IPSG Fundamentals
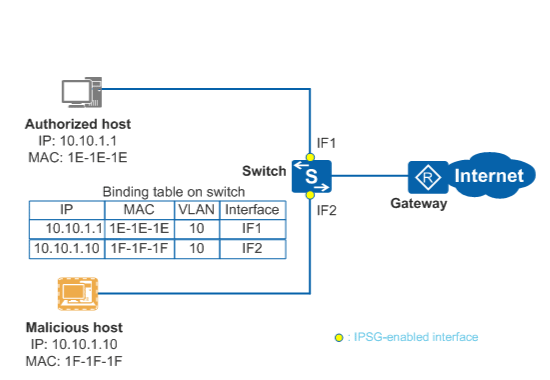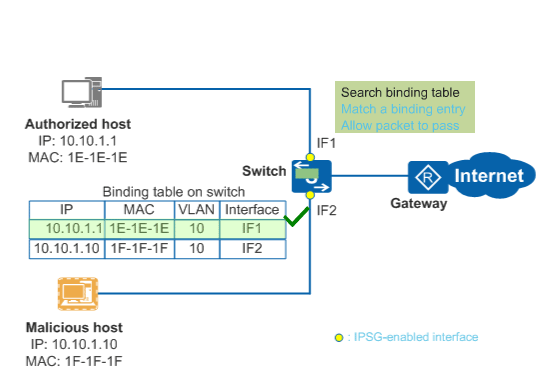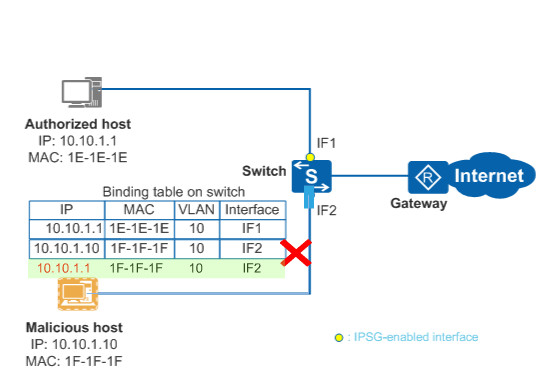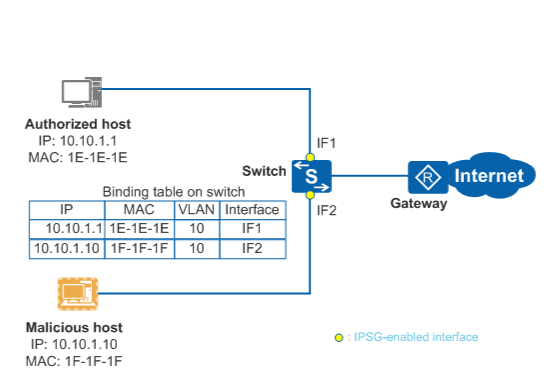
IPSG checks IP packets on Layer 2 interfaces against a binding table that contains the bindings of source IP addresses, source MAC addresses, VLANs, and inbound interfaces. Only packets matching the binding table are forwarded, and other packets are discarded.
Table 1 describes the different types of binding tables.
Type |
Description |
Application Scenario |
|---|---|---|
Static binding table |
Manually configured using the user-bind command. |
A network has a few IPv4/IPv6 hosts that use static IP addresses. |
DHCP snooping dynamic binding table (1) |
After DHCP snooping is configured, hosts request IP addresses from the DHCP server. The device generates DHCP snooping dynamic binding entries according to the DHCP reply packets returned by DHCP server. |
A network has many IPv4/IPv6 hosts that obtain IP addresses from the DHCP server. |
DHCP snooping dynamic binding table (2) |
The device generates DHCP snooping dynamic binding entries according to user information during 802.1X authentication. |
A network has many IPv4/IPv6 hosts that use static IP addresses, and 802.1X authentication has been configured on the network. This type of dynamic entries cannot ensure high accuracy. You are advised to configure static binding entries for these hosts. |
ND snooping dynamic binding table |
After ND snooping is configured, the device generates ND snooping dynamic binding entries based on the Neighbor Solicitation (NS) packets sent by users to detect duplicate addresses. |
A network has many IPv6 hosts. |
After the binding table is generated, IPSG delivers ACL rules to the specified interface or VLAN according to the binding table, and then checks all IP packets against the ACL rules. The switch forwards the packets from hosts only if the packets match binding entries, and discards the packets that do not match binding entries. When the binding table is modified, IPSG delivers the ACL rules again. By default, if IPSG is enabled but no binding table is generated, the switch forwards IP protocol packets and rejects all data packets.

