Example for Connecting IP Phones to Switches Through MAC Address Authentication Triggered by LLDP or CDP Packets
Overview of MAC Address Authentication Triggered by LLDP or CDP Packets
By default, the switch can trigger MAC address authentication on users after receiving DHCP, ARP, DHCPv6, or ND packets. If a static IPv4 address is configured for a client, no DHCP or ARP packet is exchanged between the client and switch. You can configure the function of triggering MAC address authentication through LLDP or CDP packets. During access authentication of an IP phone, LLDP or CDP negotiation packets sent from the IP phone do not carry VLAN tags. After receiving the packets, an access switch adds data VLAN tags to the packets. Since MAC address authentication can be triggered through any packet, the IP phone is authenticated and goes online in the data VLAN. After a voice VLAN is negotiated, the IP phone is authenticated and goes online in the voice VLAN. Therefore, MAC address migration and user online status detection before migration need to be configured.
Configuration Notes
This example applies to all S series switches running V200R011C10 and later versions.
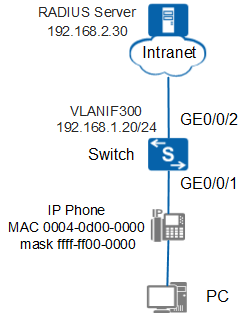
Networking Requirements
In Figure 1, the switch connects to an IP phone and a PC, and uses VLAN 200 to transmit voice packets and VLAN 100 to transmit data packets. The PC connects to the IP phone, and they are connected to the switch. Users require high quality of the VoIP service; therefore, voice data flows must be transmitted with a high priority to ensure the call quality.
Configuration Roadmap
- Create VLANs on the switch and add interfaces to the VLANs to implement Layer 2 connectivity. VLAN 200 is a voice VLAN, and VLAN 100 is a data VLAN and the default VLAN of GE1/0/1.
- Configure the voice VLAN function.
- Configure an AAA authentication domain and MAC address authentication.
- Configure MAC address migration.

- The IP address and shared key configured in the RADIUS server template must be the same as those on the RADIUS server.
- For details about the configurations on the RADIUS server, see the example for configuring MAC address authentication in the corresponding server documentation.
Procedure
- Set the NAC mode to unified on the Switch.

By default, the unified mode is used. After the common mode and unified mode are switched, you must save the configuration and restart the switch to make each function in the new configuration mode take effect.
<HUAWEI> system-view [HUAWEI] authentication unified-mode
- Configure VLANs and interfaces on the Switch.
# Create VLANs and enable the LLDP function.
[HUAWEI] sysname Switch [Switch] vlan batch 100 200 300 [Switch] lldp enable //Enable the LLDP function globally.
# Configure the PVID of GE0/0/1 and the allowed data VLAN on the interface.
[Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] port link-type hybrid [Switch-GigabitEthernet0/0/1] port hybrid pvid vlan 100 [Switch-GigabitEthernet0/0/1] port hybrid untagged vlan 100 [Switch-GigabitEthernet0/0/1] quit [Switch] interface vlanif 100 [Switch-Vlanif100] ip address 192.168.100.10 24 [Switch-Vlanif100] quit [Switch] interface vlanif 200 [Switch-Vlanif200] ip address 192.168.200.10 24 [Switch-Vlanif200] quit
# Configure GE0/0/2 connecting the switch to the RADIUS server as an access interface and add the interface to VLAN 300.
[Switch] interface gigabitethernet 0/0/2 [Switch-GigabitEthernet0/0/2] port link-type access [Switch-GigabitEthernet0/0/2] port default vlan 300 [Switch-GigabitEthernet0/0/2] quit [Switch] interface vlanif 300 [Switch-Vlanif300] ip address 192.168.1.20 24 [Switch-Vlanif300] quit
- Set the voice VLAN and OUI address.
[Switch] voice-vlan mac-address 0004-0D00-0000 mask ffff-ff00-0000 //Set the OUI address to the IP phone's MAC address, which may vary according to the network. [Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] voice-vlan 200 enable //Set the voice VLAN to 200. [Switch-GigabitEthernet0/0/1] voice-vlan legacy enable //Enable the CDP-compatible voice VLAN function so that the switch encapsulates voice VLAN information in CDP packets and sends them to the connected IP phone. [Switch-GigabitEthernet0/0/1] stp edged-port enable //Configure the interface as an edge interface. [Switch-GigabitEthernet0/0/1] port hybrid tagged vlan 200 [Switch-GigabitEthernet0/0/1] voice-vlan remark-mode mac-address //Configure the switch to identify voice packets in the voice VLAN based on MAC addresses of IP phones. [Switch-GigabitEthernet0/0/1] poe legacy enable //Enable the PoE switch to check the compatibility of PDs so that the switch can supply power to non-standard PDs. [Switch-GigabitEthernet0/0/1] lldp tlv-enable med-tlv network-policy voice-vlan vlan 200 //Configure LLDP_MED to allocate a voice VLAN to IP phones. [Switch-GigabitEthernet0/0/1] lldp compliance cdp txrx //Enable an interface to exchange information with voice devices that support CDP before connectivity. [Switch-GigabitEthernet0/0/1] quit
- Configure a static route to the server area. In this example, the IP address for the server area to connect to the Switch is 192.168.2.20.
[Switch] ip route-static 192.168.2.0 255.255.255.0 192.168.2.20
- Configure AAA.
# Create and configure the RADIUS server template rd1.
[Switch] radius-server template rd1 [Switch-radius-rd1] radius-server authentication 192.168.2.30 1812 [Switch-radius-rd1] radius-server shared-key cipher Huawei@2012 [Switch-radius-rd1] quit
# Create the AAA authentication scheme abc and set the authentication mode to RADIUS.
[Switch] aaa [Switch-aaa] authentication-scheme abc [Switch-aaa-authen-abc] authentication-mode radius [Switch-aaa-authen-abc] quit
# Create the authentication domain huawei.com, and bind the AAA authentication scheme abc and RADIUS server template rd1 to the domain.
[Switch-aaa] domain huawei.com [Switch-aaa-domain-huawei.com] authentication-scheme abc [Switch-aaa-domain-huawei.com] radius-server rd1 [Switch-aaa-domain-huawei.com] quit [Switch-aaa] quit
# Check whether a user can be authenticated using RADIUS authentication. (The test user test and password Huawei2012 have been configured on the RADIUS server.)
[Switch] test-aaa test Huawei2012 radius-template rd1 Info: Account test succeeded.
- Configure MAC address authentication.
# Configure the MAC access profile m1, and enable the function of triggering MAC address authentication through any packet.

