Example for Using User ACLs to Control Network Access Rights of Enterprise's Internal Users Based on Groups
Networking Requirements
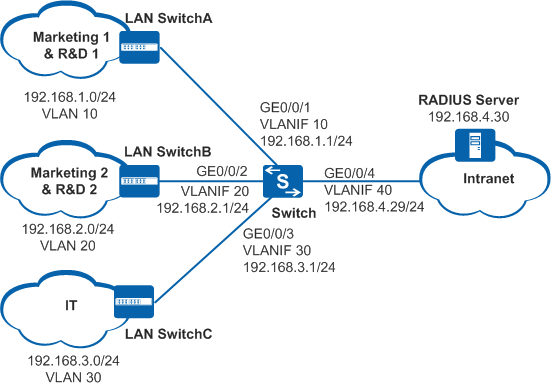
As shown in Figure 1, a large number of terminals in an office area of an enterprise connect to the enterprise internal network through the switch. Some departments have multiple branches in different locations, so the terminals of the same department cannot use the IP addresses of the same network segment.
The administrator requires that the switch authenticate the terminals (including computers and printers) of every department, to prevent unauthorized access. In addition, due to the differentiated responsibilities, the administrator wants to grant different network access rights to the users of different department, avoiding secret information leak caused by mutual access between users.
- The marketing department cannot access the IT department.
- The R&D department cannot access the IT department.
Configuration Roadmap
The configuration roadmap is as follows:
Create and configure a RADIUS server template, an AAA scheme, and an authentication domain. Bind the RADIUS server template and AAA scheme to the authentication domain, ensuring that the Switch and RADIUS server can communicate with each other and terminals can be authenticated by the RADIUS server.
Some terminals cannot have the 802.1X client installed, for example, printers. To ensure authentication for all types of terminals, configure MAC address authentication and 802.1X authentication, and configure MAC address authentication to be used first.
Each department has a large number of terminals and the terminals of some departments the same department are located on different network segments. The workload will be huge for configuring a network access policy for the terminals one by one. Therefore, configure a UCL group to classify the terminals into different types, and associate a user ACL with the UCL group so that the terminals in each group can share the ACL rules. The workload of administrator is reduced, and ACL resource use efficiency on the device is improved.
Create service schemes and apply the service schemes to the UCL group to control the network access right of each department based on groups.

This example only provides the configurations on the Switch. The configurations on the LAN switch and RADIUS server are not provided here.
Procedure
- Configure VLANs and IP addresses for interfaces to ensure network connections.
# Create VLAN 10, VLAN 20, VLAN 30, and VLAN 40.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] vlan batch 10 20 30 40
# Configure GE0/0/1, GE0/0/2, GE0/0/3, and GE0/0/4 on the Switch as trunk interfaces, and add the interfaces to VLAN 10, VLAN 20, VLAN 30, and VLAN 40. Take the configurations on GE0/0/1 as an example. The configurations on GE0/0/2, GE0/0/3, and GE0/0/4 are similar to those on GE0/0/1, and are not mentioned here.
[Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] port link-type trunk [Switch-GigabitEthernet0/0/1] port trunk allow-pass vlan 10 [Switch-GigabitEthernet0/0/1] quit
# Create VLANIF 10, VLANIF 20, VLANIF 30, and VLANIF 40, and assign IP addresses to these VLANIF interfaces so that reachable routes can be set up between the terminals, Switch, and enterprise internal servers.
[Switch] interface vlanif 10 [Switch-Vlanif10] ip address 192.168.1.1 24 [Switch-Vlanif10] quit [Switch] interface vlanif 20 [Switch-Vlanif20] ip address 192.168.2.1 24 [Switch-Vlanif20] quit [Switch] interface vlanif 30 [Switch-Vlanif30] ip address 192.168.3.1 24 [Switch-Vlanif30] quit [Switch] interface vlanif 40 [Switch-Vlanif40] ip address 192.168.4.29 24 [Switch-Vlanif40] quit
- Create and configure a RADIUS server template, an AAA scheme, and an authentication domain.
# Create and configure the RADIUS server template rd1.
[Switch] radius-server template rd1 [Switch-radius-rd1] radius-server authentication 192.168.4.30 1812 [Switch-radius-rd1] radius-server shared-key cipher huawei@2017 [Switch-radius-rd1] radius-server retransmit 2 [Switch-radius-rd1] quit
# Create the AAA scheme abc and set the authentication mode to RADIUS.
[Switch] aaa [Switch-aaa] authentication-scheme abc [Switch-aaa-authen-abc] authentication-mode radius [Switch-aaa-authen-abc] quit
# Create the authentication domain abc11, and bind the AAA scheme abc and the RADIUS server template rd1 to the authentication domain.
[Switch-aaa] domain abc11 [Switch-aaa-domain-abc11] authentication-scheme abc [Switch-aaa-domain-abc11] radius-server rd1 [Switch-aaa-domain-abc11] quit [Switch-aaa] quit
- Configure MAC address authentication and 802.1X authentication.
# Set the NAC mode to unified mode.

