Example for Configuring ARP Security Functions
ARP Security Overview
Address Resolution Protocol (ARP) security protects network devices against ARP attacks by learning ARP entries, limiting ARP packet rate, and checking ARP packets. In addition to preventing ARP protocol attacks, ARP security also prevents ARP-based network scanning attacks.
When user hosts directly connect to the gateway, the attacker forges an ARP packet of the gateway and sends the ARP packet to user hosts. The user hosts then consider that the attacker is the gateway, and record incorrect gateway address mappings into their ARP tables. The traffic destined for the gateway is then received by the attacker. In this way, the attacker intercepts the data sent by user hosts.
A user host sends a large number of IP packets with unresolvable destination IP addresses (the routing table contains the routing entries matching the destination IP addresses of the packets but the device does not have the ARP entries matching the next hop addresses of the routing entries) to the device, causing the device to generate a large number of ARP Miss packets. The IP packets (ARP Miss packets) triggering ARP Miss messages are sent to the CPU for processing. The device generates and delivers many temporary ARP entries according to the ARP Miss messages, and sends a large number of ARP request packets to the destination network. This increases CPU usage of the device and consumes much network bandwidth.
The device receives a large number of ARP attack packets and needs to process all of them. As a result, the device's CPU may be overloaded.
To prevent the first attack (the attacker poses as the gateway to intercept host information), configure ARP gateway anti-collision.
To prevent the second attack, configure ARP Miss rate limiting to reduce CPU load and save bandwidth on destination network.
To prevent the third attack, configure ARP packet rate limiting to protect CPU resources.
Configuration Notes
- This example applies to all modular switch models and versions.
- For the fixed switch models and versions that support this example, see Applicable Products and Versions.
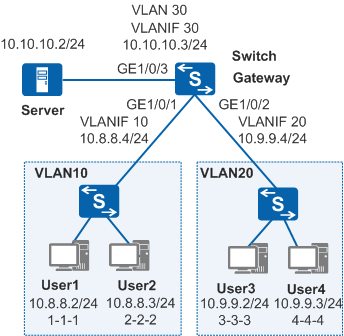
Networking Requirements
- The attacker poses as the gateway to send an ARP packet to the switch, so user hosts consider that the attacker is the gateway. As a result, traffic destined for the gateway from user hosts is received by the attacker, and the attacker intercepts data from user hosts.
- Attackers send a large number of IP packets with unresolvable destination IP addresses to the switch, leading to CPU overload.
- User1 sends a large number of ARP packets with fixed MAC addresses but variable source IP addresses to the switch. As a result, the available CPU of the switch is insufficient to process other services.
- User3 sends a large number of ARP packets with fixed source IP addresses to the switch. As a result, the available CPU of the switch is insufficient to process other services.
Configuration Roadmap
- Configure ARP gateway anti-collision to prevent attackers from posing as the gateway to intercept data.
- Configure ARP Miss rate limiting based on source IP addresses to prevent user-side attackers from sending a large number of unresolvable IP packets, triggering ARP Miss messages and forming ARP flood attacks. In addition, ensure that the switch can process ARP packets from servers because network communication will be unavailable if such packets are discarded.
- Configure ARP rate limiting based on source MAC addresses to prevent User1 from sending a large number of ARP packets with different source IP addresses and a fixed MAC address to form ARP flood attacks. The ARP flood attacks will overload the switch's CPU.
- Configure rate limiting on ARP packets based on the source IP address. This function defends against ARP flood attacks from User3 with a fixed IP address and prevents CPU overload.
Procedure
- Create VLANs, add interfaces to the VLANs, and configure VLANIF interfaces.
# Create VLAN 10, VLAN 20, VLAN 30, and add GE1/0/1 to VLAN 10, GE1/0/2 to VLAN 20, and GE1/0/3 to VLAN 30.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] vlan batch 10 20 30 [Switch] interface gigabitethernet 1/0/1 [Switch-GigabitEthernet1/0/1] port link-type trunk [Switch-GigabitEthernet1/0/1] port trunk allow-pass vlan 10 [Switch-GigabitEthernet1/0/1] quit [Switch] interface gigabitethernet 1/0/2 [Switch-GigabitEthernet1/0/2] port link-type trunk [Switch-GigabitEthernet1/0/2] port trunk allow-pass vlan 20 [Switch-GigabitEthernet1/0/2] quit [Switch] interface gigabitethernet 1/0/3 [Switch-GigabitEthernet1/0/3] port link-type trunk [Switch-GigabitEthernet1/0/3] port trunk allow-pass vlan 30 [Switch-GigabitEthernet1/0/3] quit
