Example for Configuring ACL-based Layer 2 Remote Traffic Mirroring
Networking Requirements
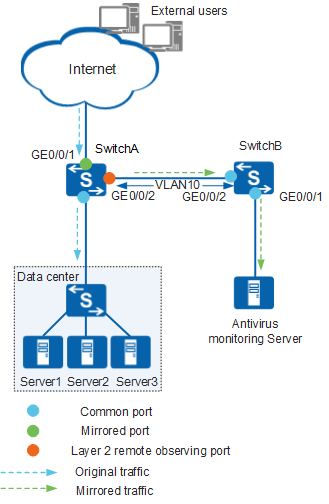
In Figure 1, external users access the servers of a company from the Internet through SwitchA. The antivirus monitoring device (Server) connects to SwitchA through SwitchB.
The official website of the company is paralyzed because of malicious attacks. The Server needs to remotely analyze traffic with TCP port number WWW to locate the attack source.
Configuration Roadmap
- Configure GE0/0/2 of SwitchA as a Layer 2 remote observing port to forward mirrored packets to the specified VLAN.
- Configure an advanced ACL on SwitchA to match traffic with TCP port number WWW.
- Configure an ACL-based traffic policy on GE0/0/1 of SwitchA to mirror the matching traffic.
- Create a VLAN on SwitchB, disable MAC address learning in this VLAN, and add ports to the VLAN to forward the mirrored packets sent from the observing port to the Server.
Procedure
- Configure an observing port on SwitchA.
# Configure GE0/0/2 of SwitchA as a Layer 2 remote observing port and bind the observing port to VLAN 10.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] observe-port 1 interface gigabitethernet 0/0/2 vlan 10
# Disable the observing port from forwarding data packets.[SwitchA] observe-port 1 forwarding disable
- Configure an advanced ACL on SwitchA.
# Create an advanced ACL numbered 3000 on SwitchA to match traffic with TCP port number WWW.
[SwitchA] acl number 3000 [SwitchA-acl-adv-3000] rule permit tcp destination-port eq www [SwitchA-acl-adv-3000] quit
- Configure an ACL-based traffic policy on SwitchA.
# Configure an ACL-based traffic policy on GE0/0/1 of SwitchA to mirror the matching traffic.
[SwitchA] interface gigabitethernet 0/0/1 [SwitchA-GigabitEthernet0/0/1] traffic-mirror inbound acl 3000 to observe-port 1 [SwitchA-GigabitEthernet0/0/1] return
- Create a VLAN on SwitchB and add ports to
the VLAN.
# Create VLAN 10 on SwitchB, disable MAC address learning in VLAN 10, and add GE0/0/1 and GE0/0/2 to VLAN 10.

VLAN 10 is used for forwarding only mirrored packets. If VLAN 10 already exists and has learned MAC address entries, run the undo mac-address vlan vlan-id command in the system view to delete all MAC address entries in VLAN 10.
<HUAWEI> system-view [HUAWEI] sysname SwitchB [SwitchB] vlan 10 [SwitchB-vlan10] mac-address learning disable [SwitchB-vlan10] quit [SwitchB] interface gigabitethernet 0/0/1 [SwitchB-GigabitEthernet0/0/1] port link-type access [SwitchB-GigabitEthernet0/0/1] port default vlan 10 [SwitchB-GigabitEthernet0/0/1] quit [SwitchB] interface gigabitethernet 0/0/2 [SwitchB-GigabitEthernet0/0/2] port link-type trunk [SwitchB-GigabitEthernet0/0/2] port trunk allow-pass vlan 10 [SwitchB-GigabitEthernet0/0/2] return
- Verify the configuration.
# Check ACL rules and traffic behavior information.
<SwitchA> display traffic-applied interface gigabitethernet 0/0/1 inbound ----------------------------------------------------------- ACL applied inbound interface GigabitEthernet0/0/1 ACL 3000 rule 5 permit tcp destination-port eq www (match-counter 0) ACTIONS: mirror to observe-port 1 -----------------------------------------------------------
# Check the observing port configuration.
<SwitchA> display observe-port ---------------------------------------------------------------------- Index : 1 Untag-packet : No Forwarding : No Interface : GigabitEthernet0/0/2 Vlan : 10 ----------------------------------------------------------------------
# Check the mirrored port configuration.
<SwitchA> display port-mirroring ---------------------------------------------------------------------- Observe-port 1 : GigabitEthernet0/0/2 ---------------------------------------------------------------------- Stream-mirror: ---------------------------------------------------------------------- Behavior Direction Observe-port ---------------------------------------------------------------------- 1 SACL - Observe-port 1 ----------------------------------------------------------------------