Configuring Egress ARP Inspection
Pre-configuration Task
Before configuring Egress ARP Inspection (EAI):
- Configure DHCP snooping. For details, see DHCP Snooping Configuration in the S2720, S5700, and S6700 V200R019C10 Configuration Guide - Security.
Context
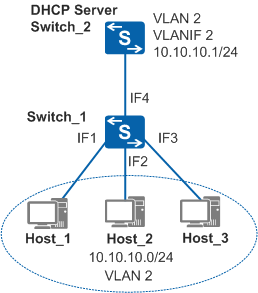
Figure 1 shows an example of a network using egress ARP inspection.
In Figure 1, if all or most users connected to Switch_1 obtain IP addresses through DHCP and belong to the same VLAN, EAI can be enabled to prevent broadcast of ARP packets. EAI allows the device to look up the DHCP snooping table for the outbound interface matching the destination IP address. The device then sends the ARP Request packets directly from the outbound interface. This avoids needless broadcast of ARP Request packets, reduces the impact on the network, ensures normal service running, and prevents ARP attacks.
For example, if Switch_1 detects that the outbound interface IF3 is isolated from the inbound interface IF1, it discards the ARP Request packet sent from Host_1. As a result, Host_1 and Host_3 cannot communicate. To solve this problem, Switch_1 is enabled to forward ARP packets to a trusted interface when the inbound and outbound interfaces are isolated, and intra-VLAN proxy ARP is configured on Switch_2. When detecting that the outbound interface IF3 is isolated from the inbound interface IF1, Switch_1 directly forwards the received ARP Request packet to the trusted interface IF4 (in DHCP snooping, the interface connected to a DHCP server is configured as a trusted interface). As Switch_2 is configured with intra-VLAN proxy ARP, it sends an ARP Reply packet after receiving the ARP Request packet. Host_1 and Host_3 can now communicate with each other.
Procedure
- Run system-view
The system view is displayed.
- Run vlan vlan-id
The VLAN view is displayed.
- Run dhcp snooping arp security enable
EAI is enabled.
By default, EAI is disabled.

After EAI is enabled, the device sends all the received ARP packets to the CPU for software forwarding, which degrades the ARP packet forwarding performance.
EAI and MAC-forced forwarding (MFF) cannot be configured in the same VLAN because the two functions use mutually exclusive ARP mechanisms. MFF uses the proxy ARP mechanism, whereas EAI forwards ARP Request packets. For the MFF implementation, see MFF Configuration in the S2720, S5700, and S6700 V200R019C10 Configuration Guide - Security.
EAI enabled in a super VLAN does not take effect.
- If a VLANIF interface is created for a VLAN enabled with EAI, EAI does not take effect on the VLAN.
- (Optional) Run dhcp snooping arp security isolate-forwarding-trust
The device is enabled to forward ARP packets to trusted interfaces when port isolation is enabled on the inbound and outbound interfaces.
By default, the device is disabled from forwarding packets to trusted interfaces when port isolation is enabled on the inbound and outbound interfaces.

On the device enabled with EAI, if port isolation is configured on the interfaces connecting to users, you must perform this step and configure intra-VLAN proxy ARP on the uplink device. For example, if port isolation is configured on the interfaces connecting Switch_1 to users in Figure 1, perform Step 4 on Switch_1 and configure intra-VLAN proxy ARP on Switch_2. For the configuration of intra-VLAN proxy ARP, see Configuring Intra-VLAN Proxy ARP.