Example for Configuring Multi-mode Authentication for Wired and Wireless Users
Networking Requirements
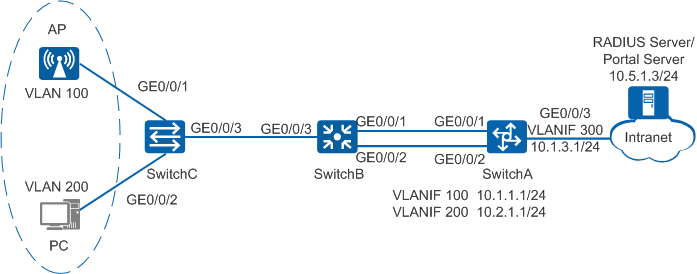
On the enterprise network shown in Figure 1, SwitchC, SwitchB, and SwitchA function as an access switch, an aggregation switch, and a core switch, respectively. SwitchA assigns IP addresses to users and APs. Wired users access the enterprise network through SwitchC, and wireless users access the enterprise network through the AP connected to SwitchC. Users can access the enterprise network only after passing 802.1X, MAC address, or Portal authentication. Authentication is not required for the AP, and therefore AP information is not stored on the authentication server.
Configuration Precautions
- This section describes only NAC configurations on switches. The AP and WLAN service configurations are not provided here.
The RADIUS authentication and accounting keys configured on the RADIUS server must be the same as the shared key of the RADIUS server configured on the device.
- The Portal shared key and port number configured on the Portal server must be the same as the shared key configured on the device and the port number used by the device to listen to Portal protocol packets.
- The default outbound interface IP address of the device is used as the source IP address for sending RADIUS packets to the RADIUS server. This IP address must be the same as the device IP address configured on the RADIUS server. You can change the source IP address as follows:
- Run the radius-server authentication ip-address port source command to configure a RADIUS authentication server and specify the source IP address used by the device to send RADIUS packets to the RADIUS authentication server.
- Run the radius-server accounting ip-address port source command to configure a RADIUS accounting server and specify the source IP address used by the device to send RADIUS packets to the RADIUS accounting server.
- The default outbound interface IP address of the device is used as the source IP address for sending Portal packets to the Portal server. This IP address must be the same as the device IP address configured on the Portal server. You can run the source-interface or source-ip command to change this IP address.
- In this example, Huawei's Agile Controller-Campus (required version: V100R003C60) acts as the RADIUS/Portal server. For details, see the Agile Controller-Campus Product Documentation.
Configuration Roadmap
- Configure network connectivity on switches.
- Configure the DHCP function on SwitchA to assign IP addresses to users and APs.
- Configure AAA on SwitchA to implement RADIUS authentication, authorization, and accounting for STAs, but not the AP.
- Configure 802.1X, MAC address, and Portal authentication on SwitchA to authenticate users.
Procedure
- Configure network connectivity.
# On SwitchA, create VLANs and configure the allowed VLANs on interfaces.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] vlan batch 100 200 300 [SwitchA] interface eth-trunk 10 [SwitchA-Eth-Trunk10] port link-type trunk [SwitchA-Eth-Trunk10] port trunk allow-pass vlan 100 200 [SwitchA-Eth-Trunk10] quit [SwitchA] interface gigabitethernet 0/0/1 [SwitchA-GigabitEthernet0/0/1] eth-trunk 10 [SwitchA-GigabitEthernet0/0/1] quit [SwitchA] interface gigabitethernet 0/0/2 [SwitchA-GigabitEthernet0/0/2] eth-trunk 10 [SwitchA-GigabitEthernet0/0/2] quit [SwitchA] interface gigabitethernet 0/0/3 [SwitchA-GigabitEthernet0/0/3] port link-type trunk [SwitchA-GigabitEthernet0/0/3] port trunk allow-pass vlan 300 [SwitchA-GGigabitEthernet0/0/3] quit [SwitchA] interface vlanif 100 [SwitchA-Vlanif100] ip address 10.1.1.1 24 [SwitchA-Vlanif100] quit [SwitchA] interface vlanif 200 [SwitchA-Vlanif200] ip address 10.2.1.1 24 [SwitchA-Vlanif200] quit [SwitchA] interface vlanif 300 [SwitchA-Vlanif300] ip address 10.3.1.1 24 [SwitchA-Vlanif300] quit [SwitchA] ip route-static 0.0.0.0 0.0.0.0 10.3.1.2
# On SwitchB, configure transparent transmission of 802.1X packets, create VLANs, and configure the allowed VLANs on interfaces.

SwitchB is a Layer 2 switch. To ensure that 802.1X authentication can be performed for users, configure transparent transmission of 802.1X packets on SwitchB. In this example, SwitchB is an S5720-LI, S5735-L, S5735S-L, and S5735S-L-M.
<HUAWEI> system-view [HUAWEI] sysname SwitchB [SwitchB] vlan batch 100 200 [SwitchB] l2protocol-tunnel user-defined-protocol 802.1X protocol-mac 0180-c200-0003 group-mac 0100-0000-0002 [SwitchB] interface eth-trunk 10 [SwitchB-Eth-Trunk10] l2protocol-tunnel user-defined-protocol 802.1X enable [SwitchB-Eth-Trunk10] bpdu enable [SwitchB-Eth-Trunk10] port link-type trunk [SwitchB-Eth-Trunk10] port trunk allow-pass vlan 100 200 [SwitchB-Eth-Trunk10] quit [SwitchB] interface gigabitethernet 0/0/1 [SwitchB-GigabitEthernet0/0/1] eth-trunk 10 [SwitchB-GigabitEthernet0/0/1] quit [SwitchB] interface gigabitethernet 0/0/2 [SwitchB-GigabitEthernet0/0/2] eth-trunk 10 [SwitchB-GigabitEthernet0/0/2] quit [SwitchB] interface gigabitethernet 0/0/3 [SwitchB-GigabitEthernet0/0/3] l2protocol-tunnel user-defined-protocol 802.1X enable [SwitchB-GigabitEthernet0/0/3] bpdu enable [SwitchB-GigabitEthernet0/0/3] port link-type trunk [SwitchB-GigabitEthernet0/0/3] port trunk allow-pass vlan 100 200 [SwitchB-GigabitEthernet0/0/3] quit
# On SwitchC, configure transparent transmission of 802.1X packets, create VLANs, and configure the allowed VLANs on interfaces.

