Example for Configuring WeChat Authentication in a Wireless-to-Wired Scenario
Configuration Notes
- The RADIUS authentication and accounting shared keys and Portal shared key on the switch must be the same as those on the Agile Controller-Campus.
- Huawei Agile Controller-Campus functions as the RADIUS server in this example. For the Agile Controller-Campus, the version required is V100R003SPC103.
- Layer 3 Portal authentication is not supported in this scenario.
Networking Requirements
- After association between a Wi-Fi network and a WeChat official account is configured, mobile phone users can access the Internet after connecting to the Wi-Fi network and following the WeChat official account. The AC and AP are third-party wireless access devices.
- If a user goes offline after passing Portal authentication for the first time, the user can go online again within a certain period (60 minutes for example) without entering the user name and password again. MAC address-prioritized Portal authentication can be configured to enable users to access the network. That is, MAC address + Portal authentication is enabled on SwitchB and MAC address-prioritized Portal authentication is enabled on the Agile Controller-Campus simultaneously.
- In a user roaming scenario, MAC address migration can be enabled.
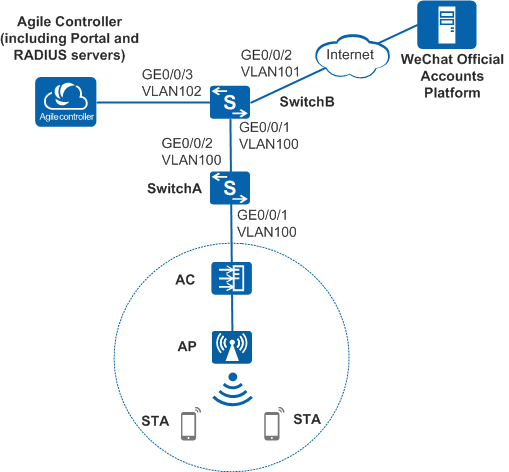
Network Data Plan
Item |
Data |
Description |
|---|---|---|
SwitchB |
IP address of VLANIF 100: 192.168.10.1 |
Client gateway. |
192.168.10.1 to 192.168.10.254/24 |
IP address pool of the client. |
|
IP address of VLANIF 101: 192.168.20.1 |
IP address of the interface connected to the public network. |
|
IP address of VLANIF 102: 192.168.30.1 |
Gateway connected to the Agile Controller-Campus. |
|
Portal server:
|
|
|
RADIUS authentication server:
|
||
RADIUS accounting server:
|
||
Agile Controller-Campus |
Domain name: access.example.com |
Users can also use the domain name to access the Portal server. |
IP address: 192.168.30.2 |
- |
|
Authentication port number: 1812 |
- |
|
Accounting port number: 1813 |
- |
|
RADIUS shared key: Admin@123 |
It must be the same as that configured on the switch. |
|
Port number in the packets received by the Portal server: 50200 |
- |
|
Portal shared key: Admin@123 |
It must be the same as that configured on the switch. |
Configuration Roadmap
- Configure network connectivity.
- Set the NAC mode to unified on SwitchB.
- Configure parameters for SwitchB to communicate with the Agile Controller-Campus (RADIUS server).
- Configure MAC address + Portal authentication.
- Configure MAC address migration.
- Configure basic WLAN services. (Configuration details of third-party devices are not provided here.)
- Configure the WeChat official account management platform.
- Configure the Agile Controller-Campus.
Procedure
- Configure network connectivity.
# Add GE0/0/1 that connects SwitchA to the AC to VLAN 100 and add GE0/0/2 that connects SwitchA to SwitchB to the same VLAN.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] vlan batch 100 [SwitchA] interface gigabitethernet 0/0/1 [SwitchA-GigabitEthernet0/0/1] port link-type trunk [SwitchA-GigabitEthernet0/0/1] port trunk pvid vlan 100 [SwitchA-GigabitEthernet0/0/1] port trunk allow-pass vlan 100 [SwitchA-GigabitEthernet0/0/1] quit [SwitchA] interface gigabitethernet 0/0/2 [SwitchA-GigabitEthernet0/0/2] port link-type trunk [SwitchA-GigabitEthernet0/0/2] port trunk allow-pass vlan 100 [SwitchA-GigabitEthernet0/0/2] quit
# Add GE0/0/1 that connects SwitchB to SwitchA to VLAN 100, add GE0/0/3 connected to the Agile Controller-Campus to VLAN 102, and add GE0/0/2 connected to the public network to VLAN 101.
