Example for Configuring MAC Address Authentication with Double VLAN Tags in the L2 BNG Scenario (AAA RADIUS Authentication Is Used)
Networking Requirements
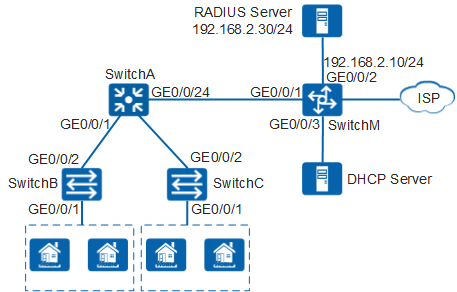
In Figure 1, residential home users are connected to carrier networks through switches. Different home users may choose different carriers, and the same home user may use different device types. To ensure that all the devices of the same home user can be connected to their corresponding carrier networks, double VLAN tags need to be used. That is, the inner VLAN tag distinguishes different devices, and the outer VLAN tag distinguishes different home users.
Because the authentication client may be unable to be installed on some devices of home users, MAC authentication needs to be deployed on SwitchM. After user devices pass MAC authentication, they can be connected to their carrier networks. S5720-LI, S5735-L, S5735S-L, and S5735S-L-M switches act as the access switches in this example.
Configuration Roadmap
The configuration roadmap is as follows:
- Configure SwitchB and SwitchC to connect to user devices.
- Configure SwitchA to implement double VLAN tags.
- Configure SwitchM to implement identity authentication on access users through the RADIUS server.

Before performing operations in this example, ensure that user access terminals and servers can communicate.
This example provides only the configurations of SwitchA, SwitchB, and SwitchM. Server configuration and user-side configuration are not provided here.
Procedure
- Configure SwitchB. The configuration of SwitchC is similar to that of SwitchB, and is not mentioned here.
<HUAWEI> system-view [HUAWEI] sysname SwitchB [SwitchB] vlan batch 101 [SwitchB] interface gigabitethernet 0/0/1 [SwitchB-GigabitEthernet0/0/1] port link-type access [SwitchB-GigabitEthernet0/0/1] port default vlan 101 [SwitchB-GigabitEthernet0/0/1] quit [SwitchB] interface gigabitethernet 0/0/2 [SwitchB-GigabitEthernet0/0/2] port link-type trunk [SwitchB-GigabitEthernet0/0/2] port trunk allow-pass vlan 101 [SwitchB-GigabitEthernet0/0/2] quit
- Configure SwitchA.
# Create VLANs and configure GE0/0/1 connecting SwitchA to SwitchB.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] vlan batch 3 101 [SwitchA] interface gigabitethernet 0/0/1 [SwitchA-GigabitEthernet0/0/1] port link-type hybrid [SwitchA-GigabitEthernet0/0/1] qinq vlan-translation enable [SwitchA-GigabitEthernet0/0/1] port hybrid tagged vlan 101 [SwitchA-GigabitEthernet0/0/1] port hybrid untagged vlan 3 [SwitchA-GigabitEthernet0/0/1] port vlan-stacking vlan 101 stack-vlan 3 [SwitchA-GigabitEthernet0/0/1] quit
# Configure users to use the user-defined Option82 user name huawei and the password configured on SwitchM for authentication.
[SwitchA] dhcp enable [SwitchA] dhcp snooping enable [SwitchA] interface gigabitethernet 0/0/1 [SwitchA-GigabitEthernet0/0/1] dhcp snooping enable [SwitchA-GigabitEthernet0/0/1] dhcp option82 rebuild enable [SwitchA-GigabitEthernet0/0/1] dhcp option82 circuit-id format user-defined "huawei" [SwitchA-GigabitEthernet0/0/1] quit
# Configure GE0/0/24 connecting SwitchA to SwitchM.
[SwitchA] interface gigabitethernet 0/0/24 [SwitchA-GigabitEthernet0/0/24] port link-type trunk [SwitchA-GigabitEthernet0/0/24] undo port trunk allow-pass vlan 1 [SwitchA-GigabitEthernet0/0/24] port trunk allow-pass vlan 3 [SwitchA-GigabitEthernet0/0/24] dhcp snooping trusted [SwitchA-GigabitEthernet0/0/24] quit
- Configure SwitchM.
# Configure GE0/0/1 connecting SwitchM to users.
<HUAWEI> system-view [HUAWEI] sysname Switch [SwitchM] vlan batch 3 [SwitchM] interface gigabitethernet 0/0/1 [SwitchM-GigabitEthernet0/0/1] port link-type trunk [SwitchM-GigabitEthernet0/0/1] undo port trunk allow-pass vlan 1 [SwitchM-GigabitEthernet0/0/1] port trunk allow-pass vlan 3 [SwitchM-GigabitEthernet0/0/1] quit [SwitchM] interface vlanif 3 [SwitchM-Vlanif3] ip address 192.168.3.10 24 [SwitchM-Vlanif3] quit
# Configure GE0/0/2 connecting SwitchM to the RADIUS server.
[SwitchM] vlan batch 20 [SwitchM] interface gigabitethernet 0/0/2 [SwitchM-GigabitEthernet0/0/2] port link-type access [SwitchM-GigabitEthernet0/0/2] port default vlan 20 [SwitchM-GigabitEthernet0/0/2] quit [SwitchM] interface vlanif 20 [SwitchM-Vlanif20] ip address 192.168.2.10 24 [SwitchM-Vlanif20] quit
# Configure GE0/0/3 connecting SwitchM to the DHCP server.

On the RADIUS server, you need to set the HW-Forwarding-VLAN (26-161) attribute to VLAN 3000 and the HW-Forwarding-Interface (26-162) attribute to GE0/0/3. That is, the ISP VLAN and outbound interface used for user packet forwarding are VLAN 3000 and GE0/0/3 respectively.
