Example for Using Advanced ACLs to Control Access to the Specified Server in the Specified Time Range
Networking Requirements
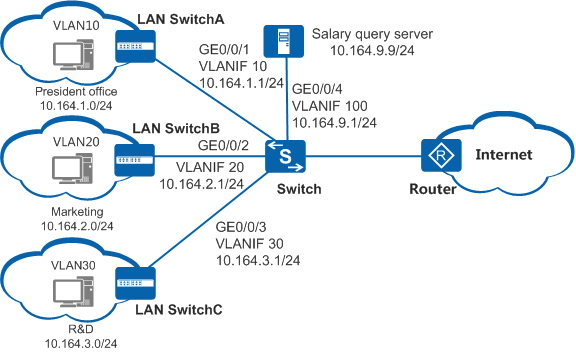
As shown in Figure 1, the departments of an enterprise are connected through the Switch. The R&D and marketing departments cannot access the salary query server at 10.164.9.9 in work hours (08:00 to 17:30), whereas the president office can access the server at anytime.
Configuration Roadmap
- Configure the time range, advanced ACL, and ACL-based traffic classifier to filter packets from users to the server in the specified time range. In this way, you can restrict the access of different users to the server in the specified time range.
- Configure a traffic behavior to discard the packets matching the ACL.
- Configure and apply a traffic policy to make the ACL and traffic behavior take effect.
Procedure
- Add interfaces to VLANs and assign IP addresses to the
VLANIF interfaces.
# Add GE0/0/1 throughGE0/0/3 to VLANs 10, 20, and 30, respectively, add GE0/0/4 to VLAN 100, and assign IP addresses to these VLANIF interfaces. The configurations on GE0/0/1 and VLANIF 10 are used as an example here. The configurations on GE0/0/2, GE0/0/3, and GE0/0/4 are similar to those on GE0/0/1, and the configurations on VLANIF 20, VLANIF 30, and VLANIF 100 are similar to those on VLANIF 10.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] vlan batch 10 20 30 100 [Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] port link-type trunk [Switch-GigabitEthernet0/0/1] port trunk allow-pass vlan 10 [Switch-GigabitEthernet0/0/1] quit [Switch] interface vlanif 10 [Switch-Vlanif10] ip address 10.164.1.1 255.255.255.0 [Switch-Vlanif10] quit
- Configure a time range.
# Configure the time range from 8:00 to 17:30.
[Switch] time-range satime 8:00 to 17:30 working-day - Configure ACLs.
# Configure an ACL for the marketing department to access the salary query server.
[Switch] acl 3002 [Switch-acl-adv-3002] rule deny ip source 10.164.2.0 0.0.0.255 destination 10.164.9.9 0.0.0.0 time-range satime [Switch-acl-adv-3002] quit
# Configure an ACL for the R&D department to access the salary query server.
[Switch] acl 3003 [Switch-acl-adv-3003] rule deny ip source 10.164.3.0 0.0.0.255 destination 10.164.9.9 0.0.0.0 time-range satime [Switch-acl-adv-3003] quit
- Configure ACL-based traffic classifiers.
# Configure the traffic classifier c_market to classify the packets that match ACL 3002.
[Switch] traffic classifier c_market [Switch-classifier-c_market] if-match acl 3002 [Switch-classifier-c_market] quit
# Configure the traffic classifier c_rd to classify the packets that match ACL 3003.
[Switch] traffic classifier c_rd [Switch-classifier-c_rd] if-match acl 3003 [Switch-classifier-c_rd] quit
- Configure traffic behaviors.
# Configure the traffic behavior b_market to reject packets.
[Switch] traffic behavior b_market [Switch-behavior-b_market] deny [Switch-behavior-b_market] quit
# Configure the traffic behavior b_rd to reject packets.
[Switch] traffic behavior b_rd [Switch-behavior-b_rd] deny [Switch-behavior-b_rd] quit
- Configure traffic policies.
# Configure the traffic policy p_market, and associate the traffic classifier c_market and the traffic behavior b_market with the traffic policy.