# Create VLANIF 10, VLANIF 20, and VLANIF 30, and assign IP addresses to them.
[Switch] interface vlanif 10 [Switch-Vlanif10] ip address 10.8.8.4 24 [Switch-Vlanif10] quit [Switch] interface vlanif 20 [Switch-Vlanif20] ip address 10.9.9.4 24 [Switch-Vlanif20] quit [Switch] interface vlanif 30 [Switch-Vlanif30] ip address 10.10.10.3 24 [Switch-Vlanif30] quit
- Configure ARP gateway anti-collision.
[Switch] arp anti-attack gateway-duplicate enable //Configure ARP gateway anti-collision
- Configure rate limiting on ARP Miss messages based on the source IP address.
# Set the maximum rate of ARP Miss messages triggered by the server with the IP address 10.10.10.2 to 40 pps, and set the maximum rate of ARP Miss messages triggered by other hosts to 20 pps.
[Switch] arp-miss speed-limit source-ip maximum 20 //Configure rate limiting on ARP Miss messages based on the source IP address [Switch] arp-miss speed-limit source-ip 10.10.10.2 maximum 40 //Configure rate limiting on ARP Miss messages based on the source IP address
- Configure rate limiting on ARP packets based on the source MAC address.
# Set the maximum rate of ARP packets from User1 with the source MAC address 0001-0001-0001 to 10 pps.
[Switch] arp speed-limit source-mac 0001-0001-0001 maximum 10 //Configure rate limiting on ARP packets based on the source MAC address
- Configure rate limiting on ARP packets based on the source IP address.
# Set the maximum rate of ARP packets from User3 with the source IP address 10.9.9.2 to 10 pps.
[Switch] arp speed-limit source-ip 10.9.9.2 maximum 10 //Configure rate limiting on ARP packets based on the source IP address
- Verify the configuration.
# Run the display arp anti-attack configuration all command to check the configuration of ARP anti-attack.
[Switch] display arp anti-attack configuration all ...... ARP anti-attack entry-check mode: Vlanif Mode ------------------------------------------------------------------------------- All disabled ------------------------------------------------------------------------------- ARP rate-limit configuration: ------------------------------------------------------------------------------- Global configuration: Interface configuration: Vlan configuration: ------------------------------------------------------------------------------- ARP miss rate-limit configuration: ------------------------------------------------------------------------------- Global configuration: Interface configuration: Vlan configuration: ------------------------------------------------------------------------------- ARP speed-limit for source-MAC configuration: MAC-address suppress-rate(pps)(rate=0 means function disabled) ------------------------------------------------------------------------------- 0001-0001-0001 10 Others 0 ------------------------------------------------------------------------------- The number of configured specified MAC address(es) is 1, spec is 1024. ARP speed-limit for source-IP configuration: IP-address suppress-rate(pps)(rate=0 means function disabled) ------------------------------------------------------------------------------- 10.9.9.2 10 Others 30 ------------------------------------------------------------------------------- The number of configured specified IP address(es) is 1, spec is 1024. ARP miss speed-limit for source-IP configuration: IP-address suppress-rate(pps)(rate=0 means function disabled) ------------------------------------------------------------------------------- 10.10.10.2/32 40 Others 20 ------------------------------------------------------------------------------- The number of configured specified IP address(es) is 1, spec is 1024.# Run the display arp packet statistics command to check statistics on ARP-based packets.
[Switch] display arp packet statistics ARP Pkt Received: sum 8678904 ARP-Miss Msg Received: sum 183 ARP Learnt Count: sum 37 ARP Pkt Discard For Limit: sum 146 ARP Pkt Discard For SpeedLimit: sum 40529 ARP Pkt Discard For Proxy Suppress: sum 0 ARP Pkt Discard For Other: sum 8367601 ARP-Miss Msg Discard For SpeedLimit: sum 20 ARP-Miss Msg Discard For Other: sum 104In the preceding command output, the numbers of ARP packets and ARP Miss messages discarded by the switch are displayed, indicating that the ARP security functions have taken effect.