By default, the NAC mode is unified mode, so this step can be skipped.
After the common mode and unified mode are switched, you must restart the device to make each function take effect in the new mode.
[Switch] authentication unified-mode
# Configure a MAC access profile.[Switch] mac-access-profile name m1 [Switch-mac-access-profile-m1] mac-authen username fixed A-123 password cipher Huawei123 [Switch-mac-access-profile-m1] quit
# Configure an 802.1X access profile.
By default, an 802.1X access profile uses the EAP authentication mode. Ensure that the RADIUS server supports EAP; otherwise, the server cannot process 802.1X authentication request packets.
[Switch] dot1x-access-profile name d1 [Switch-dot1x-access-profile-d1] quit
# Configure an authentication profile.[Switch] authentication-profile name p1 [Switch-authen-profile-p1] mac-access-profile m1 [Switch-authen-profile-p1] dot1x-access-profile d1 [Switch-authen-profile-p1] authentication dot1x-mac-bypass [Switch-authen-profile-p1] quit
# Enable MAC address authentication and 802.1X authentication on GE0/0/1, GE0/0/2, and GE0/0/3.
[Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] authentication-profile p1 [Switch-GigabitEthernet0/0/1] quit [Switch] interface gigabitethernet 0/0/2 [Switch-GigabitEthernet0/0/2] authentication-profile p1 [Switch-GigabitEthernet0/0/2] quit [Switch] interface gigabitethernet 0/0/3 [Switch-GigabitEthernet0/0/3] authentication-profile p1 [Switch-GigabitEthernet0/0/3] quit
- Create a UCL group, associate the user ACL with the UCL group, and apply the user ACL to filter packets.
# Create UCL groups group_m and group_r. Add the marketing department to group_m and R&D department to group_r.
[Switch] ucl-group 1 name group_m [Switch] ucl-group 2 name group_r

Information about user groups of the marketing and R&D departments must have been configured on the RADIUS server.
# Create user ACL 6001 and configure ACL rules. Configure rule 5 to prevent the marketing department from accessing the IT department; configure rule 10 to prevent the R&D department from accessing the IT department.
[Switch] acl 6001 [Switch-acl-ucl-6001] rule 5 deny ip source ucl-group name group_m destination 192.168.3.0 0.0.0.255 [Switch-acl-ucl-6001] rule 10 deny ip source ucl-group name group_r destination 192.168.3.0 0.0.0.255 [Switch-acl-ucl-6001] quit
# Configure user ACL-based packet filtering to make the user ACL take effect.
[Switch] traffic-filter inbound acl 6001
- Configure service schemes service-scheme1 and service-scheme2, and apply the service schemes to UCL groups group_m and group_r to control the network access right of each department based on groups.
[Switch] aaa [Switch-aaa] service-scheme service-scheme1 [Switch-aaa-service-service-scheme1] ucl-group name group_m [Switch-aaa-service-service-scheme1] quit [Switch-aaa] service-scheme service-scheme2 [Switch-aaa-service-service-scheme2] ucl-group name group_r [Switch-aaa-service-service-scheme2] quit [Switch-aaa] quit [Switch] quit

After the preceding steps are complete, configure the RADIUS server to associate the service schemes with users.
- Verify the configuration.
# Run the display acl all command to view information about the user ACL.
<Switch> display acl all Total nonempty ACL number is 1 Ucl-group ACL 6001, 2 rules Acl's step is 5 rule 5 deny ip source ucl-group name group_m destination 192.168.3.0 0.0.0.255 rule 10 deny ip source ucl-group name group_r destination 192.168.3.0 0.0.0.255# Run the display ucl-group all command to view information about all UCL groups.
<Switch> display ucl-group all ID UCL group name -------------------------------------------------------------------------------- 1 group_m 2 group_r -------------------------------------------------------------------------------- Total : 2
# Run the display dot1x command to check the 802.1X authentication configuration. The command output (802.1x protocol is Enabled) shows that the 802.1X authentication has been enabled on the interface GE0/0/1, GE0/0/2, and GE0/0/3.
# Run the display mac-authen command to check the MAC address authentication configuration. The command output (MAC address authentication is enabled) shows that MAC address authentication has been enabled on the interface GE0/0/1, GE0/0/2, and GE0/0/3.
# The marketing department cannot access the IT department and the R&D department cannot access the IT department.
Configuration Files
Switch configuration file
# sysname Switch # vlan batch 10 20 30 40 # authentication-profile name p1 dot1x-access-profile d1 mac-access-profile m1 authentication dot1x-mac-bypass ucl-group 1 name group_m ucl-group 2 name group_r # radius-server template rd1 radius-server shared-key cipher %^%#zH_B2{mN=177WZ2z+G|5)c'OKD[VaPNYP4>&6uC~%^%# radius-server authentication 192.168.4.30 1812 weight 80 radius-server retransmit 2 # acl number 6001 rule 5 deny ip source ucl-group name group_m destination 192.168.3.0 0.0.0.255 rule 10 deny ip source ucl-group name group_r destination 192.168.3.0 0.0.0.255 # aaa authentication-scheme abc authentication-mode radius service-scheme service-scheme1 ucl-group name group_m service-scheme service-scheme2 ucl-group name group_r domain abc11 authentication-scheme abc radius-server rd1 # interface Vlanif10 ip address 192.168.1.1 255.255.255.0 # interface Vlanif20 ip address 192.168.2.1 255.255.255.0 # interface Vlanif30 ip address 192.168.3.1 255.255.255.0 # interface Vlanif40 ip address 192.168.4.29 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 10 authentication-profile p1 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 20 authentication-profile p1 # interface GigabitEthernet0/0/3 port link-type trunk port trunk allow-pass vlan 30 authentication-profile p1 # interface GigabitEthernet0/0/4 port link-type trunk port trunk allow-pass vlan 40 # traffic-filter inbound acl 6001 # dot1x-access-profile name d1 # mac-access-profile name m1 mac-authen username fixed A-123 password cipher %^%#(!XnF'#X^Sc=[&,fH38!OKNNEjez>NO`Z*NJK*s4%^%# # return