IPSG checks only the IP packets from hosts, including IPv4 and IPv6 packets. It does not check non-IP packets such as ARP and PPPoE packets.
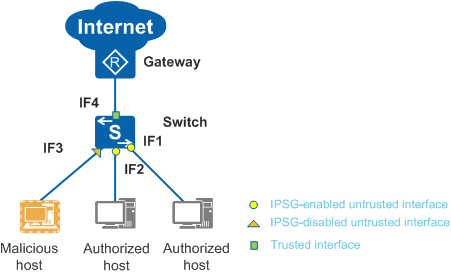
Figure 1 illustrates the IPSG working mechanism. If a malicious host uses an authorized host's IP address to send packets to the switch, the switch discards these packets because they do not match binding entries.
IPSG Interface Roles
IPSG can only be configured on Layer 2 physical interfaces or in VLANs, and checks only the packets on the untrusted interfaces with IPSG enabled. It considers all interfaces to be untrusted by default. Trusted interfaces are manually specified. IPSG trusted and untrusted interfaces are also used as trusted and untrusted interfaces in DHCP snooping and ND snooping. In addition, the trusted and untrusted interfaces are also valid for IPSG based on a static binding table.
- IF1 and IF2 are untrusted interfaces and have the IPSG function enabled. The switch performs an IPSG check on the packets received by IF1 and IF2.
- IF3 is an untrusted interface and does not have the IPSG function enabled. The switch does not perform an IPSG check on the packets received by IF3. Therefore, IF3 is prone to attacks.
- IF4 is a trusted interface, which is manually configured. The switch does not perform an IPSG check on the packets received by IF4; however, IF4 is not prone to attacks. On a network with DHCP snooping configured, the interfaces directly or indirectly connected to a valid DHCP server are generally configured as trusted interfaces.
IPSG Filtering
A static binding entry contains four options: MAC address, IP address, VLAN, and inbound interface. IPSG checks received packets against all options in a static binding entry.
A dynamic binding entry contains the same four options as a static binding entry does. You can specify the options to be checked, and IPSG filters the packets received by interfaces according to the specified options. By default, IPSG checks packets against all four options. Table 2 describes the checks commonly performed. The usage of other combinations is similar to those in the table, and is not provided here.
Option |
Description |
|---|---|
Source IP address |
The switch validates the source IP addresses of packets, and forwards the packets only when the source IP addresses in packets match binding entries. |
Source MAC address |
The switch validates the source MAC addresses of packets, and forwards the packets only when the source MAC addresses in packets match binding entries. |
Source IP address + source MAC address |
The switch validates the source IP and MAC addresses of packets, and forwards the packets only when the source IP and MAC addresses in packets match binding entries. |
Source IP address + source MAC address + interface |
The switch validates the source IP addresses, source MAC addresses, and interfaces of packets, and forwards the packets only when the source IP addresses, source MAC addresses, and interfaces in packets match binding entries. |
Source IP address + source MAC address + interface + VLAN |
The switch validates the source IP addresses, source MAC addresses, interfaces, and VLANs of packets, and forwards the packets only when the source IP addresses, source MAC addresses, interfaces, and VLANs in packets match binding entries. |