The RADIUS server can only grant HW-Forwarding-VLAN and HW-Forwarding-Interface to users who go online through the S5730-HI, S5731-H, S5731S-H, S5731-S, S5731S-S, S5732-H, S6730-H, S6730S-H, S6730-S, S6730S-S, S6720-HI, and S5720-HI. If the RADIUS server grants HW-Forwarding-VLAN and HW-Forwarding-Interface to users who pass authentication and go online through other switches, the users will go offline.
[SwitchM] vlan batch 3000 [SwitchM] interface gigabitethernet 0/0/3 [SwitchM-GigabitEthernet0/0/3] port link-type trunk [SwitchM-GigabitEthernet0/0/3] port trunk allow-pass vlan 3000 [SwitchM-GigabitEthernet0/0/3] quit
# Create and configure the RADIUS server template rd1.
[SwitchM] radius-server template rd1 [SwitchM-radius-rd1] radius-server authentication 192.168.2.30 1812 [SwitchM-radius-rd1] radius-server shared-key cipher Huawei@2012 [SwitchM-radius-rd1] quit
# Create the AAA authentication scheme abc and set the authentication mode to RADIUS.
[SwitchM] aaa [SwitchM-aaa] authentication-scheme abc [SwitchM-aaa-authen-abc] authentication-mode radius [SwitchM-aaa-authen-abc] quit
# Create the authentication domain huawei.com, and bind the AAA authentication scheme abc and RADIUS server template rd1 to the domain.
[SwitchM-aaa] domain huawei.com [SwitchM-aaa-domain-huawei.com] authentication-scheme abc [SwitchM-aaa-domain-huawei.com] radius-server rd1 [SwitchM-aaa-domain-huawei.com] quit [SwitchM-aaa] quit
# Check whether a user can pass RADIUS authentication. (The test user test and password Huawei2012 have been configured on the RADIUS server.)
[SwitchM] test-aaa test Huawei2012 radius-template rd1 Info: Account?test?succeeded.
# Set the NAC mode to unified.
By default, the unified mode is used. The switch restarts after the NAC mode is changed between the common mode and unified mode.
[Switch] authentication unified-mode
# Configure the MAC access profile m1 and enable SwitchM to send Option82 information to the authentication server when receiving DHCP packets that trigger MAC address authentication.
[SwitchM] mac-access-profile name m1 [SwitchM-mac-access-profile-m1] authentication trigger-condition dhcp [SwitchM-mac-access-profile-m1] authentication trigger-condition dhcp dhcp-option 82 [SwitchM-mac-access-profile-m1] mac-authen username dhcp-option 82 circuit-id password cipher huawei123 [SwitchM-mac-access-profile-m1] quit
# Configure the authentication profile p1, bind the MAC access profile m1 to the authentication profile, and specify the domain huawei.com as the forcible authentication domain in the authentication profile.
[SwitchM] authentication-profile name p1 [SwitchM-authen-profile-p1] mac-access-profile m1 [SwitchM-authen-profile-p1] access-domain huawei.com force [SwitchM-authen-profile-p1] quit
# Bind the authentication profile p1 to GE0/0/1 and enable MAC address authentication on the interface.
[SwitchM] interface gigabitethernet 0/0/1 [SwitchM-GigabitEthernet0/0/1] authentication-profile p1 [SwitchM-GigabitEthernet0/0/1] quit
- Verify the configuration.
- After a user starts a terminal, SwitchM automatically obtains the user terminal's Option82 information as the user name for authentication.
- After users go online, you can run the display access-user access-type mac-authen command on SwitchM to view information about online MAC address authentication users.
Configuration Files
# sysname SwitchB # vlan batch 101 # interface GigabitEthernet0/0/1 port link-type access port default vlan 101 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 101 # return
# SwitchA configuration file
# sysname SwitchA # vlan batch 3 101 # dhcp enable # dhcp snooping enable # interface GigabitEthernet0/0/1 port link-type hybrid qinq vlan-translation enable port hybrid tagged vlan 101 port hybrid untagged vlan 3 port vlan-stacking vlan 101 stack-vlan 3 dhcp snooping enable dhcp option82 rebuild enable dhcp option82 circuit-id format user-defined "huawei" # interface GigabitEthernet0/0/24 port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 3 dhcp snooping trusted # return
# SwitchM configuration file
# sysname SwitchM # vlan batch 3 20 3000 # authentication-profile name p1 mac-access-profile m1 access-domain huawei.com force # access-user arp-detect vlan 3 ip-address 192.168.3.10 mac-address 2222-1111-1234 # radius-server template rd1 radius-server shared-key cipher %^%#4*SO-2u,Q.\1C~%[eiB77N/^2wME;6t%6U@qAJ9:%^%# radius-server authentication 192.168.2.30 1812 weight 80 # aaa authentication-scheme abc authentication-mode radius domain huawei.com authentication-scheme abc radius-server rd1 # interface Vlanif3 ip address 192.168.3.10 255.255.255.0 # interface Vlanif20 ip address 192.168.2.10 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 3 authentication-profile p1 # interface GigabitEthernet0/0/2 port link-type access port default vlan 20 # interface GigabitEthernet0/0/3 port link-type trunk port trunk allow-pass vlan 3000 # mac-access-profile name m1 authentication trigger-condition dhcp authentication trigger-condition dhcp dhcp-option 82 mac-authen username dhcp-option 82 circuit-id password cipher %^%#o=QK8l^,C#m'+b.CKQ4=YdHDL"-X+Q%c+"R7!Qq5%^%# # return