Example for Configuring OSPFv3 IPSec
Networking Requirements
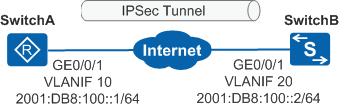
In Figure 1, SwitchA and SwitchB are running OSPFv3 and connected through the Internet. If no authentication mechanism is configured, OSPFv3 packets transmitted between SwitchA and SwitchB may be tampered with or forged by network attackers, interrupting the neighbor relationship between SwitchA and SwitchB or leading to incorrect routes. To prevent this problem, an IPSec tunnel can be established between SwitchA and SwitchB to protect OSPFv3 packets during transmission.
Configuration Roadmap
Configure VLANs and IP addresses for interfaces.
Configure basic OSPFv3 functions on SwitchA and SwitchB.
Create an IPSec proposal and configure the authentication algorithm, encryption algorithm, and encapsulation mode for the IPSec proposal.
Configure an SA.
Apply the SA to an OSPFv3 process to protect OSPFv3 packets between SwitchA and SwitchB.
Procedure
- Create VLANs and add interfaces to the VLANs.
# Configure SwitchA.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] vlan 10 [SwitchA-vlan10] quit [SwitchA] interface gigabitethernet0/0/1 [SwitchA-GigabitEthernet0/0/1] port link-type trunk [SwitchA-GigabitEthernet0/0/1] port trunk allow-pass vlan 10 [SwitchA-GigabitEthernet0/0/1] quit
# Configure SwitchB.
<HUAWEI> system-view [HUAWEI] sysname SwitchB [SwitchB] vlan 20 [SwitchB-vlan20] quit [SwitchB] interface gigabitethernet0/0/1 [SwitchB-GigabitEthernet0/0/1] port link-type trunk [SwitchB-GigabitEthernet0/0/1] port trunk allow-pass vlan 20 [SwitchB-GigabitEthernet0/0/1] quit
Configure OSPFv3 on SwitchA and SwitchB.
# Configure SwitchA.
[SwitchA] ospfv3 1 [SwitchA-ospfv3-1] router-id 1.1.1.1 [SwitchA-ospfv3-1] quit
# Configure SwitchB.
[SwitchB] ospfv3 1 [SwitchB-ospfv3-1] router-id 2.2.2.2 [SwitchB-ospfv3-1] quit
Configure IPv6 addresses and enable OSPFv3 on interfaces.
# Configure SwitchA.
[SwitchA] ipv6 [SwitchA] interface vlanif 10 [SwitchA-Vlanif10] ipv6 enable [SwitchA-Vlanif10] ipv6 address 2001:DB8:100::1 64 [SwitchA-Vlanif10] ospfv3 1 area 1 [SwitchA-Vlanif10] quit
# Configure SwitchB.
[SwitchB] ipv6 [SwitchB] interface vlanif 20 [SwitchB-Vlanif20] ipv6 enable [SwitchB-Vlanif20] ipv6 address 2001:DB8:100::2 64 [SwitchB-Vlanif20] ospfv3 1 area 1 [SwitchB-Vlanif20] quit
Configure an IPSec proposal on SwitchA and SwitchB.
# Configure an IPSec proposal on SwitchA.
[SwitchA] ipsec proposal proposal1 [SwitchA-ipsec-proposal-proposal1] encapsulation-mode transport [SwitchA-ipsec-proposal-proposal1] transform esp [SwitchA-ipsec-proposal-proposal1] esp authentication-algorithm sha2-256 [SwitchA-ipsec-proposal-proposal1] undo esp encryption-algorithm [SwitchA-ipsec-proposal-proposal1] quit
# Configure an IPSec proposal on SwitchB.[SwitchB] ipsec proposal proposal2 [SwitchB-ipsec-proposal-proposal2] encapsulation-mode transport [SwitchB-ipsec-proposal-proposal2] transform esp [SwitchB-ipsec-proposal-proposal2] esp authentication-algorithm sha2-256 [SwitchB-ipsec-proposal-proposal2] undo esp encryption-algorithm [SwitchB-ipsec-proposal-proposal2] quit
# Run the display ipsec proposal command on SwitchA and SwitchB to check configurations. The following uses the command output on SwitchA as an example.
[SwitchA] display ipsec proposal Total IP security proposal number: 1 IP security proposal name: proposal1 encapsulation mode: transport transform: esp-new ESP protocol: authentication SHA2-HMAC-256, not use encryptionConfigure an IPSec SA on SwitchA and SwitchB and apply it to the specified IPsec proposal.
# Configure an IPSec SA on SwitchA and apply it to the specified IPsec proposal.
[SwitchA] ipsec sa sa1 [SwitchA-ipsec-sa-sa1] proposal proposal1 [SwitchA-ipsec-sa-sa1] quit
# Configure an IPSec SA on SwitchB and apply it to the specified IPsec proposal.
[SwitchB] ipsec sa sa2 [SwitchB-ipsec-sa-sa2] proposal proposal2 [SwitchB-ipsec-sa-sa2] quit
Configure SPIs and authentication keys in the string format on SwitchA and SwitchB.
