Example for Using Advanced ACLs to Implement Unidirectional Access Control
Networking Requirements
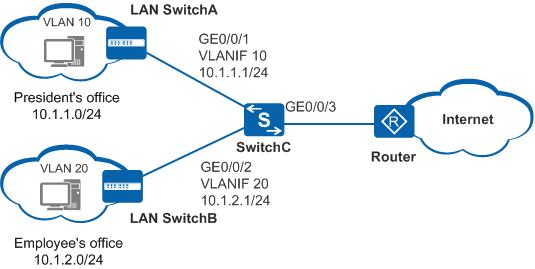
As shown in Figure 1, different offices of an enterprise are connected through SwitchC. To facilitate network management, the administrator allocates the IP addresses on two network segments to the president's office and employee's office, respectively. In addition, the administrator adds the two offices to different VLANs for broadcast domain isolation. The president's office must be able to access the employee's office, but the employee's office is not allowed to access the president's office to protect the enterprise's confidential information.
Configuration Roadmap
- Configure an advanced ACL and ACL-based traffic classifier to restrict ICMP and TCP services so that unidirectional access from the president's office to the employee's office can be implemented.
- TCP service: permits SYN and ACK packets from the employee's office to the president's office, that is, responds to TCP connections initiated by the president's office; denies SYN request packets from the employee's office to the president's office to prevent the employee's office from initiating TCP connections.
- ICMP service: denies echo request packets from the employee's office to the president's office to prevent the employee's office from initiating ping connectivity tests.

Unidirectional access cannot be implemented for UDP services.
- Configure a traffic behavior so that packets matching ACL rules are forwarded based on the original policy.
- Configure and apply a traffic policy to make the ACL and traffic behavior take effect.
Procedure
- Configure IP addresses for interfaces and add the interfaces to VLANs.
# Create VLAN 10 and VLAN 20.
<HUAWEI> system-view [HUAWEI] sysname SwitchC [SwitchC] vlan batch 10 20
# Configure GE0/0/1 and GE0/0/2 on the SwitchC as trunk interfaces and add them to VLAN 10 and VLAN 20, respectively.
[SwitchC] interface gigabitethernet 0/0/1 [SwitchC-GigabitEthernet0/0/1] port link-type trunk [SwitchC-GigabitEthernet0/0/1] port trunk allow-pass vlan 10 [SwitchC-GigabitEthernet0/0/1] quit [SwitchC] interface gigabitethernet 0/0/2 [SwitchC-GigabitEthernet0/0/2] port link-type trunk [SwitchC-GigabitEthernet0/0/2] port trunk allow-pass vlan 20 [SwitchC-GigabitEthernet0/0/2] quit
# Create VLANIF 10 and VLANIF 20, and assign IP addresses to them.
[SwitchC] interface vlanif 10 [SwitchC-Vlanif10] ip address 10.1.1.1 24 [SwitchC-Vlanif10] quit [SwitchC] interface vlanif 20 [SwitchC-Vlanif20] ip address 10.1.2.1 24 [SwitchC-Vlanif20] quit
- Configure an ACL.
# Create advanced ACL 3001 and configure ACL rules.
[SwitchC] acl 3001 [SwitchC-acl-adv-3001] rule permit tcp source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 tcp-flag syn ack [SwitchC-acl-adv-3001] rule deny tcp source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 tcp-flag syn [SwitchC-acl-adv-3001] rule deny icmp source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 icmp-type echo [SwitchC-acl-adv-3001] quit
- Configure a traffic classifier based on the advanced ACL.
# Configure the traffic classifier tc1 to classify packets that match ACL 3001.
[SwitchC] traffic classifier tc1 [SwitchC-classifier-tc1] if-match acl 3001 [SwitchC-classifier-tc1] quit
- Configure a traffic behavior.
# Configure the traffic behavior tb1.
[SwitchC] traffic behavior tb1 [SwitchC-behavior-tb1] permit [SwitchC-behavior-tb1] quit
- Configure a traffic policy.
# Define a traffic policy, and associate the traffic classifier and traffic behavior with the traffic policy.
[SwitchC] traffic policy tp1 [SwitchC-trafficpolicy-tp1] classifier tc1 behavior tb1 [SwitchC-trafficpolicy-tp1] quit
- Apply the traffic policy to an interface.
# Apply the traffic policy in the inbound direction of GE0/0/2.
[SwitchC] interface gigabitethernet 0/0/2 [SwitchC-GigabitEthernet0/0/2] traffic-policy tp1 inbound [SwitchC-GigabitEthernet0/0/2] quit
- Verify the configuration.
# Check the ACL configuration.
[SwitchC] display acl 3001 Advanced ACL 3001, 3 rules Acl's step is 5 rule 5 permit tcp source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 tcp-flag ack syn rule 10 deny tcp source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 tcp-flag syn rule 15 deny icmp source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 icmp-type echo# Check the traffic classifier configuration.
[SwitchC] display traffic classifier user-defined User Defined Classifier Information: Classifier: tc1 Operator: OR Rule(s) : if-match acl 3001 Total classifier number is 1# Check the traffic policy configuration.
[SwitchC] display traffic policy user-defined tp1 User Defined Traffic Policy Information: Policy: tp1 Classifier: tc1 Operator: OR Behavior: tb1 Permit# The president's office can access the employee's office, but the employee's office cannot access the president's office.
Configuration Files
SwitchC configuration file
# sysname SwitchC # vlan batch 10 20 # acl number 3001 rule 5 permit tcp source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 tcp-flag ack syn rule 10 deny tcp source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 tcp-flag syn rule 15 deny icmp source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 icmp-type echo # traffic classifier tc1 operator or if-match acl 3001 # traffic behavior tb1 permit # traffic policy tp1 match-order config classifier tc1 behavior tb1 # interface Vlanif10 ip address 10.1.1.1 255.255.255.0 # interface Vlanif20 ip address 10.1.2.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 10 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 20 traffic-policy tp1 inbound # return