<HUAWEI> system-view [HUAWEI] sysname SwitchB [SwitchB] vlan batch 100 101 102 [SwitchB] interface gigabitethernet 0/0/1 [SwitchB-GigabitEthernet0/0/1] port link-type trunk [SwitchB-GigabitEthernet0/0/1] port trunk allow-pass vlan 100 [SwitchB-GigabitEthernet0/0/1] quit [SwitchB] interface gigabitethernet 0/0/3 [SwitchB-GigabitEthernet0/0/3] port link-type trunk [SwitchB-GigabitEthernet0/0/3] port trunk allow-pass vlan 102 [SwitchB-GigabitEthernet0/0/3] quit [SwitchB] interface gigabitethernet 0/0/2 [SwitchB-GigabitEthernet0/0/2] port link-type trunk [SwitchB-GigabitEthernet0/0/2] port trunk allow-pass vlan 101 //Configure SwitchB uplink interfaces to transparently transmit service VLAN packets as required and communicate with the upstream device. [SwitchB-GigabitEthernet0/0/2] quit
# Configure the IP address of the VLANIF interface on SwitchB and enable DHCP.
[SwitchB] dhcp enable [SwitchB] interface vlanif 100 [SwitchB-Vlanif100] ip address 192.168.10.1 24 [SwitchB-Vlanif100] dhcp select interface [SwitchB-Vlanif100] quit [SwitchB] interface vlanif 101 [SwitchB-Vlanif101] ip address 192.168.20.1 24 [SwitchB-Vlanif101] quit
# Configure the gateway address of the Agile Controller-Campus.
[SwitchB] interface vlanif 102 [SwitchB-Vlanif102] ip address 192.168.30.1 24 [SwitchB-Vlanif102] quit
- Set the NAC mode to unified on SwitchB.
[SwitchB] authentication unified-mode //Set the NAC mode to unified. By default, the switch works in unified mode. If the switch works in common mode, the following information is displayed when this command is run to change the NAC mode. The administrator must enter y. The switch will save the configuration and restart immediately. Functions of the newly configured mode then take effect. Warning: Switching the authentication mode will take effect after system restart. Some configurations are invalid after the mode is switched. For the invalid commands, see the user manual. Save the configuration file and reboot now? [Y/N]y - Configure parameters for SwitchB to communicate with the Agile Controller-Campus (RADIUS server).
[SwitchB] radius-server template policy //Create the RADIUS server template policy. [SwitchB-radius-policy] radius-server authentication 192.168.30.2 1812 source ip-address 192.168.30.1 //Configure the IP address and port number of the RADIUS authentication server. [SwitchB-radius-policy] radius-server accounting 192.168.30.2 1813 source ip-address 192.168.30.1 //Configure the IP address and port number of the RADIUS accounting server. [SwitchB-radius-policy] radius-server shared-key cipher Admin@123 //Set the authentication key and accounting key to Admin@123. [SwitchB-radius-policy] quit [SwitchB] aaa //Enter the AAA view. [SwitchB-aaa] authentication-scheme auth //Create the authentication scheme auth. [SwitchB-aaa-authen-auth] authentication-mode radius //Set the authentication mode to RADIUS. [SwitchB-aaa-authen-auth] quit [SwitchB-aaa] accounting-scheme acco //Create the accounting scheme acco. [SwitchB-aaa-accounting-acco] accounting-mode radius //Set the accounting mode to RADIUS. [SwitchB-aaa-accounting-acco] accounting realtime 15 //Set the real-time accounting interval to 15 minutes. [SwitchB-aaa-accounting-acco] quit [SwitchB-aaa] domain portal //Create the domain portal. [SwitchB-aaa-domain-portal] authentication-scheme auth //Bind the authentication scheme auth to the domain. [SwitchB-aaa-domain-portal] accounting-scheme acco //Bind the accounting scheme acco to the domain. [SwitchB-aaa-domain-portal] radius-server policy //Bind the RADIUS server template policy to the domain. [SwitchB-aaa-domain-portal] quit [SwitchB-aaa] quit [SwitchB] domain portal //Set the domain portal as the global default domain.
