Example for Limiting Access Based on the Flow ID
Overview
When the same traffic classification rules need to be configured and the same action needs to be taken for packets that match the traffic classification rules on different interfaces or in different VLANs, to save ACL resources, configure the device to classify packets based on ACL rules, to re-mark the flow ID of each type of packets, and then to classify packets based on the flow ID and to process packets matching the same flow ID in the same manner.
Assume that M ACLs are configured on the device to distinguish services, and each ACL contains N ACL rules. Traffic classifiers classify packets based on ACL rules, and the traffic policy containing the ACL rules are applied to X interfaces. If the action of re-marking flow IDs and matching rules based on the flow IDs are not configured, applying the traffic policy occupies M*N*X ACL resources. If the action of re-marking flow IDs and matching rules based on flow IDs are configured, applying the traffic policy occupies only M*(N+X) ACL resources.
In this example, the device is configured to re-mark flow IDs of packets matching ACL rules, to classify packets based on flow IDs, and to permit or deny packets matching rules to limit the access.
Configuration Notes
For applicable product models and versions, see Applicable Product Models and Versions.

For details about software mappings, visit Hardware Query Tool and search for the desired product model.
Networking Requirements
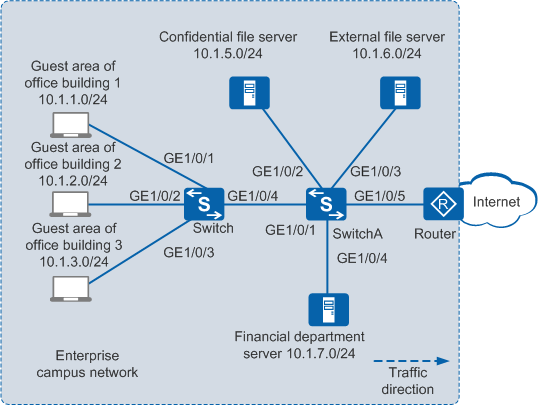
In Figure 1, the Switch connects to SwitchA, and SwitchA connect to the router. Guests can connect to the enterprise network in guest areas of office buildings 1, 2, and 3. Guests can access the public file server and the Internet, but cannot access the confidential file server and financial department server.
Device |
Interface |
VLAN |
Layer 3 Interface |
IP Address |
|---|---|---|---|---|
Switch |
GigabitEthernet1/0/1 |
VLAN 10 |
VLANIF 10 |
10.1.1.1/24 |
GigabitEthernet1/0/2 |
VLAN 20 |
VLANIF 20 |
10.1.2.1/24 |
|
GigabitEthernet1/0/3 |
VLAN 30 |
VLANIF 30 |
10.1.3.1/24 |
|
GigabitEthernet1/0/4 |
VLAN 40 |
VLANIF 40 |
10.1.4.1/24 |
|
SwitchA |
GigabitEthernet1/0/1 |
VLAN 40 |
VLANIF 40 |
10.1.4.2/24 |
GigabitEthernet1/0/2 |
VLAN 50 |
VLANIF 50 |
10.1.5.1/24 |
|
GigabitEthernet1/0/3 |
VLAN 60 |
VLANIF 60 |
10.1.6.1/24 |
|
GigabitEthernet1/0/4 |
VLAN 70 |
VLANIF 70 |
10.1.7.1/24 |
|
GigabitEthernet1/0/5 |
VLAN 80 |
VLANIF 80 |
10.1.8.1/24 |
Configuration Roadmap
- Create VLANs, and configure interfaces and a routing protocol so that the enterprise can access the Internet.
- Configure ACLs on the Switch to match packets from guest areas.
- Configure traffic classifiers on the Switch to classify packets based on ACLs.
- Configure traffic behaviors on the Switch to re-mark flow IDs of packets matching ACLs.
- Configure a traffic policy that contains flow ID re-marking on the Switch, bind the traffic behaviors and traffic classifiers to the traffic policy, and apply the traffic policy to the Switch globally in the inbound direction.
- Configure traffic classifiers on the Switch to classify packets from guest areas based on flow IDs.
- Configure traffic behaviors on the Switch to permit or reject packets from guest areas to implement access control.
- Configure a traffic policy for access control on the Switch, bind the traffic behaviors and traffic classifiers to the traffic policy, and apply the traffic policy to the interfaces on the Switch connected to guest areas in the inbound direction.
Procedure
- Create VLANs, and configure interfaces and a routing protocol (the static route is used here).
