IPSG Deployment
Typically, IPSG is configured on the interfaces or VLANs of the access device connected to users.
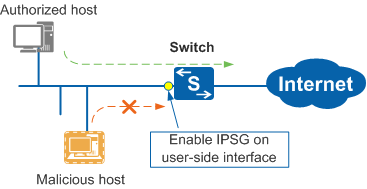
- In Figure 1, after IPSG is enabled on the user-side interface of the switch, the switch performs an IPSG check on all IP packets received by this interface.
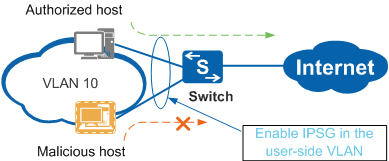
- In Figure 2, after IPSG is enabled on the user-side VLAN, the switch performs an IPSG check on the IP packets received by all interfaces in this VLAN.
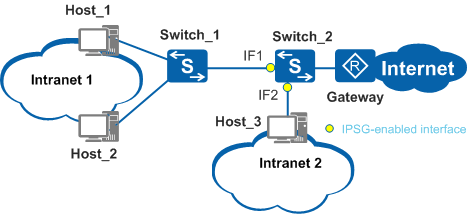
If the access device directly connected to users does not support IPSG, IPSG can be configured on the aggregation or core device, as shown in Figure 3.
- For example, Switch_1 connected to intranet 1 does not support IPSG. Therefore, IPSG is configured on IF1 of Switch_2 (a binding table needs to be built on Switch_2 for the hosts in intranet 1). Because Switch_1 does not support IPSG, the packets from Switch_1 may be IP address spoofing packets. IPSG configured on IF1 of Switch_2 can block the attack and minimize the attack scope.
- IPSG also needs to be configured on IF2 of Switch_2, which is connected to intranet 2; otherwise, intranet 2 is prone to IP address spoofing attacks.