- Configure MAC address + Portal authentication.
# Configure a URL template.
[SwitchB] url-template name huawei [SwitchB-url-template-huawei] url http://access.example.com:8080/portal //Configure the URL of the Portal authentication page and set the domain name of the Portal server to access.example.com. To access the pushed page more securely and quickly, you are advised to use the domain name. However, you need to configure the mapping between the domain name access.example.com and the IP address of the server on the DNS server in advance. [SwitchB-url-template-huawei] url-parameter user-ipaddress userip user-mac usermac ac-mac acmac sysname sysname //Configure parameters carried in the URL. [SwitchB-url-template-huawei] quit
# Configure parameters for SwicthB to communicate with the Agile Controller-Campus (Portal server).
[SwitchB] web-auth-server portal_huawei //Configure the Portal server template portal_huawei. [SwitchB-web-auth-server-portal_huawei] server-ip 192.168.30.2 //Configure the IP address of the Portal server. [SwitchB-web-auth-server-portal_huawei] source-ip 192.168.30.1 //Configure the IP address for the device to communicate with the Portal server. [SwitchB-web-auth-server-portal_huawei] port 50200 //Set the destination port number in the packets sent to the Portal server to 50200, which is the same as the port number in the packets received by the Portal server. The default port number in the packets sent by the switch is 50100. You must manually change the port number to 50200 for adaptation to the Portal server. [SwitchB-web-auth-server-portal_huawei] shared-key cipher Admin@123 //Configure the shared key for communication with the Portal server. The shared key must be the same as that configured on the Portal server. [SwitchB-web-auth-server-portal_huawei] url-template huawei //Bind the URL template to the Portal server template. [SwitchB-web-auth-server-portal_huawei] quit [SwitchB] web-auth-server listening-port 2000 //Configure the port number used to process Portal packets on the device. The default port number is 2000. If this port number is changed on the server, you must also change the port number on the switch accordingly. [SwitchB] portal quiet-period //Enable the quiet function for Portal authentication. If the number of times that an authentication user fails to be authenticated within 60 seconds exceeds the configured value, the device discards packets from the user for a period of time to prevent impact on the system caused by frequent authentication failures. [SwitchB] portal quiet-times 5 //Configure the maximum number of authentication failures within 60 seconds before the device quiets a Portal authentication user. [SwitchB] portal timer quiet-period 240 //Set the quiet period for Portal authentication to 240 seconds.
# Configure a Portal access profile.
[SwitchB] portal-access-profile name web1 [SwitchB-portal-acces-profile-web1] web-auth-server portal_huawei direct [SwitchB-portal-acces-profile-web1] quit
# Configure MAC access profile m1.
In a MAC access profile, a MAC address without hyphens (-) is used as the user name and password for MAC address authentication by default.
[SwitchB] mac-access-profile name m1 [SwitchB-mac-access-profile-m1] quit
# Configure the switch to allow packets sent to the DNS server and WeChat server to pass through before authentication.
The parameters dns-ip-address,dns-ip-mask,weixin-ip-address, and weixinip-mask should be configured based on site requirements.
[SwitchB] free-rule-template name default_free_rule [SwitchB-free-rule-default_free_rule] free-rule 0 destination ip dns-ip-address mask dns-ip-mask //Allow packets sent to the DNS server to pass through. [SwitchB-free-rule-default_free_rule] free-rule 1 destination ip weixin-ip-address mask weixinip-mask //Allow packets sent to the WeChat server to pass through. [SwitchB-free-rule-default_free_rule] quit
# Configure an authentication profile.
[SwitchB] authentication-profile name p1 [SwitchB-authen-profile-p1] portal-access-profile web1 //Bind the Portal access profile web1. [SwitchB-authen-profile-p1] mac-access-profile m1 //Bind the MAC access profile m1. [SwitchB-authen-profile-p1] free-rule-template default_free_rule //Bind an authentication-free rule profile. [SwitchB-authen-profile-p1] quit
# Enable Portal authentication.
[SwitchB] interface vlanif 100 [SwitchB-Vlanif100] authentication-profile p1 [SwitchB-Vlanif100] quit
# Configure the function of automatically displaying the Portal authentication page after users connect to the Wi-Fi network.