# Configure the Switch.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] vlan batch 10 20 30 40 //Create VLAN 10 to VLAN 40. [Switch] interface gigabitethernet 1/0/1 [Switch-GigabitEthernet1/0/1] port link-type access //Configure the interface as an access interface. [Switch-GigabitEthernet1/0/1] port default vlan 10 [Switch-GigabitEthernet1/0/1] quit [Switch] interface gigabitethernet 1/0/2 [Switch-GigabitEthernet1/0/2] port link-type access [Switch-GigabitEthernet1/0/2] port default vlan 20 [Switch-GigabitEthernet1/0/2] quit [Switch] interface gigabitethernet 1/0/3 [Switch-GigabitEthernet1/0/3] port link-type access [Switch-GigabitEthernet1/0/3] port default vlan 30 [Switch-GigabitEthernet1/0/3] quit [Switch] interface gigabitethernet 1/0/4 [Switch-GigabitEthernet1/0/4] port link-type trunk //Configure the interface as a trunk interface. [Switch-GigabitEthernet1/0/4] port trunk allow-pass vlan 10 20 30 40 [Switch-GigabitEthernet1/0/4] quit [Switch] interface vlanif 10 //Create a VLANIF interface. [Switch-Vlanif10] ip address 10.1.1.1 255.255.255.0 //Configure an IP address for the VLANIF interface. [Switch-Vlanif10] quit [Switch] interface vlanif 20 [Switch-Vlanif20] ip address 10.1.2.1 255.255.255.0 [Switch-Vlanif20] quit [Switch] interface vlanif 30 [Switch-Vlanif30] ip address 10.1.3.1 255.255.255.0 [Switch-Vlanif30] quit [Switch] interface vlanif 40 [Switch-Vlanif40] ip address 10.1.4.1 255.255.255.0 [Switch-Vlanif40] quit [Switch] ip route-static 10.1.5.0 255.255.255.0 10.1.4.2 //Configure a static route. [Switch] ip route-static 10.1.6.0 255.255.255.0 10.1.4.2 [Switch] ip route-static 10.1.7.0 255.255.255.0 10.1.4.2 [Switch] ip route-static 10.1.8.0 255.255.255.0 10.1.4.2
# Configure SwitchA.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] vlan batch 40 50 60 70 80 //Create VLAN 40 to VLAN 80. [SwitchA] interface gigabitethernet 1/0/1 [SwitchA-GigabitEthernet1/0/1] port link-type trunk //Configure the interface as a trunk interface. [SwitchA-GigabitEthernet1/0/1] port trunk allow-pass vlan 40 50 60 70 80 [SwitchA-GigabitEthernet1/0/1] quit [SwitchA] interface gigabitethernet 1/0/2 [SwitchA-GigabitEthernet1/0/2] port link-type access //Configure the interface as an access interface. [SwitchA-GigabitEthernet1/0/2] port default vlan 50 [SwitchA-GigabitEthernet1/0/2] quit [SwitchA] interface gigabitethernet 1/0/3 [SwitchA-GigabitEthernet1/0/3] port link-type access [SwitchA-GigabitEthernet1/0/3] port default vlan 60 [SwitchA-GigabitEthernet1/0/3] quit [SwitchA] interface gigabitethernet 1/0/4 [SwitchA-GigabitEthernet1/0/4] port link-type access [SwitchA-GigabitEthernet1/0/4] port default vlan 70 [SwitchA-GigabitEthernet1/0/4] quit [SwitchA] interface gigabitethernet 1/0/5 [SwitchA-GigabitEthernet1/0/5] port link-type access [SwitchA-GigabitEthernet1/0/5] port default vlan 80 [SwitchA-GigabitEthernet1/0/5] quit [SwitchA] interface vlanif 40 //Create a VLANIF interface. [SwitchA-Vlanif40] ip address 10.1.4.2 255.255.255.0 //Configure an IP address for the VLANIF interface. [SwitchA-Vlanif40] quit [SwitchA] interface vlanif 50 [SwitchA-Vlanif50] ip address 10.1.5.1 255.255.255.0 [SwitchA-Vlanif50] quit [SwitchA] interface vlanif 60 [SwitchA-Vlanif60] ip address 10.1.6.1 255.255.255.0 [SwitchA-Vlanif60] quit [SwitchA] interface vlanif 70 [SwitchA-Vlanif70] ip address 10.1.7.1 255.255.255.0 [SwitchA-Vlanif70] quit [SwitchA] interface vlanif 80 [SwitchA-Vlanif80] ip address 10.1.8.1 255.255.255.0 [SwitchA-Vlanif80] quit [SwitchA] ip route-static 10.1.1.0 255.255.255.0 10.1.4.1 //Configure a static route. [SwitchA] ip route-static 10.1.2.0 255.255.255.0 10.1.4.1 [SwitchA] ip route-static 10.1.3.0 255.255.255.0 10.1.4.1
- Configure ACLs.# Configure an ACL rule to match packets sent from the guest area to the confidential file server.
