authorization from the server through reauthentication, as shown in Figure 2.

For 802.1X authenticated users and MAC address authenticated users, after the RADIUS server status reverts to Up, users exist from escape authorization and are reauthenticated. For Portal authenticated users, after the RADIUS server status reverts to Up, users obtain pre-connection authorization and can be redirected to the Portal server for authentication only if the users attempt to access network resources.
After the testuser command is configured, the dead timer will not start.
The following table lists the commands for configuring the escape rights upon transition of the RADIUS server status to Down and configuring the reauthentication function, respectively.
Command |
Description |
|---|---|
authentication event authen-server-down action authorize { vlan vlan-id | service-scheme service-scheme-name | ucl-group ucl-group-name } [ response-fail ] |
Configures the escape function upon transition of the RADIUS server status to Down. |
authentication event authen-server-up action re-authen |
Configures the reauthentication function for users in escape status when the RADIUS server status reverts to Up. |