Example for Applying for the Local Certificate in Offline Mode
Networking Requirements
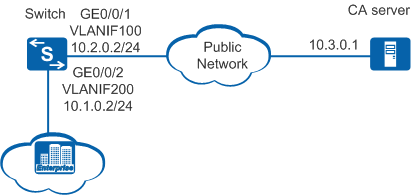
On an enterprise network shown in Figure 1, the Switch is located at the edge to function as the egress gateway and a CA server is located on the public network. The network administrator applies for a local certificate from the CA server.
If you fail to apply for a local certificate using SCEP, you can use the offline (out-of-band) mode.

This example provides only the configurations on Switch. For the configurations on the CA server, see the CA server product manual. In this example, the CA server runs Windows Server 2008 with the built-in Certification Services and with the SCEP plugin installed.
Configuration Roadmap
The configuration roadmap is as follows:
- Create an RSA key pair so that the local certificate application request contains the public key.
- Configure the PKI entity and related information to identify the PKI entity.
- Configure offline local certificate application for the PKI entity and generate a local certificate request file.
- Send the local certificate request file and download the local certificate in out-of-band mode.
- Install the local certificate so that the device can protect communication data.
Procedure
- Assign IP addresses to interfaces and configure static routes to the CA server.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] vlan batch 100 200 [Switch] interface vlanif 100 [Switch-Vlanif100] ip address 10.2.0.2 255.255.255.0 [Switch-Vlanif100] quit [Switch] interface vlanif 200 [Switch-Vlanif200] ip address 10.1.0.2 255.255.255.0 [Switch-Vlanif200] quit [Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] port link-type trunk [Switch-GigabitEthernet0/0/1] port trunk allow-pass vlan 100 [Switch-GigabitEthernet0/0/1] quit [Switch] interface gigabitethernet 0/0/2 [Switch-GigabitEthernet0/0/2] port link-type trunk [Switch-GigabitEthernet0/0/2] port trunk allow-pass vlan 200 [Switch-GigabitEthernet0/0/2] quit [Switch] ip route-static 10.3.0.0 255.255.255.0 10.2.0.1
- Create an RSA key pair.
# Create a 2048-bit RSA key pair named rsa and allow it to be exported.
[Switch] pki rsa local-key-pair create rsakey exportable Info: The name of the new key-pair will be: rsakey The size of the public key ranges from 2048 to 4096. Input the bits in the modules:2048 Generating key-pairs... ..................+++ .......................+++
- Configure a PKI entity to identify a certificate applicant.
# Configure the PKI entity user01.
[Switch] pki entity user01 [Switch-pki-entity-user01] common-name hello [Switch-pki-entity-user01] country cn [Switch-pki-entity-user01] email user@test.abc.com [Switch-pki-entity-user01] fqdn test.abc.com [Switch-pki-entity-user01] ip-address 10.2.0.2 [Switch-pki-entity-user01] state jiangsu [Switch-pki-entity-user01] organization huawei [Switch-pki-entity-user01] organization-unit info [Switch-pki-entity-user01] quit
- Apply for a local certificate in offline mode.
[Switch] pki realm abc [Switch-pki-realm-abc] entity user01 [Switch-pki-realm-abc] rsa local-key-pair rsakey [Switch-pki-realm-abc] quit [Switch] pki enroll-certificate realm abc pkcs10 filename cer_req Info: Creating certificate request file... Info: Create certificate request file successfully.
After the configurations are complete, run the display pki cert-req command to view content of the certificate request file.