Configuration File
# Configuration file of the Switch
# sysname Switch # vlan batch 10 20 30 # arp-miss speed-limit source-ip 10.10.10.2 maximum 40 arp speed-limit source-ip 10.9.9.2 maximum 10 arp speed-limit source-mac 0001-0001-0001 maximum 10 arp anti-attack gateway-duplicate enable # arp-miss speed-limit source-ip maximum 20 # interface Vlanif10 ip address 10.8.8.4 255.255.255.0 # interface Vlanif20 ip address 10.9.9.4 255.255.255.0 # interface Vlanif30 ip address 10.10.10.3 255.255.255.0 # interface GigabitEthernet1/0/1 port link-type trunk port trunk allow-pass vlan 10 # interface GigabitEthernet1/0/2 port link-type trunk port trunk allow-pass vlan 20 # interface GigabitEthernet1/0/3 port link-type trunk port trunk allow-pass vlan 30 # return
Applicable Products and Versions
Product |
Product Model |
Software Version |
|---|---|---|
S2700 |
S2700-SI |
V100R006C05 |
S2700-EI |
V100R006C05 |
|
S2710-SI |
V100R006C05 |
|
S2752EI |
V100R006C05 |
|
S3700 |
S3700-SI, S3700-EI |
V100R006C05 |
S3700-HI |
V200R001C00 |
|
S5700 |
S5700-SI |
V200R001C00, V200R002C00, V200R003C00, V200R005C00 |
S5700-EI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00&C01&C02&C03) |
|
S5710-EI |
V200R002C00, V200R003C00, V200R005(C00&C02) |
|
S5720-EI |
V200R007C00, V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5720-LI, S5720S-LI |
V200R010C00, V200R011C00, V200R011C10, V200R012(C00&C20), V200R013C00, V200R019C00, V200R019C10 |
|
S5720-SI, S5720S-SI |
V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5720I-SI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5700-HI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00SPC500&C01&C02) |
|
S5710-HI |
V200R003C00, V200R005(C00&C02&C03) |
|
S5720-HI |
V200R006C00, V200R007(C00&C10), V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5730-HI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5730-SI |
V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5730S-EI |
V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5731-H |
V200R013C02, V200R019C00, V200R019C10 |
|
S5731-S, S5731S-S |
V200R019C00, V200R019C10 |
|
S5731S-H |
V200R019C00, V200R019C10 |
|
S5732-H |
V200R019C00, V200R019C10 |
|
S5735-L, S5735S-L |
V200R019C00, V200R019C10 |
|
S5735S-L-M |
V200R019C00, V200R019C10 |
|
S5735-S, S5735S-S |
V200R019C00, V200R019C10 |
|
S5700 |
S5735-S-I |
V200R019C10 |
S6700 |
S6700-EI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00&C01&C02) |
S6720-LI, S6720S-LI |
V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-SI, S6720S-SI |
V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-EI |
V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720S-EI |
V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-HI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6730-H |
V200R013C02, V200R019C00, V200R019C10 |
|
S6730S-H |
V200R019C10 |
|
S6730-S, S6730S-S |
V200R019C00, V200R019C10 |
Product |
Product Model |
Software Version |
|---|---|---|
S2700 |
S2700-SI |
V100R006C05 |
S2700-EI |
V100R006C05 |
|
S2710-SI |
V100R006C05 |
|
S2752EI |
V100R006C05 |
|
S3700 |
S3700-SI, S3700-EI |
V100R006C05 |
S3700-HI |
V200R001C00 |
|
S5700 |
S5700-SI |
V200R001C00, V200R002C00, V200R003C00, V200R005C00 |
S5700-EI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00&C01&C02&C03) |
|
S5710-EI |
V200R002C00, V200R003C00, V200R005(C00&C02) |
|
S5720-EI |
V200R007C00, V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5720-SI, S5720S-SI |
V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5720I-SI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5700-HI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00SPC500&C01&C02) |
|
S5710-HI |
V200R003C00, V200R005(C00&C02&C03) |
|
S5720-HI |
V200R006C00, V200R007(C00&C10), V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5730-HI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5730-SI |
V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5730S-EI |
V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5731-H |
V200R013C02, V200R019C00, V200R019C10 |
|
S5731-S, S5731S-S |
V200R019C00, V200R019C10 |
|
S5731S-H |
V200R019C00, V200R019C10 |
|
S5732-H |
V200R019C00, V200R019C10 |
|
S5735-S, S5735S-S |
V200R019C00, V200R019C10 |
|
S5700 |
S5735-S-I |
V200R019C10 |
S6700 |
S6700-EI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00&C01&C02) |
