Example for Configuring Initial Application of Local Certificate Using CMPv2
Networking Requirements
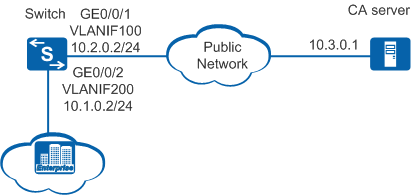
On an enterprise network shown in Figure 1, the Switch is located at the edge to function as the egress gateway. The Switch uses CMPv2 to apply for a local certificate for the first time from the CA server located on the public network. The local certificate will be automatically downloaded to the device storage.

This example provides only the configurations on Switch. For the configurations on the CA server, see the CA server product manual.
Ensure that the devices are routable before the configuration.
Configuration Roadmap
The configuration roadmap is as follows:
- Create an RSA key pair so that the local certificate application request contains the public key.
- Configure the PKI entity and related information to identify the PKI entity.
- Configure certificate application and automatic update using CMPv2 and use the MAC to authenticate messages so that the device can automatically download the CA and local certificates.
- Install the CA and local certificates to make the certificates effective. That is, the device can use the certificates to protect communication data.
Data Preparation
To complete the configuration, you need the following data:
CA name
Subject of the CA certificate
Reference and secret values of the MAC
Obtained from the CMPv2 server in out-of-band mode.
Procedure
- Create an RSA key pair.
# Create a 2048-bit RSA key pair named rsa_cmp and allow it to be exported.
[Switch] pki rsa local-key-pair create rsa_cmp exportable Info: The name of the new key-pair will be: rsa_cmp The size of the public key ranges from 2048 to 4096. Input the bits in the modules:2048 Generating key-pairs... ...........+++ ...........+++
- Configure a PKI entity to identify the certificate applicant.
# Configure the PKI entity user01.
[Switch] pki entity user01 [Switch-pki-entity-user01] common-name hello [Switch-pki-entity-user01] country cn [Switch-pki-entity-user01] email user@test.abc.com [Switch-pki-entity-user01] fqdn test.abc.com [Switch-pki-entity-user01] ip-address 10.2.0.2 [Switch-pki-entity-user01] state jiangsu [Switch-pki-entity-user01] organization huawei [Switch-pki-entity-user01] organization-unit info [Switch-pki-entity-user01] quit
- Configure the PKI realm.
[Switch] pki realm abc [Switch-pki-realm-abc] quit
- Configure the CMP session.
# Create the CMP session named cmp.
[Switch] pki cmp session cmp# Specify the pki entity name referenced by the CMP session.
[Switch-pki-cmp-session-cmp] cmp-request entity user01# Configure a CA name, for example, C=cn,ST=beijing,L=SD,O=BB,OU=BB,CN=BB.

The field order in the CA name must be the same as that in the CA certificate; otherwise, the server considers the CA name invalid.
[Switch-pki-cmp-session-cmp] cmp-request ca-name "C=cn,ST=beijing,L=SD,O=BB,OU=BB,CN=BB"# Configure the URL for certificate application.
[Switch-pki-cmp-session-cmp] cmp-request server url http://10.3.0.1:8080# Specify the RSA key pair used for certificate application and configure the device to update the RSA key pair together with the certificate.
[Switch-pki-cmp-session-cmp] cmp-request rsa local-key-pair rsa_cmp regenerate# Specify a PKI domain to which the CMP server certificate belongs. Set a PKI domain name of the CMP server certificate to abc.[Switch-pki-cmp-session-cmp] cmp-request realm abc# Use the MAC for initial certificate application. Set the MAC reference value to 1234 and secret value to 123456.
[Switch-pki-cmp-session-cmp] cmp-request message-authentication-code 1234 123456 [Switch-pki-cmp-session-cmp] quit [Switch] pki cmp initial-request session cmp [Switch] Info: Initializing configuration. Info: Creatting initial request packet. Info: Connectting to CMPv2 server. Info: Sending initial request packet. Info: Waitting for initial response packet. Info: Creatting confirm packet. Info: Connectting to CMPv2 server. Info: Sending confirm packet. Info: Waitting for confirm packet from server. Info: CMPv2 operation finish.
The CA and local certificates are named cmp_ca1.cer and cmp_ir.cer and stored in the device storage.
- Install the certificates.# Import the CA certificate to the PKI realm.
[Switch] pki import-certificate ca realm abc pem filename cmp_ca1.cer The CA's Subject is /C=cn/ST=beijing/L=BB/O=BB/OU=BB/CN=BB The CA's fingerprint is: MD5 fingerprint:3AC7 54FD E272 09BE 9008 84EE D1FC 118E SHA1 fingerprint:492A 8E0B BED2 BE10 C097 9039 99FE F7E1 9AA5 B658 Is the fingerprint correct?(Y/N):y Info: Succeeded in importing file.# Import the local certificate to the PKI realm.[Switch] pki import-certificate local realm abc pem filename cmp_ir.cer Info: Succeeded in importing file. - Configure automatic certificate update.
# Configure the certificate that proves the device itself, which is the certificate to be updated, cmp_ir.cer.
[Switch] pki cmp session cmp [Switch-pki-cmp-session-cmp] cmp-request authentication-cert cmp_ir.cer
# Enable automatic certificate update.
[Switch-pki-cmp-session-cmp] certificate auto-update enable# Configure the device to update the certificate when 60% of the certificate validity period has elapsed.
[Switch-pki-cmp-session-cmp] certificate update expire-time 60 [Switch-pki-cmp-session-cmp] quit
- Verify the configuration.
Configuration Files
Switch configuration file
#
sysname Switch
#
pki entity user01
country CN
state jiangsu
organization huawei
organization-unit info
common-name hello
fqdn user@test.abc.com
ip-address 10.2.0.2
email user@user@test.abc.com
#
pki realm abc
#
pki cmp session cmp
cmp-request ca-name "C=cn,ST=beijing,L=SD,O=BB,OU=BB,CN=BB"
cmp-request authentication-cert cmp_ir.cer
cmp-request entity user01
cmp-request server url http://10.3.0.1:8080
cmp-request rsa local-key-pair rsa_cmp regenerate
cmp-request realm abc
cmp-request message-authentication-code 1234 %^%#ZodFBGH[^BkU2(~>[NRBv|#b>se|@I7"'A,llG_B%^%#
certificate auto-update enable
certificate update expire-time 60
#
ip route-static 10.3.0.0 255.255.255.0 10.2.0.1
#
return