Overview of Network Deception Technology
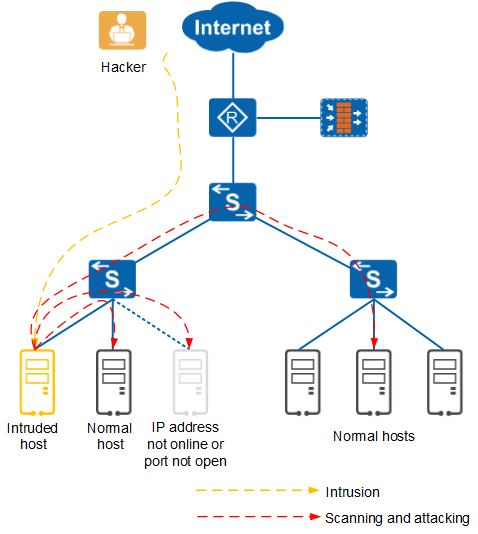
After a hacker intrudes on the network shown in Figure 1, the hacker first scans IP addresses and service ports on the network to search for attack or spreading targets, and then uses the system or software vulnerabilities or brute force cracking measures to attack the target host. Network deception technology detects such scanning behavior on the network, and lures suspicious traffic to a Decoy for in-depth interaction and detection, protecting the service network from the hacker.