S6720-LI, S6720S-LI |
V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-SI, S6720S-SI |
V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-EI |
V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720S-EI |
V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-HI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6730-H |
V200R013C02, V200R019C00, V200R019C10 |
|
S6730S-H |
V200R019C10 |
|
S6730-S, S6730S-S |
V200R019C00, V200R019C10 |
Product |
Product Model |
Software Version |
|---|---|---|
S3700 |
S3700-HI |
V200R001C00 |
S5700 |
S5710-EI |
V200R002C00, V200R003C00, V200R005(C00&C02) |
S5720-EI |
V200R007C00, V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5700-HI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00SPC500&C01&C02) |
|
S5710-HI |
V200R003C00, V200R005(C00&C02&C03) |
|
S5720-HI |
V200R006C00, V200R007(C00&C10), V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5730-HI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5731-H |
V200R013C02, V200R019C00, V200R019C10 |
|
S5731-S, S5731S-S |
V200R019C00, V200R019C10 |
|
S5731S-H |
V200R019C00, V200R019C10 |
|
S5732-H |
V200R019C00, V200R019C10 |
|
S6700 |
S6700-EI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00&C01&C02) |
S6720-EI |
V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720S-EI |
V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-HI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6730-H |
V200R013C02, V200R019C00, V200R019C10 |
|
S6730S-H |
V200R019C10 |
|
S6730-S, S6730S-S |
V200R019C00, V200R019C10 |
Product |
Product Model |
Software Version |
|---|---|---|
S2700 |
S2700-SI |
V100R006C05 |
S2700-EI |
V100R006C05 |
|
S2710-SI |
V100R006C05 |
|
S2752EI |
V100R006C05 |
|
S2720-EI |
V200R006C10, V200R009C00, V200R010C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S2750-EI |
V200R005C00SPC300, V200R006C00, V200R007C00, V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00 |
|
S3700 |
S3700-SI, S3700-EI |
V100R006C05 |
S3700-HI |
V200R001C00 |
|
S5700 |
S5700-LI |
V200R005C00SPC300, V200R006C00, V200R007C00, V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00 |
S5700S-LI |
V200R005C00SPC300, V200R006C00, V200R007C00, V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00 |
|
S5710-X-LI |
V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00 |
|
S5700-SI |
V200R001C00, V200R002C00, V200R003C00, V200R005C00 |
|
S5700-EI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00&C01&C02&C03) |
|
S5710-EI |
V200R002C00, V200R003C00, V200R005(C00&C02) |
|
S5720-EI |
V200R007C00, V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5720-LI, S5720S-LI |
V200R010C00, V200R011C00, V200R011C10, V200R012(C00&C20), V200R013C00, V200R019C00, V200R019C10 |
|
S5720-SI, S5720S-SI |
V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5720I-SI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5700-HI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00SPC500&C01&C02) |
|
S5710-HI |
V200R003C00, V200R005(C00&C02&C03) |
|
S5720-HI |
V200R006C00, V200R007(C00&C10), V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5730-HI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5730-SI |
V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5730S-EI |
V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5731-H |
V200R013C02, V200R019C00, V200R019C10 |
|
S5731-S, S5731S-S |
V200R019C00, V200R019C10 |
|
S5731S-H |
V200R019C00, V200R019C10 |
|
S5732-H |
V200R019C00, V200R019C10 |
|
S5735-L, S5735S-L |
V200R019C00, V200R019C10 |
|
S5735S-L-M |
V200R019C00, V200R019C10 |
|
S5735-S, S5735S-S |
V200R019C00, V200R019C10 |
|
S5700 |
S5735-S-I |
V200R019C10 |
S6700 |
S6700-EI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00&C01&C02) |
S6720-LI, S6720S-LI |
V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-SI, S6720S-SI |
V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-EI |
V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720S-EI |
V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-HI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6730-H |
V200R013C02, V200R019C00, V200R019C10 |
|
S6730S-H |
V200R019C10 |
|
S6730-S, S6730S-S |
V200R019C00, V200R019C10 |

For details about software mappings, visit Hardware Query Tool and search for the desired product model.