Overview of Security
Threats to Network Security
Existing or potential security events may threaten the confidentiality, integrity, or availability of resources in a network system. Network security protection services can mitigate network security threats to a certain extent and within a specified scope.
- Confidentiality: Data stored, processed, and transmitted by a switch must not be leaked to unauthorized users, entities, or processes. That is, data must be used only by authorized users.
- Integrity: Data cannot be modified without permission. That is, network information must not be deleted, modified, forged, unsequenced, or inserted during storage and transmission.
- Availability: As long as required external resources are available, functions of a switch can be executed under specified conditions and at a specified time or time period. Services must be always available and meet carrier-class quality of service (QoS) requirements.
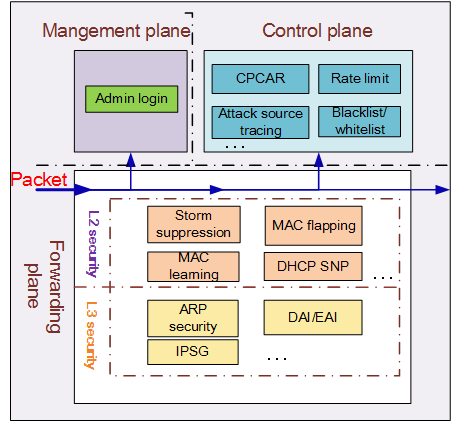
Management Plane
The key to security of the management plane is ensuring that devices can be managed by authorized users. Network security services specify which users can log in to a switch and what operations the users can perform. As shown in Figure 1, to ensure security of the management plane of a switch, you can configure the switch to allow only administrators to log in to it. Administrators can then log in to and manage the switch securely. You can configure user names and passwords for each user who you want to log in to the switch, and configure ACLs to restrict login of users. You can use STelnet to ensure that administrators can log in securely, and configure the user level to control user operation rights. For details about the implementation and configuration of user login, see CLI Login Configuration and Web System Login in the S2720, S5700, and S6700 V200R019C10 Configuration Guide-Basic Configuration Guide.
Control Plane
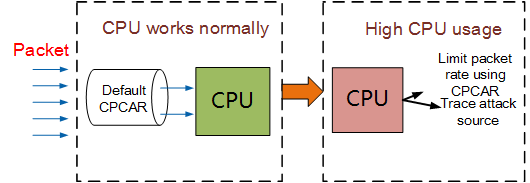
The control plane controls data forwarding based on the CPU. The CPU is the brain of a switch, controlling operations of switch components. Therefore, security of the CPU must be guaranteed for devices and protocols to run properly. If too many protocol packets are sent to the CPU, the CPU will become overloaded, degrading the switch performance and causing service interruptions. As the core component of a switch, the CPU is a common target of attacks from unauthorized users. Switches support two main types of security protection services on the control plane: local attack defense and attack defense.
- Adjust the CPCAR value: Decrease the CPCAR value to reduce the number of protocol packets sent to the CPU.
- Trace attack sources: Analyze the packets sent to the CPU, and set the threshold for the number of packets sent to the CPU. Take measures to handle packets exceeding the threshold, for example, dropping the packets, shutting down interfaces, and configuring a blacklist.
Forwarding Plane
- Exhausting forwarding entries: prevents forwarding entries of authorized users from being learnt and their traffic forwarded.
- Tampering with forwarding entries: causes traffic of authorized users to be forwarded to an incorrect destination.
- Layer 2 network: Layer 2 data is forwarded based on the MAC address table. That is, a switch needs to search for MAC address entries to forward data traffic. Therefore, the MAC address table is prone to attacks. An attack may be in the form of unauthorized users sending a large number of packets, which are then recorded as MAC address entries. Also, when no MAC entry is found for a packet, the packet is broadcast, consuming bandwidth and potentially causing broadcast storms. To guarantee security of MAC address tables, switches MAC address learning, port security, DHCP Snooping, and storm suppression.
- Layer 3 network: Layer 3 data is forwarded based on the ARP table and routing table. The entries in the routing table are generated through routing protocol negotiation, so they are difficult to attack. The ARP entries are generated by protocol packet exchange. Attackers may send a large number of protocol packets or forged protocol packets to attack the ARP table. Therefore, the ARP table must be properly protected in Layer 3 forwarding. To prevent such attacks, switches support ARP security, DAI, EAI, and IPSG.