[Switch] traffic policy p_market [Switch-trafficpolicy-p_market] classifier c_market behavior b_market [Switch-trafficpolicy-p_market] quit
# Configure the traffic policy p_rd, and associate the traffic classifier c_rd and the traffic behavior b_rd with the traffic policy.
[Switch] traffic policy p_rd [Switch-trafficpolicy-p_rd] classifier c_rd behavior b_rd [Switch-trafficpolicy-p_rd] quit
- Apply the traffic policy.
# Packets from the marketing department are received by GE0/0/2, so apply the traffic policy p_market to the inbound direction of GE0/0/2.
[Switch] interface gigabitethernet 0/0/2 [Switch-GigabitEthernet0/0/2] traffic-policy p_market inbound [Switch-GigabitEthernet0/0/2] quit
# Packets from the R&D department are received by GE0/0/3, so apply the traffic policy p_rd to the inbound direction of GE0/0/3.
[Switch] interface gigabitethernet 0/0/3 [Switch-GigabitEthernet0/0/3] traffic-policy p_rd inbound [Switch-GigabitEthernet0/0/3] quit
- Verify the configuration.
# Check the configuration of ACL rules.
[Switch] display acl all Total nonempty ACL number is 2 Advanced ACL 3002, 1 rule Acl's step is 5 rule 5 deny ip source 10.164.2.0 0.0.0.255 destination 10.164.9.9 0 time-range satime (Active) Advanced ACL 3003, 1 rule Acl's step is 5 rule 5 deny ip source 10.164.3.0 0.0.0.255 destination 10.164.9.9 0 time-range satime (Active)
# Check the configuration of traffic classifiers.
[Switch] display traffic classifier user-defined User Defined Classifier Information: Classifier: c_market Operator: OR Rule(s) : if-match acl 3002 Classifier: c_rd Operator: OR Rule(s) : if-match acl 3003 Total classifier number is 2# Check the configuration of traffic policies.
[Switch] display traffic policy user-defined User Defined Traffic Policy Information: Policy: p_market Classifier: c_market Operator: OR Behavior: b_market Deny Policy: p_rd Classifier: c_rd Operator: OR Behavior: b_rd Deny Total policy number is 2# Check the traffic policy use records.
[Switch] display traffic-policy applied-record # ------------------------------------------------- Policy Name: p_market Policy Index: 0 Classifier:c_market Behavior:b_market ------------------------------------------------- *interface GigabitEthernet0/0/2 traffic-policy p_market inbound slot 0 : success ------------------------------------------------- Policy total applied times: 1. # ------------------------------------------------- Policy Name: p_rd Policy Index: 1 Classifier:c_rd Behavior:b_rd ------------------------------------------------- *interface GigabitEthernet0/0/3 traffic-policy p_rd inbound slot 0 : success ------------------------------------------------- Policy total applied times: 1. #
# The R&D and marketing departments cannot access the salary query server during work hours (08:00 to 17:30).
Configuration Files
Switch configuration file
# sysname Switch # vlan batch 10 20 30 100 # time-range satime 08:00 to 17:30 working-day # acl number 3002 rule 5 deny ip source 10.164.2.0 0.0.0.255 destination 10.164.9.9 0 time-range satime acl number 3003 rule 5 deny ip source 10.164.3.0 0.0.0.255 destination 10.164.9.9 0 time-range satime # traffic classifier c_market operator or if-match acl 3002 traffic classifier c_rd operator or if-match acl 3003 # traffic behavior b_market deny traffic behavior b_rd deny # traffic policy p_market match-order config classifier c_market behavior b_market traffic policy p_rd match-order config classifier c_rd behavior b_rd # interface Vlanif10 ip address 10.164.1.1 255.255.255.0 # interface Vlanif20 ip address 10.164.2.1 255.255.255.0 # interface Vlanif30 ip address 10.164.3.1 255.255.255.0 # interface Vlanif100 ip address 10.164.9.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 10 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 20 traffic-policy p_market inbound # interface GigabitEthernet0/0/3 port link-type trunk port trunk allow-pass vlan 30 traffic-policy p_rd inbound # interface GigabitEthernet0/0/4 port link-type trunk port trunk allow-pass vlan 100 # return