Example for Configuring Automatic Local Certificate Application Using SCEP
Networking Requirements
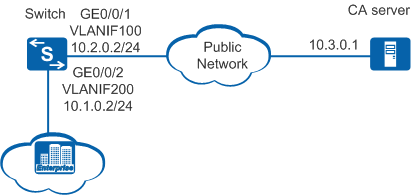
On an enterprise network shown in Figure 1, the Switch is located at the edge to function as the egress gateway and a CA server is located on the public network. The network administrator manually applies for a local certificate from the CA server in online mode.
The network administrator wants to use a simple and fast method to apply for a local certificate, and the certificate can be automatically imported to the memory. In addition, the certificate needs to be automatically updated before expiration. The automatic certificate application through SCEP can be configured to meet these requirements.

This example provides only the configurations on Switch. For the configurations on the CA server, see the CA server product manual. In this example, the CA server runs Windows Server 2008 with the built-in Certification Services and with the SCEP plugin installed.
Configuration Roadmap
The configuration roadmap is as follows:
- Assign IP addresses to interfaces and static routes to the CA server so that the Switch and CA server can communicate with each other.
- Create an RSA key pair so that the local certificate application request contains the public key.
- Configure the PKI entity and related information to identify the PKI entity.
- Configure certificate application through SCEP and automatic certificate update, automatic certificate installation, and automatic certificate update.
Data Preparation
Obtain the fingerprint and challenge password from the CA server in offline mode. In this example, the digital fingerprint is e71add0744360e91186b828412d279e06dcc15a4ab4bb3d13842820396b526a0 and challenge password is 6AE73F21E6D3571D.
For example, from a CA server running Windows Server 2008, you can obtain the digital fingerprint at http://host:port/certsrv/mscep_admin/, in which host indicates the server's IP address and port indicates the port number.
Procedure
- Assign IP addresses to interfaces and configure static routes to the CA server.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] vlan batch 100 200 [Switch] interface vlanif 100 [Switch-Vlanif100] ip address 10.2.0.2 255.255.255.0 [Switch-Vlanif100] quit [Switch] interface vlanif 200 [Switch-Vlanif200] ip address 10.1.0.2 255.255.255.0 [Switch-Vlanif200] quit [Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] port link-type trunk [Switch-GigabitEthernet0/0/1] port trunk allow-pass vlan 100 [Switch-GigabitEthernet0/0/1] quit [Switch] interface gigabitethernet 0/0/2 [Switch-GigabitEthernet0/0/2] port link-type trunk [Switch-GigabitEthernet0/0/2] port trunk allow-pass vlan 200 [Switch-GigabitEthernet0/0/2] quit [Switch] ip route-static 10.3.0.0 255.255.255.0 10.2.0.1
- Create an RSA key pair.
# Create a 2048-bit RSA key pair named rsa_scep and allow it to be exported.
[Switch] pki rsa local-key-pair create rsa_scep exportable Info: The name of the new key-pair will be: rsa_scep The size of the public key ranges from 2048 to 4096. Input the bits in the modules:2048 Generating key-pairs... ..................+++ .......................+++
- Configure a PKI entity to identify a certificate applicant.
# Configure the PKI entity user01.
[Switch] pki entity user01 [Switch-pki-entity-user01] common-name hello [Switch-pki-entity-user01] country cn [Switch-pki-entity-user01] email user@test.abc.com [Switch-pki-entity-user01] fqdn test.abc.com [Switch-pki-entity-user01] ip-address 10.2.0.2 [Switch-pki-entity-user01] state jiangsu [Switch-pki-entity-user01] organization huawei [Switch-pki-entity-user01] organization-unit info [Switch-pki-entity-user01] quit
- Apply for and update the certificate using SCEP.
[Switch] pki realm abc [Switch-pki-realm-abc] ca id ca_root [Switch-pki-realm-abc] entity user01 [Switch-pki-realm-abc] fingerprint sha256 e71add0744360e91186b828412d279e06dcc15a4ab4bb3d13842820396b526a0 [Switch-pki-realm-abc] enrollment-url http://10.3.0.1:80/certsrv/mscep/mscep.dll ra [Switch-pki-realm-abc] rsa local-key-pair rsa_scep [Switch-pki-realm-abc] enrollment-request signature message-digest-method sha-384 [Switch-pki-realm-abc] password cipher 6AE73F21E6D3571D
- Enable automatic certificate enrollment and configure the certificate to be updated when 60% of the validity period is passed and the RSA key pair is updated together with the certificate.
[Switch-pki-realm-abc] auto-enroll 60 regenerate 2048 [Switch-pki-realm-abc] quit
Before obtaining and installing a local certificate, the device obtains and installs a CA certificate first. The CA and local certificates are named abc_ca.cer and abc_local.cer.
- Verify the configuration.
Configuration Files
Switch configuration file
#
sysname Switch
#
vlan batch 100 200
#
interface Vlanif100
ip address 10.2.0.2 255.255.255.0
#
interface Vlanif200
ip address 10.1.0.2 255.255.255.0
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 100
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 200
#
ip route-static 10.3.0.0 255.255.255.0 10.2.0.1
#
pki realm abc
ca id ca_root
enrollment-url http://10.3.0.1:80/certsrv/mscep/mscep.dll ra
entity user01
fingerprint sha256 e71add0744360e91186b828412d279e06dcc15a4ab4bb3d13842820396b526a0
rsa local-key-pair rsa_scep
password cipher %^%#\1HN-bn(k;^|O85OAtYF3(M4%^%#
auto-enroll 60 regenerate
enrollment-request signature message-digest-method sha-384
#
pki entity user01
country CN
state jiangsu
organization huawei
organization-unit info
common-name hello
fqdn test.abc.com
ip-address 10.2.0.2
email user@test.abc.com
#
return