Example for Configuring 802.1X and MAC Address Authentication to Control Internal User Access to the Enterprise Network (with Unauthenticated AP)
Networking Requirements
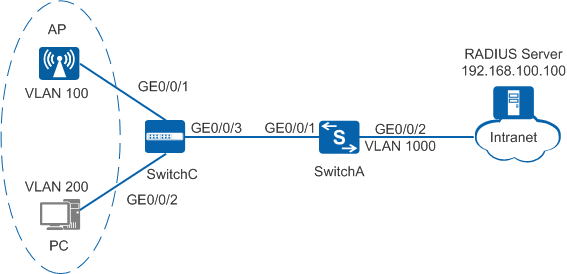
Wired and wireless users are connected to the enterprise network through switches and APs connected to the switches respectively, but users can access the enterprise network only after being authenticated. AP information is not stored on the authentication server. Therefore, the AP does not need to be authenticated.
Figure 1 Networking Diagram

Procedure
- Configure the aggregation switch.
- Create and configure a RADIUS server template,
an AAA authentication scheme, and an authentication domain.
# Create and configure the RADIUS server template rd1.
[SwitchA] radius-server template rd1 [SwitchA-radius-rd1] radius-server authentication 192.168.100.100 1812 [SwitchA-radius-rd1] radius-server accounting 192.168.100.100 1813 [SwitchA-radius-rd1] radius-server shared-key cipher Huawei@2014 [SwitchA-radius-rd1] quit
# Create the AAA authentication scheme abc and set the authentication mode to RADIUS.[SwitchA] aaa [SwitchA-aaa] authentication-scheme abc [SwitchA-aaa-authen-abc] authentication-mode radius [SwitchA-aaa-authen-abc] quit
# Configure the accounting scheme acco1. You must set the accounting mode to RADIUS so that the RADIUS server can maintain the account status, such as login, log-off, and forced log-off.[SwitchA-aaa] accounting-scheme acco1 [SwitchA-aaa-accounting-acco1] accounting-mode radius [SwitchA-aaa-accounting-acco1] accounting realtime 15 //Set the interval of real-time accounting to 15 minutes. [SwitchA-aaa-accounting-acco1] quit# Create the authentication domain isp, and bind the AAA authentication scheme abc, accounting scheme acco1, and RADIUS server template rd1 to the domain.[SwitchA-aaa] domain isp [SwitchA-aaa-domain-isp] authentication-scheme abc [SwitchA-aaa-domain-isp] accounting-scheme acco1 [SwitchA-aaa-domain-isp] radius-server rd1 [SwitchA-aaa-domain-isp] quit [SwitchA-aaa] quit
# Configure the global default domain isp. During access authentication, enter a user name in the format user@isp to perform AAA authentication in the domain isp. If the user name does not contain a domain name or contains an invalid domain name, the user is authenticated in the default domain.[SwitchA] domain isp
- Configure non-authentication for AP.
# Create the AAA authentication scheme noauthen and set the authentication mode to none.
[SwitchA] aaa [SwitchA-aaa] authentication-scheme noauthen [SwitchA-aaa-authen-noauthen] authentication-mode none [SwitchA-aaa-authen-noauthen] quit
# Create an authentication domain of the AP.[SwitchA-aaa] domain ap_noauthen [SwitchA-aaa-domain-ap_noauthen] authentication-scheme noauthen [SwitchA-aaa-domain-ap_noauthen] quit [SwitchA-aaa] quit
# Configure the user context identification function.[SwitchA] access-context profile enable //Enable the user context identification function. [SwitchA] access-context profile name ap_access //Create a user context profile. [SwitchA-access-context-ap_access] if-match vlan-id 100 //Configure the VLAN-based identification policy. [SwitchA-access-context-ap_access] quit [SwitchA] access-author policy name ap_noauthen //Create the user authentication event authorization policy. [SwitchA-access-author-ap_noauthen] match access-context-profile ap_access action access-domain ap_noauthen //Configure an access user's authentication domain based on the user context profile. [SwitchA-access-author-ap_noauthen] quit [SwitchA] access-author policy ap_noauthen global //Apply the user authentication event authorization policy.
- Enable 802.1X and MAC address authentication.
# Switch the NAC mode to unified.
[SwitchA] authentication unified-mode

By default, the unified mode is used. After the NAC mode is changed, the device automatically restarts.
# Configure a MAC access profile.[SwitchA] mac-access-profile name m1 [SwitchA-mac-access-profile-m1] quit
# Configure an 802.1X access profile.
By default, an 802.1X access profile uses the EAP authentication mode. Ensure that the RADIUS server supports EAP; otherwise, the server cannot process 802.1X authentication request packets.
[SwitchA] dot1x-access-profile name d1 [SwitchA-dot1x-access-profile-d1] quit
# Configure an authentication profile.[SwitchA] authentication-profile name p1 [SwitchA-authen-profile-p1] mac-access-profile m1 //Bind a MAC access profile. [SwitchA-authen-profile-p1] dot1x-access-profile d1 //Bind an 802.1X access profile. [SwitchA-authen-profile-p1] quit
# Bind the authentication profile to the GE0/0/1.[SwitchA] interface gigabitethernet 0/0/1 [SwitchA-Gigabitethernet0/0/1] authentication-profile p1 //Bind a authentication profile and enable 802.1X + MAC address authentication. [SwitchA-Gigabitethernet0/0/1] quit
- Create and configure a RADIUS server template,
an AAA authentication scheme, and an authentication domain.