[Switch] acl name non-access-file [Switch-acl-adv-non-access-file] rule permit tcp destination 10.1.5.0 0.0.0.255 destination-port eq 20 //Configure a rule to permit FTP data packets sent from the guest area to the confidential file server. [Switch-acl-adv-non-access-file] rule permit tcp destination 10.1.5.0 0.0.0.255 destination-port eq 21 //Configure a rule to permit FTP protocol packets sent from the guest area to the confidential file server. [Switch-acl-adv-non-access-file] quit
# Configure an ACL rule to match packets sent from the guest area to the financial department server.[Switch] acl name non-access-finance [Switch-acl-adv-non-access-finance] rule permit tcp destination 10.1.7.0 0.0.0.255 destination-port eq 20 //Configure a rule to permit FTP data packets sent from the guest area to the financial department server. [Switch-acl-adv-non-access-finance] rule permit tcp destination 10.1.7.0 0.0.0.255 destination-port eq 21 //Configure a rule to permit FTP protocol packets sent from the guest area to the financial department server. [Switch-acl-adv-non-access-finance] quit
# Configure an ACL rule to match packets sent from the guest area to the public file server.[Switch] acl name access-file [Switch-acl-adv-access-file] rule permit tcp destination 10.1.6.0 0.0.0.255 destination-port eq 20 //Configure a rule to permit FTP data packets sent from the guest area to the public file server. [Switch-acl-adv-access-file] rule permit tcp destination 10.1.6.0 0.0.0.255 destination-port eq 21 //Configure a rule to permit FTP protocol packets sent from the guest area to the public file server. [Switch-acl-adv-access-file] quit
# Configure an ACL rule to match packets sent from the guest area to the external network.[Switch] acl name access-internet [Switch-acl-adv-access-internet] rule permit tcp destination-port eq 80 [Switch-acl-adv-access-internet] quit
- Configure traffic classifiers.
# Configure traffic classifiers on the Switch to classify packets from guest areas based on ACLs.
[Switch] traffic classifier non-access-file operator and [Switch-classifier-non-access-file] if-match acl non-access-file //Configure the device to match packets sent from the guest area to the confidential file server. [Switch-classifier-non-access-file] quit [Switch] traffic classifier non-access-finance operator and [Switch-classifier-non-access-finance] if-match acl non-access-finance //Configure the device to match packets sent from the guest area to the financial department server. [Switch-classifier-non-access-finance] quit [Switch] traffic classifier access-file operator and [Switch-classifier-access-file] if-match acl access-file //Configure the device to match packets sent from the guest area to the public file server. [Switch-classifier-access-file] quit [Switch] traffic classifier access-internet operator and [Switch-classifier-access-internet] if-match acl access-internet //Configure the device to match packets sent from the guest area to the external network. [Switch-classifier-access-internet] quit
- Configure traffic behaviors.
# Create traffic behaviors on the Switch to re-mark flow IDs of packets.
[Switch] traffic behavior non-access-file [Switch-behavior-non-access-file] remark flow-id 1 //Configure the device to re-mark the flow ID of packets sent from the guest area to the confidential file server with 1. [Switch-behavior-non-access-file] quit [Switch] traffic behavior non-access-finance [Switch-behavior-non-access-finance] remark flow-id 2 //Configure the device to re-mark the flow ID of packets sent from the guest area to the financial department server with 2. [Switch-behavior-non-access-finance] quit [Switch] traffic behavior access-file [Switch-behavior-access-file] remark flow-id 3 //Configure the device to re-mark the flow ID of packets sent from the guest area to the public file server with 3. [Switch-behavior-access-file] quit [Switch] traffic behavior access-internet [Switch-behavior-access-internet] remark flow-id 4 //Configure the device to re-mark the flow ID of packets sent from the guest area to the external network with 4. [Switch-behavior-access-internet] quit
- Configure a traffic policy that contains flow ID re-marking and apply the traffic policy globally in the inbound direction.
