Example for Configuring Defense Against ARP MITM Attacks
DAI Overview
Address Resolution Protocol (ARP) security protects network devices against ARP attacks by learning ARP entries, limiting ARP packet rate, and checking ARP packets. In addition to preventing ARP protocol attacks, ARP security also prevents ARP-based network scanning attacks.
Man-in-the-middle (MITM) attack is a frequently launched ARP attack. The attacker functions as the "man in the middle" to intercept data.
To defend against MITM attacks, deploy dynamic ARP inspection (DAI) on the device.
DAI defends against MITM attacks using binding entries. When a device receives an ARP packet, it compares the source IP address, source MAC address, interface information, and VLAN ID of the ARP packet with binding entries. If the ARP packet matches a binding entry, the device considers the ARP packet valid and allows the packet to pass through. If the ARP packet matches no binding entry, the device considers the ARP packet invalid and discards the packet.

The device enabled with DHCP snooping generates DHCP snooping binding entries when DHCP users go online. If a user uses a static IP address, you need to manually configure a static binding entry for the user.
Configuration Notes
In V100R006C05, S2700-SI does not support the DHCP snooping function. This example applies to all models in other versions.
Networking Requirements
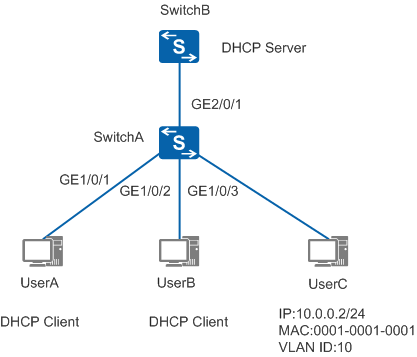
As shown in Figure 1, SwitchA connects to the DHCP server using GE2/0/1, connects to DHCP clients UserA and UserB using GE1/0/1 and GE1/0/2, and connects to UserC configured with a static IP address using GE1/0/3. GE1/0/1, GE1/0/2, GE1/0/3, and GE2/0/1 on SwitchA all belong to VLAN 10. The administrator wants to prevent ARP MITM attacks and theft on authorized user information, and learn the frequency and range of ARP MITM attacks.
Configuration Roadmap
- Enable DHCP snooping and configure a static binding entry.
- Enable DAI so that SwitchA compares the source IP address, source MAC address, interface information, and VLAN ID of the ARP packet with binding entries. This prevents ARP MITM attacks.
Procedure
- Create a VLAN and add interfaces to the VLAN.
# Create VLAN 10, and add GE1/0/1, GE1/0/2, GE1/0/3, and GE2/0/1 to VLAN 10.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] vlan batch 10 [SwitchA] interface gigabitethernet 1/0/1 [SwitchA-GigabitEthernet1/0/1] port link-type access [SwitchA-GigabitEthernet1/0/1] port default vlan 10 [SwitchA-GigabitEthernet1/0/1] quit [SwitchA] interface gigabitethernet 1/0/2 [SwitchA-GigabitEthernet1/0/2] port link-type access [SwitchA-GigabitEthernet1/0/2] port default vlan 10 [SwitchA-GigabitEthernet1/0/2] quit [SwitchA] interface gigabitethernet 1/0/3 [SwitchA-GigabitEthernet1/0/3] port link-type access [SwitchA-GigabitEthernet1/0/3] port default vlan 10 [SwitchA-GigabitEthernet1/0/3] quit [SwitchA] interface gigabitethernet 2/0/1 [SwitchA-GigabitEthernet2/0/1] port link-type trunk [SwitchA-GigabitEthernet2/0/1] port trunk allow-pass vlan 10 [SwitchA-GigabitEthernet2/0/1] quit
- Configure DHCP snooping.
# Enable DHCP snooping globally.
[SwitchA] dhcp enable [SwitchA] dhcp snooping enable
# Enable DHCP snooping in VLAN 10.
[SwitchA] vlan 10 [SwitchA-vlan10] dhcp snooping enable [SwitchA-vlan10] quit
# Configure GE2/0/1 as a trusted interface.
[SwitchA] interface gigabitethernet 2/0/1 [SwitchA-GigabitEthernet2/0/1] dhcp snooping trusted [SwitchA-GigabitEthernet2/0/1] quit
# Configure a static binding table.
[SwitchA] user-bind static ip-address 10.0.0.2 mac-address 0001-0001-0001 interface gigabitethernet 1/0/3 vlan 10
- Enable DAI.
# Enable DAI on GE1/0/1, GE1/0/2, and GE1/0/3. GE1/0/1 is used as an example. Configurations of GE1/0/2 and GE1/0/3 are similar to the configuration of GE1/0/1, and are not mentioned here.
[SwitchA] interface gigabitethernet 1/0/1 [SwitchA-GigabitEthernet1/0/1] arp anti-attack check user-bind enable //Enable dynamic ARP inspection (check ARP packets against a binding table). [SwitchA-GigabitEthernet1/0/1] quit
- Verify the configuration.
# Run the display arp anti-attack configuration check user-bind interface command to check the DAI configuration on each interface. GE1/0/1 is used as an example.
[SwitchA] display arp anti-attack configuration check user-bind interface gigabitethernet 1/0/1 arp anti-attack check user-bind enable
# Run the display arp anti-attack statistics check user-bind interface command to check the number of ARP packets discarded based on DAI. GE1/0/1 is used as an example.
[SwitchA] display arp anti-attack statistics check user-bind interface gigabitethernet 1/0/1 Dropped ARP packet number is 966 Dropped ARP packet number since the latest warning is 605
In the preceding command output, the number of discarded ARP packets on GE1/0/1 is displayed, indicating that the defense against ARP MITM attacks has taken effect.
When you run the display arp anti-attack statistics check user-bind interface command for multiple times on each interface, the administrator can learn the frequency and range of ARP MITM attacks based on the number of discarded ARP packets.
Configuration File
# Configuration file of SwitchA
# sysname SwitchA # vlan batch 10 # dhcp enable # dhcp snooping enable user-bind static ip-address 10.0.0.2 mac-address 0001-0001-0001 interface GigabitEthernet1/0/3 vlan 10 # vlan 10 dhcp snooping enable # interface GigabitEthernet1/0/1 port link-type access port default vlan 10 arp anti-attack check user-bind enable # interface GigabitEthernet1/0/2 port link-type access port default vlan 10 arp anti-attack check user-bind enable # interface GigabitEthernet1/0/3 port link-type access port default vlan 10 arp anti-attack check user-bind enable # interface GigabitEthernet2/0/1 port link-type trunk port trunk allow-pass vlan 10 dhcp snooping trusted # return