Example for Configuring 802.1X Authentication Escape (Used When Both the Active and Standby RADIUS Servers Are Faulty)
Networking Requirements
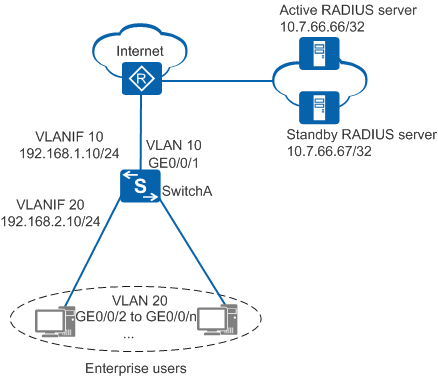
On the enterprise network shown in Figure 1, SwitchA functions as the access device, and two RADIUS servers are deployed for 802.1X + RADIUS authentication of users on the enterprise network. Users can access the Internet only after being successfully authenticated. The administrator has the following user authentication requirements: When the two RADIUS servers are faulty, users bypass authentication and are granted the same network access rights as they are successfully authenticated. After the RADIUS servers recover, users are re-authenticated and re-authorized by the RADIUS servers.
Configuration Precautions
- This section describes only NAC configurations on SwitchA. The RADIUS server configurations are not provided here.
The RADIUS authentication and accounting keys configured on the RADIUS server must be the same as the shared key of the RADIUS server configured on the device.
- The default outbound interface IP address of the device is used as the source IP address for sending RADIUS packets to the RADIUS server. This IP address must be the same as the device IP address configured on the RADIUS server. You can change the source IP address as follows:
- Run the radius-server authentication ip-address port source command to configure a RADIUS authentication server and specify the source IP address used by the device to send RADIUS packets to the RADIUS authentication server.
- Run the radius-server accounting ip-address port source command to configure a RADIUS accounting server and specify the source IP address used by the device to send RADIUS packets to the RADIUS accounting server.
- When the authentication event authen-server-up action re-authen command is configured, you also need to run the radius-server testuser command to enable automatic detection. If automatic detection is not enabled and the authentication server status changes from Down to Up, the device cannot re-authenticate users in authentication escape state.
- When VLAN-based authorization is used, ensure that the interfaces added to the VLAN are hybrid interfaces and the undo authentication pre-authen-access enable command has been run in the system view to disable the pre-connection function.
- You can trigger the RADIUS server Down event as follows:
[SwitchA] radius-server dead-interval 7 [SwitchA] radius-server dead-count 1
Run the test-aaa command for four times. The RADIUS server then goes Down.
Configuration Roadmap
- Configure network connectivity to ensure that devices are routable to each other.
- Configure AAA to implement RADIUS authentication, authorization, and accounting for users.
- Configure 802.1X authentication, configure escape rights granted to users when the RADIUS servers are faulty, and configure the re-authentication function when the RADIUS servers recover.
Procedure
- Configure network connectivity.
# Create VLANs, configure the allowed VLANs on interfaces, and configure IP addresses for interfaces.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] vlan batch 10 20 [SwitchA] interface gigabitethernet 0/0/2 [SwitchA-GigabitEthernet0/0/2] port link-type hybrid [SwitchA-GigabitEthernet0/0/2] port hybrid pvid vlan 20 [SwitchA-GigabitEthernet0/0/2] port hybrid untagged vlan 20 [SwitchA-GigabitEthernet0/0/2] quit [SwitchA] interface vlanif 20 [SwitchA-Vlanif20] ip address 192.168.2.10 24 [SwitchA-Vlanif20] quit [SwitchA] interface gigabitethernet 0/0/1 [SwitchA-GigabitEthernet0/0/1] port link-type trunk [SwitchA-GigabitEthernet0/0/1] port trunk allow-pass vlan 10 [SwitchA-GigabitEthernet0/0/1] quit [SwitchA] interface vlanif 10 [SwitchA-Vlanif10] ip address 192.168.1.10 24 [SwitchA-Vlanif10] quit
# Configure a route destined for RADIUS servers. In this example, the next hop is 192.168.1.1.
[SwitchA] ip route-static 10.7.66.0 255.255.255.0 192.168.1.1 - Configure AAA.
# Create a RADIUS server template named controller.
[SwitchA] radius-server template controller# Configure IP addresses and port numbers of the active and standby RADIUS authentication and accounting servers, set the algorithm for selecting RADIUS servers to master/backup, and set the RADIUS authentication key.