# Create the traffic policy flow-id on the Switch, bind the traffic classifiers and traffic behaviors to the traffic policy, and apply the traffic policy globally in the inbound direction.
[Switch] traffic policy flow-id [Switch-trafficpolicy-flow-id] classifier non-access-file behavior non-access-file [Switch-trafficpolicy-flow-id] classifier non-access-finance behavior non-access-finance [Switch-trafficpolicy-flow-id] classifier access-file behavior access-file [Switch-trafficpolicy-flow-id] classifier access-internet behavior access-internet [Switch-trafficpolicy-flow-id] quit [Switch] traffic-policy flow-id global inbound
- Configure traffic classifiers.
# Configure traffic classifiers on the Switch to classify packets from guest areas based on flow IDs.
[Switch] traffic classifier flow-id1 operator and [Switch-classifier-flow-id1] if-match flow-id 1 //Configure the device to match packets with the flow ID of 1, that is, packets sent from the guest area to the confidential file server. [Switch-classifier-flow-id1] quit [Switch] traffic classifier flow-id2 operator and [Switch-classifier-flow-id2] if-match flow-id 2 //Configure the device to match packets with the flow ID of 2, that is, packets sent from the guest area to the financial department server. [Switch-classifier-flow-id2] quit [Switch] traffic classifier flow-id3 operator and [Switch-classifier-flow-id3] if-match flow-id 3 //Configure the device to match packets with the flow ID of 3, that is, packets sent from the guest area to the public file server. [Switch-classifier-flow-id3] quit [Switch] traffic classifier flow-id4 operator and [Switch-classifier-flow-id4] if-match flow-id 4 //Configure the device to match packets with the flow ID of 4, that is, packets sent from the guest area to the external network. [Switch-classifier-flow-id4] quit
- Configure traffic behaviors.
# Create traffic behaviors on the Switch to permit or reject matching packets.
[Switch] traffic behavior flow-id1 [Switch-behavior-flow-id1] deny //Configure the device to reject packets with the flow ID of 1. [Switch-behavior-flow-id1] quit [Switch] traffic behavior flow-id2 [Switch-behavior-flow-id2] deny //Configure the device to reject packets with the flow ID of 2. [Switch-behavior-flow-id2] quit [Switch] traffic behavior flow-id3 [Switch-behavior-flow-id3] permit //Configure the device to permit packets with the flow ID of 3 to pass through. [Switch-behavior-flow-id3] quit [Switch] traffic behavior flow-id4 [Switch-behavior-flow-id4] permit //Configure the device to permit packets with the flow ID of 4 to pass through. [Switch-behavior-flow-id4] quit
- Configure a traffic policy for access control and apply the traffic policy to an interface.
# Create the traffic policy access_policy on the Switch, bind the traffic behaviors and traffic classifiers to the traffic policy, and apply the traffic policy to GE1/0/1, GE1/0/2, and GE1/0/3 in the inbound direction to limit access of guest areas.
[Switch] traffic policy access_policy [Switch-trafficpolicy-access_policy] classifier flow-id1 behavior flow-id1 [Switch-trafficpolicy-access_policy] classifier flow-id2 behavior flow-id2 [Switch-trafficpolicy-access_policy] classifier flow-id3 behavior flow-id3 [Switch-trafficpolicy-access_policy] classifier flow-id4 behavior flow-id4 [Switch-trafficpolicy-access_policy] quit [Switch] interface gigabitethernet 1/0/1 [Switch-GigabitEthernet1/0/1] traffic-policy access_policy inbound [Switch-GigabitEthernet1/0/1] quit [Switch] interface gigabitethernet 1/0/2 [Switch-GigabitEthernet1/0/2] traffic-policy access_policy inbound [Switch-GigabitEthernet1/0/2] quit [Switch] interface gigabitethernet 1/0/3 [Switch-GigabitEthernet1/0/3] traffic-policy access_policy inbound [Switch-GigabitEthernet1/0/3] quit
- Verify the configuration.