[Switch] display pki cert-req filename cer_req Certificate Request: Data: Version: 0 (0x0) Subject: C=CN, ST=jiangsu, O=huawei, OU=info, CN=hello Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:a2:db:e3:30:17:8e:f6:2d:2e:64:15:46:51:ad: 70:86:dd:32:c4:bb:6b:58:3a:8c:5f:a0:06:a1:e1: 56:2e:a4:eb:7e:12:06:05:04:28:b2:6d:64:7a:9c: 4f:85:24:c1:aa:b8:99:dc:e9:bb:c4:1e:e2:9d:a0: 18:51:1f:ad:b5:2f:60:18:06:8b:c1:cc:6f:32:58: f2:21:2c:16:e8:29:c2:a8:c5:aa:9d:6c:1e:ca:14: fc:7a:e9:bc:07:91:ce:ed:a0:c0:52:d9:0c:e9:ba: 9b:64:43:e0:9a:3f:c5:d1:2c:86:36:96:6b:4b:4f: d4:df:05:d0:4b:41:2c:ec:0a:d7:0e:45:83:ed:cd: 07:78:40:ed:d5:3d:7f:fe:0f:08:90:04:2e:ac:e5: 42:b9:81:ea:ec:77:e2:cc:04:6e:e4:63:9f:69:ed: 60:06:5e:c7:e8:bf:30:57:6a:5d:e0:46:68:d3:ee: b0:da:47:24:e3:b6:a5:f3:20:d8:5a:75:92:70:c2: a9:a6:97:07:07:0d:1c:94:9a:03:6f:f7:8c:db:6f: b7:06:de:51:50:9e:71:fd:86:f3:b5:c9:99:05:bf: f1:10:20:28:d3:a6:29:3d:e0:f4:a7:ba:1e:27:85: a9:66:fc:a9:90:49:f0:35:f7:d9:6d:06:a2:43:3f: 18:87 Exponent: 65537 (0x10001) Attributes: Requested Extensions: X509v3 Key Usage: Digital Signature, Non Repudiation, Key Encipherment, Data Encip herment X509v3 Subject Alternative Name: IP Address:10.2.0.2, DNS:test.abc.com, email:user@test.abc.com Signature Algorithm: sha256WithRSAEncryption 0e:0a:a5:b7:d5:54:11:10:c4:ea:ff:77:da:f9:24:4b:a9:98: a1:75:36:08:10:59:60:fa:1a:30:70:2c:b7:f6:5f:5e:31:b7: 55:a5:7a:26:e5:af:4a:cd:83:c5:f3:90:f3:b9:d5:f9:0a:6d: 6e:8f:25:b4:ed:95:9c:75:a5:d7:b6:25:fc:8d:39:89:fb:af: 37:fc:01:7b:09:07:9c:96:7c:fa:28:6d:e2:11:49:a7:95:94: ed:26:5b:ca:f8:98:b0:e7:64:7e:dd:2d:75:ff:89:03:b7:0a: 92:53:25:d4:a1:23:b9:5c:eb:5b:29:1d:8a:92:8f:36:68:7b: 77:32:bc:48:92:48:84:fa:87:5a:d7:2e:3e:be:d5:6b:e4:df: b1:f2:02:35:91:6a:eb:cd:fc:5a:ea:37:85:6c:12:74:5f:a5: 5c:c0:05:09:cd:34:59:0d:c6:c8:75:ca:1c:18:d6:48:e5:4b: e7:8e:e3:ff:25:99:0f:2e:a8:b4:c5:8e:4d:8f:dd:64:c5:1f: 61:3c:58:21:4f:d5:35:ba:c8:8e:5f:76:41:9f:27:41:0a:94: 59:2c:59:25:2d:de:60:5c:92:07:ac:8a:a5:7a:ba:75:af:2c: 82:5f:bb:55:a8:48:49:54:0f:99:54:af:8d:12:4d:4b:7d:8b: 95:28:ce:dc - Transfer the certificate request file to the CA server in out-of-band mode, for example, web, disk, and email, to apply for a local certificate.
When the local certificate is successfully registered, download the local certificate abc_local.cer also in out-of-band mode. Transfer the certificate file to the device storage using a file transfer protocol.
- Install the local certificate.
[Switch] pki import-certificate local realm abc pem filename abc_local.cer Info: Succeeded in importing file.Install the local certificate so that the device can protect communication data.
- Verify the configuration.
Run the display pki certificate local command to view the content of the local certificate imported to memory.
