Comparison Between IPSG and Other Features
IPSG, Dynamic ARP Inspection (DAI), static ARP, and port security are network security technologies. This section describes the differences between IPSG and DAI, IPSG and Static ARP, and IPSG and Port Security.
IPSG and DAI
IPSG and DAI use binding tables (static or DHCP snooping binding tables) to filter packets. Table 1 lists their differences.
Feature |
Description |
Usage Scenario |
|---|---|---|
IPSG |
Filters IP packets by using binding tables. The device matches IP packets received by interfaces against binding entries, and forwards the IP packets matching the binding entries. |
Prevent IP address spoofing attacks. For example, a malicious host steals an authorized host's IP address to access the network or initiate attacks. |
DAI |
Filters ARP packets by using binding tables. The device matches ARP packets received by interfaces against binding entries, and forwards the ARP packets matching the binding entries. |
Prevent man-in-the-middle attacks. Man-in-the-middle attacks are generally initiated through ARP spoofing. That is, an attacker directs traffic to itself to intercept other hosts' information. |
IPSG cannot prevent address conflicts. For example, when a malicious host steals an online host's IP address, the ARP request packets sent by the malicious host will be sent to the online host through broadcast, causing an address conflict. Therefore, to prevent IP address conflicts, you can configure both IPSG and DAI.
For details about the DAI configuration, see ARP Security Configuration.
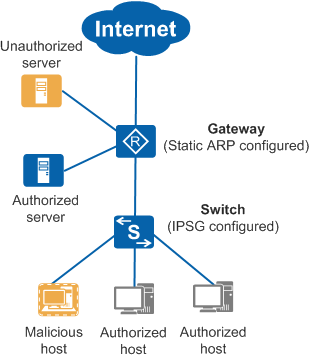
IPSG and Static ARP
Both IPSG based on a static binding table and static ARP support IP and MAC address bindings. Table 2 lists their differences.
Feature |
Description |
Usage Scenario |
|---|---|---|
IPSG |
Builds a static binding table to bind IP addresses to MAC addresses. The device checks the packets received by interfaces, and forwards the packets matching the binding entries. |
IPSG is generally configured on the access switch connected to users or on the aggregation or core switch to prevent IP address spoofing attacks from the intranet. For example, a malicious host steals an authorized host's IP address to access the network. |
Static ARP |
Builds a static ARP table to bind IP addresses to MAC addresses. A static ARP table is not dynamically updated. The device processes received packets according to the static ARP table. |
Generally, static ARP is configured on the gateway. The static ARP table stores the ARP entries of key servers to prevent ARP spoofing attacks and ensure normal communication between hosts and servers. |
- IPSG is configured on the switch to prevent malicious hosts from changing their own IP addresses or stealing authorized hosts' IP addresses to access the network.
- Static ARP entries of servers are configured on the gateway to prevent unauthorized servers from initiating ARP attacks or incorrectly updating ARP entries. This configuration ensures that hosts and authorized servers can communicate with each other normally.
Static ARP cannot prevent IP address spoofing attacks.
Assume that IPSG is not configured on the switch, and static ARP entries of hosts are configured on the gateway. When a malicious host steals an authorized host's IP address to access the Internet, the packet forwarding process is as follows:
- The packet sent by the malicious host reaches the switch.
- The switch forwards the packet to the gateway.
- The gateway forwards the packet to the Internet.
- The packet returned from the Internet reaches the gateway.
- The gateway searches for the static ARP entry according to the destination IP address (the IP address of the authorized host). If an entry is found, the gateway considers the MAC address corresponding to this IP address as the authorized host's MAC address. The gateway then encapsulates the packet and forwards it to the switch.
- The switch forwards the packet to the authorized host according to the destination MAC address.
If the malicious host changes its IP address to that of an authorized host, static ARP can prevent access of the malicious host. However, the authorized host will receive a large number of invalid reply packets. The malicious host can continue to send such packets to initiate an attack against the authorized host, and receive return packets.