# Check the ACL configuration.
[Switch] display acl all Total nonempty ACL number is 4 Advanced ACL access-internet 3996, 1 rule Acl's step is 5 rule 5 permit tcp destination-port eq www (match-counter 0) Advanced ACL access-file 3997, 2 rules Acl's step is 5 rule 5 permit tcp destination 10.1.6.0 0.0.0.255 destination-port eq ftp-data (match-counter 0) rule 10 permit tcp destination 10.1.6.0 0.0.0.255 destination-port eq ftp (match-counter 0) Advanced ACL non-access-finance 3998, 2 rules Acl's step is 5 rule 5 permit tcp destination 10.1.7.0 0.0.0.255 destination-port eq ftp-data (match-counter 0) rule 10 permit tcp destination 10.1.7.0 0.0.0.255 destination-port eq ftp (match-counter 0) Advanced ACL non-access-file 3999, 2 rules Acl's step is 5 rule 5 permit tcp destination 10.1.5.0 0.0.0.255 destination-port eq ftp-data (match-counter 0) rule 10 permit tcp destination 10.1.5.0 0.0.0.255 destination-port eq ftp (match-counter 0)# Check the traffic classifier configuration.
[Switch] display traffic classifier user-defined User Defined Classifier Information: Classifier: flow-id1 Precedence: 25 Operator: AND Rule(s) : if-match flow-id 1 Classifier: flow-id2 Precedence: 30 Operator: AND Rule(s) : if-match flow-id 2 Classifier: flow-id3 Precedence: 35 Operator: AND Rule(s) : if-match flow-id 3 Classifier: flow-id4 Precedence: 40 Operator: AND Rule(s) : if-match flow-id 4 Classifier: non-access-file Precedence: 5 Operator: AND Rule(s) : if-match acl non-access-file Classifier: non-access-finance Precedence: 10 Operator: AND Rule(s) : if-match acl non-access-finance Classifier: access-file Precedence: 15 Operator: AND Rule(s) : if-match acl access-file Classifier: access-internet Precedence: 20 Operator: AND Rule(s) : if-match acl access-internet Total classifier number is 8# Check the traffic policy configuration.
[Switch] display traffic policy user-defined User Defined Traffic Policy Information: Policy: flow-id Classifier: non-access-file Operator: AND Behavior: non-access-file Permit Remark: Remark flow-id 1 Classifier: non-access-finance Operator: AND Behavior: non-access-finance Permit Remark: Remark flow-id 2 Classifier: access-file Operator: AND Behavior: access-file Permit Remark: Remark flow-id 3 Classifier: access-internet Operator: AND Behavior: access-internet Permit Remark: Remark flow-id 4 Policy: access_policy Classifier: flow-id1 Operator: AND Behavior: flow-id1 Deny Classifier: flow-id2 Operator: AND Behavior: flow-id2 Deny Classifier: flow-id3 Operator: AND Behavior: flow-id3 Permit Classifier: flow-id4 Operator: AND Behavior: flow-id4 Permit Total policy number is 2
Configuration Files
Switch configuration file
# sysname Switch # vlan batch 10 20 30 40 # acl name access-internet 3996 rule 5 permit tcp destination-port eq www acl name access-file 3997 rule 5 permit tcp destination 10.1.6.0 0.0.0.255 destination-port eq ftp-data rule 10 permit tcp destination 10.1.6.0 0.0.0.255 destination-port eq ftp acl name non-access-finance 3998 rule 5 permit tcp destination 10.1.7.0 0.0.0.255 destination-port eq ftp-data rule 10 permit tcp destination 10.1.7.0 0.0.0.255 destination-port eq ftp acl name non-access-file 3999 rule 5 permit tcp destination 10.1.5.0 0.0.0.255 destination-port eq ftp-data rule 10 permit tcp destination 10.1.5.0 0.0.0.255 destination-port eq ftp # traffic classifier access-file operator and precedence 15 if-match acl access-file traffic classifier access-internet operator and precedence 20 if-match acl access-internet traffic classifier flow-id1 operator and precedence 25 if-match flow-id 1 traffic classifier flow-id2 operator and precedence 30 if-match flow-id 2 traffic classifier flow-id3 operator and precedence 35 if-match flow-id 3 traffic classifier flow-id4 operator and precedence 40 if-match flow-id 4 traffic classifier non-access-file operator and precedence 5 if-match acl non-access-file traffic classifier non-access-finance