802.1X Authentication Protocol
Overview
In the 802.1X authentication system,
the client, access device, and authentication server exchange information
using the Extensible Authentication Protocol (EAP). EAP can run without
an IP address over various bottom layers, including the data link
layer and upper-layer protocols (such as UDP and TCP). This offers
great flexibility to 802.1X authentication.
- The EAP packets transmitted between the client and access device are encapsulated in EAPoL format and transmitted across the LAN.
- You can determine to use either of the following authentication
modes between the access device and authentication server based on
the client support and network security requirements:
- EAP termination mode: The access device terminates EAP packets and encapsulates them into RADIUS packets. The authentication server then uses the standard RADIUS protocol to implement authentication, authorization, and accounting.
- EAP relay mode: The access device directly encapsulates the received EAP packets into RADIUS using EAP over RADIUS (EAPoR) packets, and then transmits these packets over a complex network to the authentication server.
EAP Packet
Figure 1 EAP packet
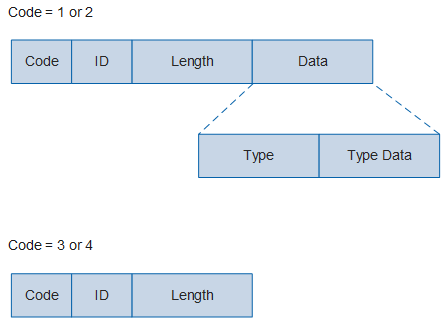

Field |
Bytes |
Description |
|---|---|---|
| Code | 1 | Indicates the type of an EAP data packet. The options are as
follows:
|
| ID | 1 | Is used to match a Response packet with the corresponding Request packet. |
| Length | 2 | Indicates the length of an EAP data packet, including the Code, ID, Length, and Data fields. Bytes outside the range of the Length field are treated as padding at the data link layer and ignored on reception. |
| Data | Zero or multiple bytes | The format of the Data field is determined by the Code field.
|
Type Field Value |
Packet Type |
Description |
|---|---|---|
| 1 | Identity | Requests or returns the user name information entered by a user. |
| 2 | Notification | Transmits notification information about some events, such as password expiry and account locking. It is an optional message. |
| 3 | NAK | Indicates negative acknowledgment and is used only in a Response packet. For example, if the access device uses an authentication method not supported by the client to initiate a request, the client can send a Response/NAK packet to notify the access device of the authentication methods supported by the client. |
| 4 | MD5-Challenge | Indicates that the authentication method is MD5-Challenge. |
| 5 | OTP | Indicates that the authentication method is One-Time Password (OTP). For example, during e-banking payment, the system sends a one-time password through an SMS message. |
| 6 | GTC | Indicates that the authentication method is Generic Token Card (GTC). A GTC is similar to an OTP except that a GTC usually corresponds to an actual device. For example, many banks in China provide a dynamic token for users who apply for e-banking. This token is a GTC. |
| 13 | EAP-TLS | Indicates that the authentication method is EAP-TLS. |
| 21 | EAP-TTLS | Indicates that the authentication method is EAP-TTLS. |
| 25 | EAP-PEAP | Indicates that the authentication method is EAP-PEAP. |
| 254 | Expanded Types | Indicates an expanded type, which can be customized by vendors. |
| 255 | Experimental use | Indicates a type for experimental use. |
EAPoL Packet
EAPoL is a packet encapsulation format defined by the 802.1X protocol. EAPoL is mainly used to transmit EAP packets over a LAN between the client and access device. The following figure shows the format of an EAPoL packet.Figure 2 EAPoL packet
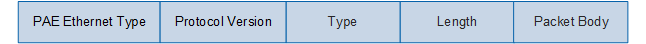

Field |
Bytes |
Description |
|---|---|---|
| PAE Ethernet Type | 2 | Indicates the protocol type. The value is fixed at 0x888E. |
| Protocol Version | 1 | Indicates the protocol version number supported by the EAPoL
packet sender.
|
| Type | 1 | Indicates the type of an EAPoL data packet:
Note that the EAPoL-Start, EAPoL-Logoff, and EAPoL-Key packets are transmitted only between the client and access device. |
| Length | 2 | Indicates the data length, that is, the length of the Packet Body field, in bytes. The value 0 indicates that the Packet Body field does not exist. For the EAPoL-Start and EAPoL-Logoff packets, the values of the Length field are both 0. |
| Packet Body | 2 | Indicates the data content. |
EAPoR
To support EAP relay, the following attributes are added to the RADIUS protocol:
- EAP-Message: is used to encapsulate EAP packets.
- Message-Authenticator: is used to authenticate and verify authentication packets to protect against spoofing of invalid packets.
The following figure shows the format of an EAPoR packet.
Figure 3 EAPoR packet
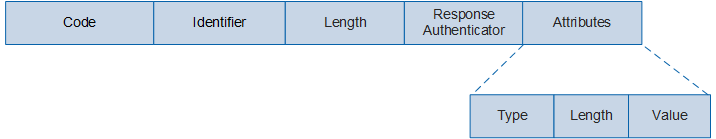

Field |
Bytes |
Description |
|---|---|---|
| Code | 1 | Indicates the type of a RADIUS packet. |
| Identifier | 1 | Is used to match a Response packet with the corresponding Request packet, and to detect the Request packet retransmitted within a certain period. After the client sends a Request packet, the authentication server sends a Response packet with the same Identifier value as the Request packet. |
| Length | 2 | Indicates the length of a RADIUS packet. Bytes outside the range of the Length field are treated as padding and ignored on reception. If the length of a received packet is less than the Length value, the packet is discarded. |
| Response Authenticator | 16 | Is used to verify the Response packet sent by the RADIUS server and encrypt the user password. |
| Attributes | Variable length | Indicates the packet content body, which carries authentication, authorization, and accounting information and provides configuration details of the Request and Response packets. The Attributes field may contain multiple attributes, each of which consists of Type, Length, and Value.
|
Guidelines for Selecting Authentication Modes
- The EAP relay mode simplifies the processing on the access device and supports various authentication methods. However, the authentication server must support EAP and have high processing capability. The commonly used authentication modes include EAP-TLS, EAP-TTLS, and EAP-PEAP. EAP-TLS has the highest security because it requires a certificate to be loaded on both the client and authentication server. EAP-TTLS and EAP-PEAP are easier to deploy since the certificate needs to be loaded only on the authentication server, but not the client.
- The EAP termination mode is advantageous in that mainstream RADIUS servers support Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP) authentication, eliminating the need for server upgrade. However, the workload on the access device is heavy because it needs to extract the client authentication information from the EAP packets sent by the client and encapsulate the information using the standard RADIUS protocol. In addition, the access device does not support other EAP authentication methods except MD5-Challenge. In CHAP authentication, passwords are transmitted in cipher text; in PAP authentication, passwords are transmitted in plain text. CHAP provides higher security and is recommended.