The preceding scenario can occur if the malicious host uses an idle IP address that has not been added to the static ARP table. To use static ARP to prevent the theft of IP addresses, you need to add all the IP addresses on the network, including idle IP addresses, to the static ARP table. This is a very time-consuming process.
In addition, because static ARP is configured on the gateway, IP address spoofing attacks on the network connected to the switch cannot be prevented.
To prevent IP address spoofing attacks on an intranet, it is recommended that you configure IPSG on the switch.
IPSG cannot prevent ARP spoofing attacks.
Assume that IPSG is configured on the switch, and static ARP entries of hosts are not configured on the gateway.- A malicious host steals an authorized host's IP address to send a bogus ARP request packet to the switch.
- The switch forwards the packet to the gateway, and then the gateway incorrectly updates the ARP entry of the authorized host. In the ARP entry, the IP address belongs to the authorized host and the MAC address belongs to the malicious host.
- When the authorized host accesses the Internet, the reply packets from the Internet are returned to the malicious host. As a result, the authorized host cannot go online.
In addition, the malicious host is able to intercept the packets sent from the Internet to the authorized host.
Two methods are available to solve this problem. One method is to configure both IPSG on the switch and static ARP entries of hosts on the gateway. However, configuration and maintenance are complex for a network with a large number of hosts. Another method is to configure both IPSG and DAI on the switch. The switch matches IP and ARP packets received by interfaces against binding entries, and discards the ARP packets that do not match binding entries. Because the bogus ARP packets cannot reach the gateway, the ARP entries will not be incorrectly modified.
For details about static ARP, see ARP Configuration in the S2720, S5700, and S6700 V200R019C10 Configuration Guide - IP Service.
IPSG and Port Security
Both IPSG based on a static binding table and port security support MAC address and interface binding. Table 3 lists their differences.
Feature |
Description |
Usage Scenario |
|---|---|---|
IPSG |
Binds MAC addresses to interfaces in the binding table. This ensures that a host can go online only through a fixed port. Hosts whose MAC addresses are not in the binding table cannot go online through the device. The binding entries are manually configured. If a network has a large number of hosts, the configuration workload is heavy. |
In addition to binding MAC addresses to interfaces, IPSG can bind IP addresses, MAC addresses, VLANs, and interfaces. IPSG prevents IP address spoofing attacks. For example, a malicious host steals an authorized host's IP address to access or attack the network. |
Port security |
Converts the limited number of dynamic MAC entries learned by interfaces into secure MAC entries. This ensures that a host can go online only through a fixed port. Hosts whose MAC addresses are not in the MAC address table cannot go online through the device. Secure MAC entries are dynamically generated. |
Port security prevents access of unauthorized hosts and limits the number of access hosts. It is applicable to networks with a large number of hosts. |
If you need only to prevent hosts with unauthorized MAC addresses from communicating with each other and a large number of hosts reside on the network, port security is recommended.
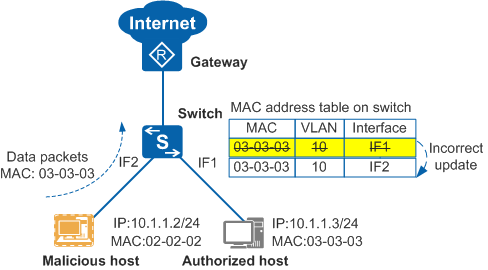
IPSG does not fix MAC entries. Therefore, it cannot prevent MAC address flapping caused by incorrect MAC entry updates. In Figure 2, when a malicious host sends data (for example, bogus ARP packets) to the switch by using an authorized host's MAC address, the switch incorrectly updates the MAC address table. As a result, the malicious host can intercept the packets destined for the authorized host.
To prevent MAC address flapping illustrated in the preceding figure, you can configure the device to generate snooping MAC entries based on binding tables.
For details about port security, see Port Security Configuration.
IPSG, DAI, static ARP, and port security address different issues and apply to different scenarios. Therefore, it is recommended that you configure them according to your security and networking requirements.