operator and precedence 10 if-match acl non-access-finance # traffic behavior access-file permit remark flow-id 3 traffic behavior access-internet permit remark flow-id 4 traffic behavior flow-id1 deny traffic behavior flow-id2 deny traffic behavior flow-id3 permit traffic behavior flow-id4 permit traffic behavior non-access-file permit remark flow-id 1 traffic behavior non-access-finance permit remark flow-id 2 # traffic policy access_policy match-order config classifier flow-id1 behavior flow-id1 classifier flow-id2 behavior flow-id2 classifier flow-id3 behavior flow-id3 classifier flow-id4 behavior flow-id4 traffic policy flow-id match-order config classifier non-access-file behavior non-access-file classifier non-access-finance behavior non-access-finance classifier access-file behavior access-file classifier access-internet behavior access-internet # interface Vlanif10 ip address 10.1.1.1 255.255.255.0 # interface Vlanif20 ip address 10.1.2.1 255.255.255.0 # interface Vlanif30 ip address 10.1.3.1 255.255.255.0 # interface Vlanif40 ip address 10.1.4.1 255.255.255.0 # interface GigabitEthernet1/0/1 port link-type access port default vlan 10 traffic-policy access_policy inbound # interface GigabitEthernet1/0/2 port link-type access port default vlan 20 traffic-policy access_policy inbound # interface GigabitEthernet1/0/3 port link-type access port default vlan 30 traffic-policy access_policy inbound # interface GigabitEthernet1/0/4 port link-type trunk port trunk allow-pass vlan 10 20 30 40 # ip route-static 10.1.5.0 255.255.255.0 10.1.4.2 ip route-static 10.1.6.0 255.255.255.0 10.1.4.2 ip route-static 10.1.7.0 255.255.255.0 10.1.4.2 ip route-static 10.1.8.0 255.255.255.0 10.1.4.2 # traffic-policy flow-id global inbound # returnSwitchA configuration file
# sysname SwitchA # vlan batch 40 50 60 70 80 # interface Vlanif40 ip address 10.1.4.2 255.255.255.0 # interface Vlanif50 ip address 10.1.5.1 255.255.255.0 # interface Vlanif60 ip address 10.1.6.1 255.255.255.0 # interface Vlanif70 ip address 10.1.7.1 255.255.255.0 # interface Vlanif80 ip address 10.1.8.1 255.255.255.0 # interface GigabitEthernet1/0/1 port link-type trunk port trunk allow-pass vlan 40 50 60 70 80 # interface GigabitEthernet1/0/2 port link-type access port default vlan 50 # interface GigabitEthernet1/0/3 port link-type access port default vlan 60 # interface GigabitEthernet1/0/4 port link-type access port default vlan 70 # interface GigabitEthernet1/0/5 port link-type access port default vlan 80 # ip route-static 10.1.1.0 255.255.255.0 10.1.4.1 ip route-static 10.1.2.0 255.255.255.0 10.1.4.1 ip route-static 10.1.3.0 255.255.255.0 10.1.4.1 # return
Applicable Product Models and Versions
Product |
Product Model |
Software Version |
|---|---|---|
S5700 |
S5720-EI |
V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
S5720-HI |
V200R019C00, V200R019C10 |
|
S5730-HI |
V200R019C00, V200R019C10 |
|
S5731-H |
V200R019C00, V200R019C10 |
|
S5731-S |
V200R019C00, V200R019C10 |
|
S5731S-S |
V200R019C00, V200R019C10 |
|
S5731S-H |
V200R019C00, V200R019C10 |
|
S5732-H |
V200R019C00, V200R019C10 |
|
S5735-L, S5735S-L |
V200R019C00, V200R019C10 |
|
S5735S-L-M |
V200R019C00, V200R019C10 |
|
S5735-S, S5735S-S |
V200R019C00, V200R019C10 |
|
S5700 |
S5735-S-I |
V200R019C10 |
S6700 |
S6720-EI |
V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
S6720S-EI |
V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-HI |
V200R019C00, V200R019C10 |
|
S6730-H |
V200R019C00, V200R019C10 |
|
S6730-S |
V200R019C00, V200R019C10 |
|
S6730S-S |
V200R019C00, V200R019C10 |
|
S6730S-H |
V200R019C10 |
|
S7700 |
S7703, S7706, S7712 |
V200R008C00, V200R009C00, V200R010C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
S7703 PoE |
V200R013C00, V200R019C00, V200R019C10 |
|
S7706 PoE |
V200R013C00, V200R019C00, V200R019C10 |
|
S9700 |
S9703, S9706, S9712 |
V200R008C00, V200R009C00, V200R010C00, V200R011C10, V200R012C00, V200R013C00 |