# Configure SPIs and authentication keys in the string format on SwitchA.
[SwitchA] ipsec sa sa1 [SwitchA-ipsec-sa-sa1] sa spi inbound esp 12345 [SwitchA-ipsec-sa-sa1] sa spi outbound esp 12345 [SwitchA-ipsec-sa-sa1] sa string-key inbound esp Huawei-123 [SwitchA-ipsec-sa-sa1] sa string-key outbound esp Huawei-123 [SwitchA-ipsec-sa-sa1] quit
# Configure SPIs and authentication keys in the string format on SwitchB.
[SwitchB] ipsec sa sa2 [SwitchB-ipsec-sa-sa2] sa spi outbound esp 12345 [SwitchB-ipsec-sa-sa2] sa spi inbound esp 12345 [SwitchB-ipsec-sa-sa2] sa string-key outbound esp Huawei-123 [SwitchB-ipsec-sa-sa2] sa string-key inbound esp Huawei-123 [SwitchB-ipsec-sa-sa2] quit
Configure SAs for an OSPFv3 process.
# Apply the SA to an OSPFv3 process on SwitchA.
[SwitchA] ospfv3 1 [SwitchA-ospfv3-1] ipsec sa sa1 [SwitchA-ospfv3-1] quit
# Apply the SA to an OSPFv3 process on SwitchB.
[SwitchB] ospfv3 1 [SwitchB-ospfv3-1] ipsec sa sa2 [SwitchB-ospfv3-1] quit
Verify the configuration.
Run the display ipsec sa command to check the SA configuration. The following uses the command output on SwitchA as an example.
[SwitchA] display ipsec sa IP security association name: sa1 Number of references: 1 proposal name: proposal1 inbound AH setting: AH spi: AH string-key: AH authentication hex key: inbound ESP setting: ESP spi: 12345 (0x3039) ESP string-key: %^%#Rmi-NNXDj%&Uw/$;+eD@yIws7^t]!;PG}QX2QOy-%^%# ESP encryption hex key: ESP authentication hex key: outbound AH setting: AH spi: AH string-key: AH authentication hex key: outbound ESP setting: ESP spi: 12345 (0x3039) ESP string-key: %^%#5rV8K(\j},rE.+EezM>=SI$vBQn7z=*8aY5bqM&J%^%# ESP encryption hex key: ESP authentication hex key:# Run the display ipsec statistics command to check the IPSec packet statistics. The following uses the command output on SwitchA as an example.
[SwitchA] display ipsec statistics IPv6 security packet statistics: input/output security packets: 184/51 input/output security bytes: 13216/1836 input/output dropped security packets: 0/0 dropped security packet detail: memory process problem: 0 can't find SA: 0 queue is full: 0 authentication is failed: 0 wrong length: 0 replay packet: 0 too long packet: 0 invalid SA: 0 policy deny: 0 the normal packet statistics: input/output dropped normal packets: 0/0 IPv4 security packet statistics: input/output security packets: 0/0 input/output security bytes: 0/0 input/output dropped security packets: 0/0 dropped security packet detail: memory process problem: 0 can't find SA: 0 queue is full: 0 authentication is failed: 0 wrong length: 0 replay packet: 0 too long packet: 0 invalid SA: 0 policy deny: 0 the normal packet statistics: input/output dropped normal packets: 0/0
Configuration Files
- SwitchA configuration file
# sysname SwitchA # ipv6 # vlan batch 10 # ipsec proposal proposal1 encapsulation-mode transport esp authentication-algorithm sha2-256 undo esp encryption-algorithm # ipsec sa sa1 proposal proposal1 sa spi inbound esp 12345 sa string-key inbound esp cipher %^%#Rmi-NNXDj%&Uw/$;+eD@yIws7^t]!;PG}QX2QOy-%^%# sa spi outbound esp 12345 sa string-key outbound esp cipher %^%#5rV8K(\j},rE.+EezM>=SI$vBQn7z=*8aY5bqM&J%^%# # ospfv3 1 router-id 1.1.1.1 ipsec sa sa1 # interface Vlanif10 ipv6 enable ipv6 address 2001:DB8:100::1/64 ospfv3 1 area 0.0.0.1 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 10 # return
- SwitchB configuration file
# sysname SwitchB # ipv6 # vlan batch 20 # ipsec proposal proposal2 encapsulation-mode transport esp authentication-algorithm sha2-256 undo esp encryption-algorithm # ipsec sa sa2 proposal proposal2 sa spi inbound esp 12345 sa string-key inbound esp cipher %^%#wW|6AGv5|J8o#i/.s;,TU9.="{gB*3b"l^7B5.WU%^%# sa spi outbound esp 12345 sa string-key outbound esp cipher %^%#0\o;!$V>/,e.i_FdIbCA"j2a/@Jy0Z!i1'+*W5}>%^%# # ospfv3 1 router-id 2.2.2.2 ipsec sa sa2 # interface Vlanif20 ipv6 enable ipv6 address 2001:DB8:100::2/64 ospfv3 1 area 0.0.0.1 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 20 # return