After this function is configured, mobile phones running iOS9.3.1 cannot be successfully authenticated after connecting to the Wi-Fi network, and the Wi-Fi connection is automatically disconnected. To solve this problem, run the portal captive-bypass enable command to enable the CNA bypass function. Users need to manually access any post-authentication domain, and complete the subsequent WeChat authentication after the Portal authentication page is displayed.
[SwitchB] portal captive-adaptive enable
- Configure MAC address migration.
[SwitchB] authentication mac-move enable vlan all
- Configure the Agile Controller-CampusIn addition to the preceding configurations, you need to enable MAC address-prioritized Portal authentication on the Agile Controller-Campus. The procedure is as follows:
- Choose System > Terminal Configuration > Global Parameters.
On the MAC Address-Prioritized Portal Authentication tab page, enable MAC Address-Prioritized Portal Authentication, and set Validity Period of MAC Address to 60.
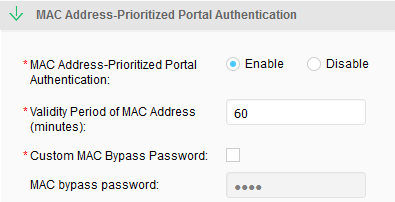
- Click OK.
- Verify the configuration.
Manually search for the specified WLAN. After completing the WeChat authentication process as prompted, the Internet can be accessed.
Configuration Files
SwitchA configuration file
# sysname SwitchA # vlan batch 100 # interface GigabitEthernet0/0/1 port link-type trunk port trunk pvid vlan 100 port trunk allow-pass vlan 100 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 100 # return
SwitchB configuration file
# sysname SwitchB # vlan batch 100 to 102 # authentication-profile name p1 mac-access-profile m1 portal-access-profile web1 free-rule-template default_free_rule authentication mac-move enable vlan all # domain portal # dhcp enable # radius-server template policy radius-server shared-key cipher %^%#v@)#XkYybF19}~4&3(rDX%va0:#G>0MDrOF^B;D+%^%# radius-server authentication 192.168.30.2 1812 source ip-address 192.168.30.1 weight 80 radius-server accounting 192.168.30.2 1813 source ip-address 192.168.30.1 weight 80 # free-rule-template name default_free_rule free-rule 0 destination ip dns-ip-address mask dns-ip-mask free-rule 1 destination ip weixin-ip-address mask weixin-ip-mask # url-template name huawei url http://access.example.com:8080/portal url-parameter user-ipaddress userip user-mac usermac ac-mac acmac sysname sysname # web-auth-server portal_huawei server-ip 192.168.30.2 port 50200 shared-key cipher %^%#vB3l&dt|S!59SdGIdcT"mwAQ!4[#Y-#{IBGbI[l:%^%# url-template huawei source-ip 192.168.30.1 # portal-access-profile name web1 web-auth-server portal_huawei direct # aaa authentication-scheme auth authentication-mode radius accounting-scheme acco accounting-mode radius accounting realtime 15 domain portal authentication-scheme auth accounting-scheme acco radius-server policy # interface Vlanif100 ip address 192.168.10.1 255.255.255.0 authentication-profile p1 dhcp select interface # interface Vlanif101 ip address 192.168.20.1 255.255.255.0 # interface Vlanif102 ip address 192.168.30.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 100 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 101 # interface GigabitEthernet0/0/3 port link-type trunk port trunk allow-pass vlan 102 # portal captive-adaptive enable portal timer quiet-period 240 portal quiet-times 5 # mac-access-profile name m1 # return