Example for Configuring MAC Address Authentication (AAA Local Authentication Is Used)
Networking Requirements
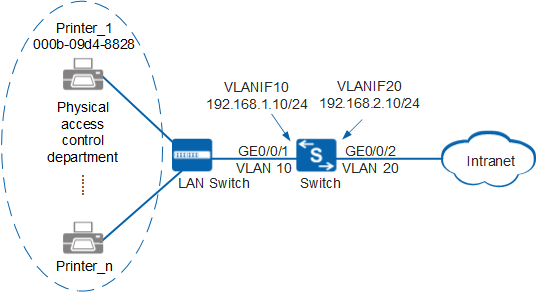
As shown in Figure 1, terminals in a company's physical access control department are connected to the company's internal network through the Switch. Unauthorized access to the internal network can damage the company's service system and cause leakage of key information. Therefore, the administrator requires that the Switch should control users' network access rights to ensure internal network security.
Because dumb terminals (such as printers) in the physical access control department cannot have the authentication client installed, MAC address authentication needs to be configured on the Switch, and the local authentication mode is configured to authenticate user identities.
Procedure
- Configure AAA local authentication.
# Configure the local authentication scheme a1.
[Switch] aaa [Switch-aaa] authentication-scheme a1 [Switch-aaa-authen-a1] authentication-mode local [Switch-aaa-authen-a1] quit
# Configure the local authorization scheme b1.
[Switch-aaa] authorization-scheme b1 [Switch-aaa-author-b1] authorization-mode local [Switch-aaa-author-b1] quit
# Configure the user name, password, and access type of the local user.

Configure terminals' MAC addresses as local user names, set the password to Huawei@123, and set the access type to MAC address authentication (8021x). Take printer 1 with the MAC address 000b-09d4-8828 as an example.
[Switch-aaa] local-user 000b-09d4-8828 password cipher Huawei@123 [Switch-aaa] local-user 000b-09d4-8828 service-type 8021x [Switch-aaa] quit
# Configure service scheme s1 so that users can access resources on the network segment 192.168.2.0 after being authenticated successfully.
[Switch] ucl-group 10 name g1 [Switch] acl 6000 [Switch-acl-ucl-6000] rule 10 permit ip source ucl-group name g1 destination 192.168.2.0 0 [Switch-acl-ucl-6000] quit [Switch] traffic-filter inbound acl 6000 [Switch] aaa [Switch-aaa] service-scheme s1 [Switch-aaa-service-s1] ucl-group name g1 [Switch-aaa-service-s1] quit
# Configure the domain huawei.com, and apply the authentication scheme a1, authorization scheme b1, and service scheme s1 to the domain.
[Switch-aaa] domain huawei.com [Switch-aaa-domain-huawei.com] authentication-scheme a1 [Switch-aaa-domain-huawei.com] authorization-scheme b1 [Switch-aaa-domain-huawei.com] service-scheme s1 [Switch-aaa-domain-huawei.com] quit [Switch-aaa] quit
- Configure MAC address authentication.# Set the NAC mode to unified.
[Switch] authentication unified-mode

- By default, the unified mode is used.
- After changing the NAC mode from common to unified, save the configuration and restart the device to make the configuration take effect.
# Configure the MAC access profile m1.

When AAA local authentication and authorization are used, the user name and password for MAC address authentication must be the same as those of the AAA local user. In this example, the user name of the local user is the terminal's MAC address containing hyphens (-) and the password is Huawei@123.
[Switch] mac-access-profile name m1 [Switch-mac-access-profile-m1] mac-authen username macaddress format with-hyphen password cipher Huawei@123 [Switch-mac-access-profile-m1] quit
# Configure the authentication profile p1, bind the MAC access profile m1 to the authentication profile, and specify the domain huawei.com as the forcible authentication domain in the authentication profile.
[Switch] authentication-profile name p1 [Switch-authen-profile-p1] mac-access-profile m1 [Switch-authen-profile-p1] access-domain huawei.com force [Switch-authen-profile-p1] quit
# Bind the authentication profile p1 to GE0/0/1 and enable MAC address authentication on the interface.
[Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] authentication-profile p1 [Switch-GigabitEthernet0/0/1] quit
- Verify the configuration.
- After a user starts a terminal, the device automatically obtains the user terminal's MAC address as the user name and password for authentication.
- Users can access the network after being authenticated successfully.
- After users go online, you can run the display access-user access-type mac-authen command on the device to view information about online MAC address authentication users.