In a MAC access profile, a MAC address without hyphens (-) is used as the user name and password for MAC address authentication by default. Ensure that the formats of the user name and password for MAC address authentication configured on the RADIUS server are the same as those configured on the access device.
[Switch] mac-access-profile name m1 [Switch-mac-access-profile-m1] authentication trigger-condition dhcp arp dhcpv6 nd any-l2-packet [Switch-mac-access-profile-m1] quit
# Configure the authentication profile p1, bind the MAC access profile m1 to the authentication profile, and specify the domain huawei.com as the forcible authentication domain in the authentication profile.
[Switch] authentication-profile name p1 [Switch-authen-profile-p1] mac-access-profile m1 [Switch-authen-profile-p1] access-domain huawei.com force [Switch-authen-profile-p1] quit
# Bind the authentication profile p1 to GE0/0/1 and enable MAC address authentication on the interface.
[Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] authentication-profile p1 [Switch-GigabitEthernet0/0/1] quit
- Configure MAC address migration and user online status detection before migration.
[Switch] authentication mac-move enable vlan all [Switch] authentication mac-move detect enable
- Verify the configuration.
The IP phone can go online and support clear voice communication. The PC can also go online normally.
Configuration Files
Configuration file of the Switch
# sysname Switch # voice-vlan mac-address 0004-0d00-0000 mask ffff-ff00-0000 # vlan batch 100 200 300 # access-user arp-detect vlan 100 ip-address 192.168.100.10 mac-address 2222-1111-1234 access-user arp-detect vlan 200 ip-address 192.168.200.10 mac-address 2222-1111-1234 # authentication-profile name p1 mac-access-profile m1 access-domain huawei.com force authentication mac-move enable vlan all authentication mac-move detect enable # radius-server template rd1 radius-server shared-key cipher %^%#4*SO-2u,Q.\1C~%[eiB77N/^2wME;6t%6U@qAJ9:%^%# radius-server authentication 192.168.2.30 1812 weight 80 # aaa authentication-scheme abc authentication-mode radius domain huawei.com authentication-scheme abc radius-server rd1 # interface Vlanif300 ip address 192.168.1.20 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type hybrid voice-vlan 200 enable voice-vlan remark-mode mac-address voice-vlan legacy enable port hybrid pvid vlan 100 port hybrid tagged vlan 200 port hybrid untagged vlan 100 stp edged-port enable authentication-profile p1 poe legacy enable lldp tlv-enable med-tlv network-policy voice-vlan vlan 200 lldp compliance cdp txrx # interface GigabitEthernet0/0/2 port link-type access port default vlan 300 # ip route-static 192.168.1.0 255.255.255.0 192.168.2.20 # mac-access-profile name m1 authentication trigger-condition dhcp arp dhcpv6 nd any-l2-packet # return