SwitchC is a Layer 2 switch. To ensure that 802.1X authentication can be performed for users, configure transparent transmission of 802.1X packets on SwitchC. In this example, SwitchC is an S5720-LI, S5735-L, S5735S-L, and S5735S-L-M.
<HUAWEI> system-view [HUAWEI] sysname SwitchC [SwitchC] vlan batch 100 200 [SwitchC] l2protocol-tunnel user-defined-protocol 802.1X protocol-mac 0180-c200-0003 group-mac 0100-0000-0002 [SwitchC] interface gigabitethernet 0/0/1 [SwitchC-GigabitEthernet0/0/1] l2protocol-tunnel user-defined-protocol 802.1X enable [SwitchC-GigabitEthernet0/0/1] bpdu enable [SwitchC-GigabitEthernet0/0/1] port link-type access [SwitchC-GigabitEthernet0/0/1] port default vlan 100 [SwitchC-GigabitEthernet0/0/1] quit [SwitchC] interface gigabitethernet 0/0/2 [SwitchC-GigabitEthernet0/0/2] l2protocol-tunnel user-defined-protocol 802.1X enable [SwitchC-GigabitEthernet0/0/2] bpdu enable [SwitchC-GigabitEthernet0/0/2] port link-type access [SwitchC-GigabitEthernet0/0/2] port default vlan 200 [SwitchC-GigabitEthernet0/0/2] quit [SwitchC] interface gigabitethernet 0/0/3 [SwitchC-GigabitEthernet0/0/3] l2protocol-tunnel user-defined-protocol 802.1X enable [SwitchC-GigabitEthernet0/0/3] bpdu enable [SwitchC-GigabitEthernet0/0/3] port link-type trunk [SwitchC-GigabitEthernet0/0/3] port trunk allow-pass vlan 100 200 [SwitchC-GigabitEthernet0/0/3] quit
- Configure DHCP on SwitchA.
Configure VLANIF 100, VLANIF 200, and VLANIF300 to assign IP addresses to APs, wired users, and wireless users, respectively.
[SwitchA] dhcp enable [SwitchA] interface vlanif 100 [SwitchA-Vlanif100] dhcp select interface [SwitchA-Vlanif100] quit [SwitchA] interface vlanif 200 [SwitchA-Vlanif200] dhcp select interface [SwitchA-Vlanif200] quit [SwitchA] interface vlanif 300 [SwitchA-Vlanif200] dhcp select interface [SwitchA-Vlanif300] quit
- Configure AAA on SwitchA.
- Configure 802.1X, MAC address, and Portal authentication on SwitchA.# Change the NAC mode to unified.
[SwitchA] authentication unified-mode

By default, the unified mode is enabled. After you change the NAT mode between common and unified, the device automatically restarts.
# Configure a MAC access profile.[SwitchA] mac-access-profile name m1 [SwitchA-mac-access-profile-m1] quit
# Configure an 802.1X access profile.[SwitchA] dot1x-access-profile name d1 [SwitchA-dot1x-access-profile-d1] dot1x authentication-method eap [SwitchA-dot1x-access-profile-d1] quit
# Configure a Portal server template named abc.[SwitchA] web-auth-server abc [SwitchA-web-auth-server-abc] server-ip 10.5.1.3 [SwitchA-web-auth-server-abc] port 50200 [SwitchA-web-auth-server-abc] url http://10.5.1.3:8080/portal [SwitchA-web-auth-server-abc] shared-key cipher Huawei@123 [SwitchA-web-auth-server-abc] quit
# Configure a Portal access profile named web1.
[SwitchA] portal-access-profile name web1 [SwitchA-portal-acces-profile-web1] web-auth-server abc direct [SwitchA-portal-acces-profile-web1] quit
# Bind the MAC access profile, 802.1X access profile, and Portal access profile to the authentication profile p1.[SwitchA] authentication-profile name p1 [SwitchA-authen-profile-p1] mac-access-profile m1 [SwitchA-authen-profile-p1] dot1x-access-profile d1 [SwitchA-authen-profile-p1] portal-access-profile web1
# Enable MAC address bypass authentication and configure a forcible authentication domain.
[SwitchA-authen-profile-p1] authentication dot1x-mac-bypass [SwitchA-authen-profile-p1] access-domain isp force [SwitchA-authen-profile-p1] quit
# Bind the authentication profile to an interface.[SwitchA] interface eth-trunk 10 [SwitchA-Eth-Trunk10] authentication-profile p1 [SwitchA-Eth-Trunk10] quit
- Configure Agile Controller-Campus.
- Log in to Agile Controller-Campus.
- Choose Resource > User > User Management and click Add to create a common account.
- Choose Resource > Device > Device Management, click Add, and set device parameters, including the SwitchA IP address and RADIUS authentication and accounting parameters.
- Choose System > Terminal Configuration > Global Parameters. Under Configure MAC Address-Prioritized Portal Authentication, enable MAC address-prioritized Portal authentication and set the MAC address validity period to 60 minutes.
- Verify the configuration.
A user can access the network after the authentication succeeds.
After the user goes online, you can run the display access-user command on the device to check the online user information.