Example for Configuring IGMP Snooping SSM Mapping in a VLAN
Networking Requirements
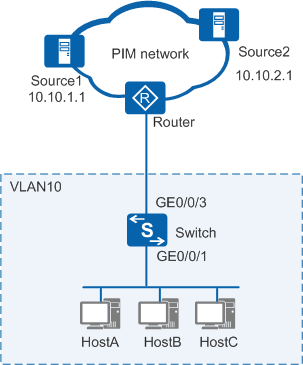
As shown in Figure 1, the router connects to user hosts through a Layer 2 switch. The router runs IGMPv3 and uses the any-source multicast (ASM) and source-specific multicast (SSM) models to provide multicast services. HostA, HostB, and HostC run IGMPv2 and do not support IGMPv3. Multicast sources Source1 and Source2 send multicast data to the multicast group 225.1.1.1. However, the hosts want to receive multicast data sent from Source1 only.
Configuration Roadmap
To meet the preceding requirements, configure SSM mapping on the switch. The configuration roadmap is as follows:
Create a VLAN and add interfaces to the VLAN.
Enable IGMP snooping globally and in the VLAN.
Configure an IGMP snooping SSM policy to add the ASM group address to the SSM group address range.
Configure SSM mapping to allow the users to receive only multicast data sent from the specified source.
Procedure
- Create a VLAN and add interfaces to the VLAN.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] vlan 10 [Switch-vlan10] quit [Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] port link-type hybrid [Switch-GigabitEthernet0/0/1] port hybrid pvid vlan 10 [Switch-GigabitEthernet0/0/1] port hybrid untagged vlan 10 [Switch-GigabitEthernet0/0/1] quit [Switch] interface gigabitethernet 0/0/3 [Switch-GigabitEthernet0/0/3] port link-type hybrid [Switch-GigabitEthernet0/0/3] port hybrid pvid vlan 10 [Switch-GigabitEthernet0/0/3] port hybrid untagged vlan 10 [Switch-GigabitEthernet0/0/3] quit
- Enable IGMP snooping.
# Enable IGMP snooping globally.
[Switch] igmp-snooping enable# Enable IGMP snooping in VLAN 10.
[Switch] vlan 10 [Switch-vlan10] igmp-snooping enable [Switch-vlan10] quit
- Configure an IGMP snooping SSM policy.
# Create an ACL, and configure a rule that allows hosts to receive data of multicast group 225.1.1.1.
[Switch] acl number 2008 [Switch-acl-basic-2008] rule 5 permit source 225.1.1.1 0 [Switch-acl-basic-2008] quit
# Apply the SSM mapping policy to the VLAN to include group 225.1.1.1 in the SSM group range.
[Switch] vlan 10 [Switch-vlan10] igmp-snooping ssm-policy 2008
- Enable SSM mapping.
# Set the IGMP snooping version to V3, enable SSM mapping, and configure a mapping between group address 225.1.1.1 and source address 10.10.1.1.
[Switch-vlan10] igmp-snooping version 3 [Switch-vlan10] igmp-snooping ssm-mapping enable [Switch-vlan10] igmp-snooping ssm-mapping 225.1.1.1 32 10.10.1.1 [Switch-vlan10] quit
- Verify the configuration.
# Check the IGMP snooping configuration in the VLAN.
[Switch] display igmp-snooping vlan configuration IGMP Snooping Configuration for VLAN 10 igmp-snooping enable igmp-snooping version 3 igmp-snooping ssm-mapping enable igmp-snooping ssm-policy 2008 igmp-snooping ssm-mapping 225.1.1.1 255.255.255.255 10.10.1.1An SSM mapping policy has been configured in VLAN 10.
# Check the Layer 2 multicast forwarding table.
[Switch] display l2-multicast forwarding-table vlan 10 VLAN ID : 10, Forwarding Mode : IP Total Group(s) : 2 ---------------------------------------------------------------------------- (Source, Group) Interface Out-Vlan ---------------------------------------------------------------------------- Router-port GigabitEthernet0/0/3 10 (10.10.1.1, 225.1.1.1) GigabitEthernet0/0/1 10 GigabitEthernet0/0/3 10 (10.10.2.1, 225.1.1.1) Stream 10 GigabitEthernet0/0/3 10 ----------------------------------------------------------------------------
The command output shows that a mapping entry (10.10.1.1, 225.1.1.1) has been generated on the switch. The mapping entry indicates that the data is sent from Source1.

The preceding stream entries are triggered by unknown streams, which are generated because user hosts do not require data from multicast source 10.10.2.1.
Configuration Files
Switch configuration file
# sysname Switch # vlan batch 10 # igmp-snooping enable # acl number 2008 rule 5 permit source 225.1.1.1 0 # vlan 10 igmp-snooping enable igmp-snooping ssm-mapping enable igmp-snooping version 3 igmp-snooping ssm-policy 2008 igmp-snooping ssm-mapping 225.1.1.1 255.255.255.255 10.10.1.1 # interface GigabitEthernet0/0/1 port link-type hybrid port hybrid pvid vlan 10 port hybrid untagged vlan 10 # interface GigabitEthernet0/0/3 port link-type hybrid port hybrid pvid vlan 10 port hybrid untagged vlan 10 # return