[SwitchA-radius-controller] radius-server authentication 10.7.66.66 1812 weight 80 [SwitchA-radius-controller] radius-server accounting 10.7.66.66 1813 weight 80 [SwitchA-radius-controller] radius-server authentication 10.7.66.67 1812 weight 40 [SwitchA-radius-controller] radius-server accounting 10.7.66.67 1813 weight 40 [SwitchA-radius-controller] radius-server algorithm master-backup [SwitchA-radius-controller] radius-server shared-key cipher Huawei@123
# Enable automatic detection.
[SwitchA-radius-controller] radius-server testuser username test1 password cipher abc@123# Configure the automatic detection interval and detection packet timeout interval for RADIUS servers in Down state. (In this example, the default values are used.)
[SwitchA-radius-controller] radius-server detect-server interval 60 [SwitchA-radius-controller] radius-server detect-server timeout 3
# Configure the retransmission times and timeout interval for RADIUS authentication request packets. (In this example, the default values are used.)
[SwitchA-radius-controller] radius-server retransmit 3 timeout 5 [SwitchA-radius-controller] quit
# Configure the conditions for setting the status of a RADIUS server to Down. (In this example, the default values are used.)
[SwitchA] radius-server dead-interval 5 [SwitchA] radius-server dead-count 2 [SwitchA] radius-server detect-cycle 2 [SwitchA] radius-server max-unresponsive-interval 300
# Configure an authentication scheme named auth and set the authentication mode to RADIUS.
[SwitchA] aaa [SwitchA-aaa] authentication-scheme auth [SwitchA-aaa-authen-auth] authentication-mode radius [SwitchA-aaa-authen-auth] quit
# Configure an accounting scheme named acc and set the accounting mode to RADIUS.
[SwitchA-aaa] accounting-scheme acc [SwitchA-aaa-accounting-acc] accounting-mode radius [SwitchA-aaa-accounting-acc] quit
# Configure a domain named huawei, and apply the authentication scheme auth, accounting scheme acc, and RADIUS server template controller to the domain.
[SwitchA-aaa] domain huawei [SwitchA-aaa-domain-huawei] authentication-scheme auth [SwitchA-aaa-domain-huawei] accounting-scheme acc [SwitchA-aaa-domain-huawei] radius-server controller [SwitchA-aaa-domain-huawei] quit [SwitchA-aaa] quit
- Configure 802.1X authentication.
# Change the NAC mode to unified.

By default, the unified mode is enabled. After you change the NAT mode between common and unified, the device automatically restarts.
[SwitchA] authentication unified-mode# Configure an 802.1X access profile named d1 and set the client authentication timeout interval to 30 seconds.[SwitchA] dot1x-access-profile name d1 [SwitchA-dot1x-access-profile-d1] dot1x authentication-method eap [SwitchA-dot1x-access-profile-d1] dot1x timer client-timeout 30 [SwitchA-dot1x-access-profile-d1] quit
# Bind the 802.1X access profile d1 to the authentication profile, and configure the forcible authentication domain huawei for users using this authentication profile.

After a forcible domain is configured in an authentication profile, users using this authentication profile are authenticated in the domain no matter whether the user names carry domain names or carry what kind of domain names.
[SwitchA] authentication-profile name p1 [SwitchA-authen-profile-p1] dot1x-access-profile d1 [SwitchA-authen-profile-p1] access-domain huawei force [SwitchA-authen-profile-p1] quit
# Configure the escape rights granted to users when RADIUS servers are faulty, and enable the re-authentication function when the RADIUS servers recover. In this example, VLAN-based authorization is used for users in escape state. For other authorization modes, see (Optional) Configuring Authentication Event Authorization Information.
[SwitchA] authentication-profile name p1 [SwitchA-authen-profile-p1] authentication event authen-server-down action authorize vlan 20 [SwitchA-authen-profile-p1] authentication event authen-server-up action re-authen [SwitchA-authen-profile-p1] quit
# Disable the function of keeping users who fail to be authenticated and do not have any network access rights in the pre-connection state.
[SwitchA] undo authentication pre-authen-access enable# Bind the authentication profile p1 to interfaces GE0/0/2 to GE0/0/n, and enable 802.1X authentication. The following uses the configuration of GE0/0/2 as an example:
[SwitchA] interface gigabitethernet 0/0/2 [SwitchA-GigabitEthernet0/0/2] authentication-profile p1 [SwitchA-GigabitEthernet0/0/2] quit
- Verify the configuration.
- A user starts a terminal and initiates 802.1X authentication. After the authentication is successful, the user can access the Internet.
- When the active RADIUS server is Down, the standby RADIUS server authorizes the user so that the user can access the Internet. When both the active and standby RADIUS servers are Down, the user enters the escape state and can access specified network resources.
- After the user goes online, run the display access-user mac-address command on SwitchA to check information about the online user.