[Switch] display pki certificate local realm abc The x509 object type is certificate: Certificate: Data: Version: 3 (0x2) Serial Number: 48:65:aa:2a:00:00:00:00:3f:c6 Signature Algorithm: sha1WithRSAEncryption Issuer: CN=ca_root Validity Not Before: Dec 21 11:46:10 2015 GMT Not After : Dec 21 11:56:10 2016 GMT Subject: C=CN, ST=jiangsu, O=huawei, OU=info, CN=hello Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:94:6f:49:bd:6a:f3:d5:07:ee:10:ee:4f:d3:06: 80:59:15:cb:a8:0a:b2:ba:c2:db:52:ec:e9:d1:a7: 72:de:ac:35:df:bb:e0:72:62:08:3e:c5:54:c1:ba: 4a:bb:1b:a9:d9:dc:e4:b6:4d:ca:b3:54:90:b6:8e: 15:a3:6e:2d:b2:9e:9e:7a:33:b0:56:3f:ec:bc:67: 1c:4c:59:c6:67:0f:a7:03:52:44:8c:53:72:42:bd: 6e:0c:90:5b:88:9b:2c:95:f7:b8:89:d1:c2:37:3e: 93:78:fa:cb:2c:20:22:5f:e5:9c:61:23:7b:c0:e9: fe:b7:e6:9c:a1:49:0b:99:ef:16:23:e9:44:40:6d: 94:79:20:58:d7:e1:51:a1:a6:4b:67:44:f7:07:71: 54:93:4e:32:ff:98:b4:2b:fa:5d:b2:3c:5b:df:3e: 23:b2:8a:1a:75:7e:8f:82:58:66:be:b3:3c:4a:1c: 2c:64:d0:3f:47:13:d0:5a:29:94:e2:97:dc:f2:d1: 06:c9:7e:54:b3:42:2e:15:b8:40:f3:94:d3:76:a1: 91:66:dd:40:29:c3:69:70:6d:5a:b7:6b:91:87:e8: bb:cb:a5:7e:ec:a5:31:11:f3:04:ab:1a:ef:10:e6: f1:bd:d9:76:42:6c:2e:bf:d9:91:39:1d:08:d7:b4: 18:53 Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Subject Alternative Name: IP Address:10.2.0.2, DNS:test.abc.com, email:user@test.abc.com X509v3 Subject Key Identifier: 15:D1:F6:24:EB:6B:C0:26:19:58:88:91:8B:60:42:CE:BA:D5:4D:F3 X509v3 Authority Key Identifier: keyid:B8:63:72:A4:5E:19:F3:B1:1D:71:E1:37:26:E1:46:39:01:B6:82:C 5 X509v3 CRL Distribution Points: Full Name: URI:file://\\vasp-e6000-127.china.huawei.com\CertEnroll\ca_roo t.crl URI:http://10.3.0.1:8080/certenroll/ca_root.crl Authority Information Access: CA Issuers - URI:http://vasp-e6000-127.china.huawei.com/CertEnro ll/vasp-e6000-127.china.huawei.com_ca_root.crt OCSP - URI:file://\\vasp-e6000-127.china.huawei.com\CertEnroll\v asp-e6000-127.china.huawei.com_ca_root.crt 1.3.6.1.4.1.311.20.2: .0.I.P.S.E.C.I.n.t.e.r.m.e.d.i.a.t.e.O.f.f.l.i.n.e Signature Algorithm: sha1WithRSAEncryption d2:be:a8:52:6b:03:ce:89:f1:5b:49:d4:eb:2b:9f:fd:59:17: d4:3c:f1:db:4f:1b:d1:12:ac:bf:ae:59:b4:13:1b:8a:20:d0: 52:6a:f8:a6:03:a6:72:06:41:d2:a7:7d:3f:51:64:9b:84:64: cf:ec:4c:23:0a:f1:57:41:53:eb:f6:3a:44:92:f3:ec:bd:09: 75:db:02:42:ab:89:fa:c4:cd:cb:09:bf:83:1d:de:d5:4b:68: 8a:a6:5f:7a:e8:b3:34:d3:e8:ec:24:37:2b:bd:3d:09:ed:88: d8:ed:a7:f8:66:aa:6f:b0:fe:44:92:d4:c9:29:21:1c:b3:7a: 65:51:32:50:5a:90:fa:ae:e1:19:5f:c8:63:8d:a8:e7:c6:89: 2e:6d:c8:5b:2c:0c:cd:41:48:bd:79:74:0e:b8:2f:48:69:df: 02:89:bb:b3:59:91:7f:6b:46:29:7e:22:05:8c:bb:6a:7e:f3: 11:5a:5f:fb:65:51:7d:35:ff:49:9e:ec:d1:2d:7e:73:e5:99: c6:41:84:0c:50:11:ed:97:ed:15:de:11:22:73:a1:78:11:2e: 34:e6:f5:de:66:0c:ba:d5:32:af:b8:54:26:4f:5b:9e:89:89: 2a:3f:b8:96:27:00:c3:08:3a:e9:e8:a6:ce:4b:5a:e3:97:9e: 6b:dd:f0:72 Pki realm name: abc Certificate file name: abc_local.cer Certificate peer name: -
Configuration Files
Switch configuration file
#
sysname Switch
#
vlan batch 100 200
#
interface Vlanif100
ip address 10.2.0.2 255.255.255.0
#
interface Vlanif200
ip address 10.1.0.2 255.255.255.0
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 100
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 200
#
ip route-static 10.3.0.0 255.255.255.0 10.2.0.1
#
pki realm abc
entity user01
rsa local-key-pair rsakey
#
pki entity user01
country CN
state jiangsu
organization huawei
organization-unit info
common-name hello
fqdn test.abc.com
ip-address 10.2.0.2
email user@test.abc.com
#
return