Configuring 802.1X and MAC Address Authentication for Access Users on Huawei Agile Controller-Campus
Overview
On a NAC network, the 802.1X, MAC address, and Portal authentication modes are configured on the user access interfaces of a device to meet various authentication requirements. Users can access the network using any authentication mode.
If multiple authentication modes are enabled, the authentication modes take effect in the sequence they are configured. In addition, after multiple authentication modes are deployed, users can be authenticated in different modes by default and assigned different network rights accordingly by the device.
Networking Requirements
Enterprises have high requirements on network security. To prevent unauthorized access and protect information security, an enterprise requests users to pass identity authentication and security check before they access the enterprise network. Only authorized users are allowed to access the enterprise network.
In addition, dumb terminals, such as IP phones and printers, can access the enterprise network only after passing authentication.
The enterprise network has the following characteristics:
The access switches on the network do not support 802.1X authentication.
The enterprise network has a small size and does not have branch networks.
The enterprise has no more than 1000 employees. A maximum of 2000 users, including guests, access the network every day.
Dumb terminals, such as IP phones and printers, are connected to the enterprise network.
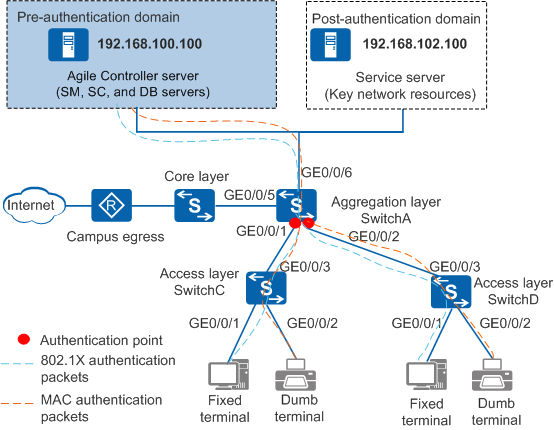
To reduce network reconstruction investment, you are advised to configure the 802.1X authentication function on the aggregation switch and connect a single centralized authentication server to the aggregation switch in bypass mode. MAC address authentication needs to be configured for dumb terminals.
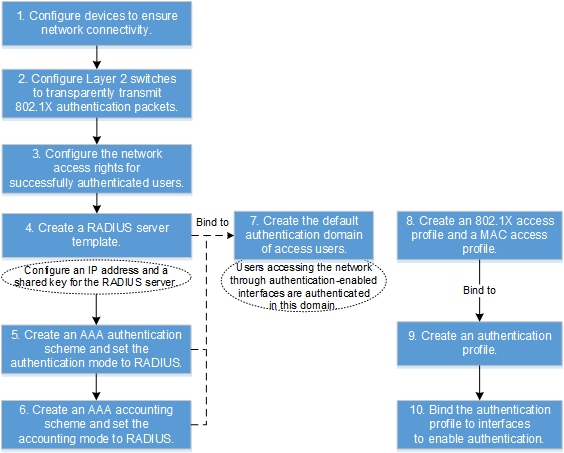
Configuration Logic
Item |
Description |
|---|---|
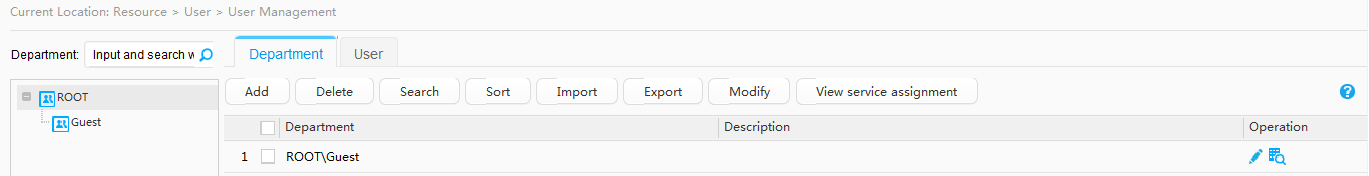
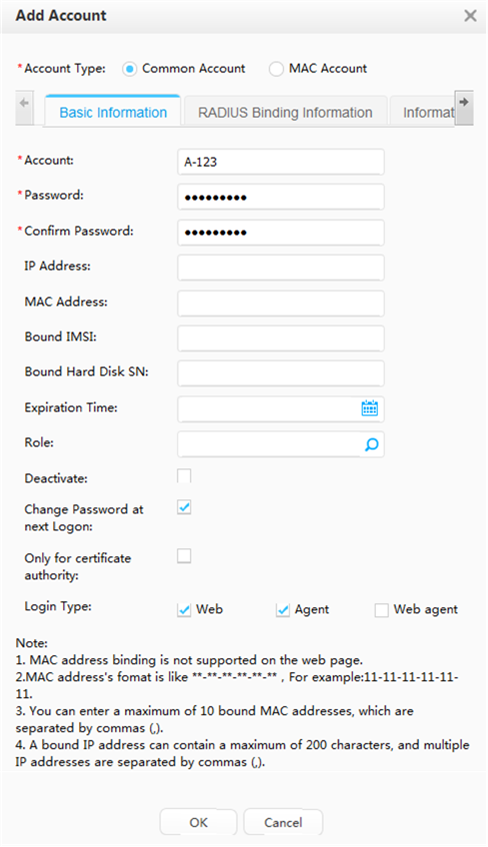
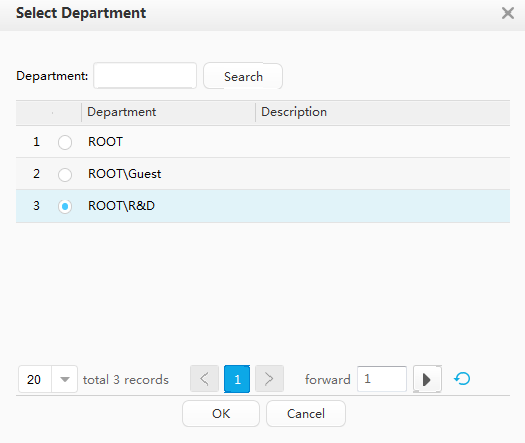
Creating a department and an account |
- |
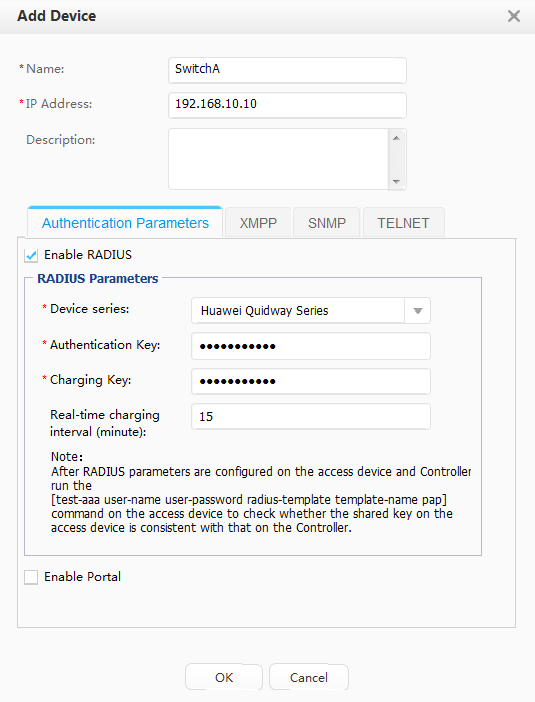
Adding switches |
Set parameters for switches connected to the Agile Controller-Campus. |
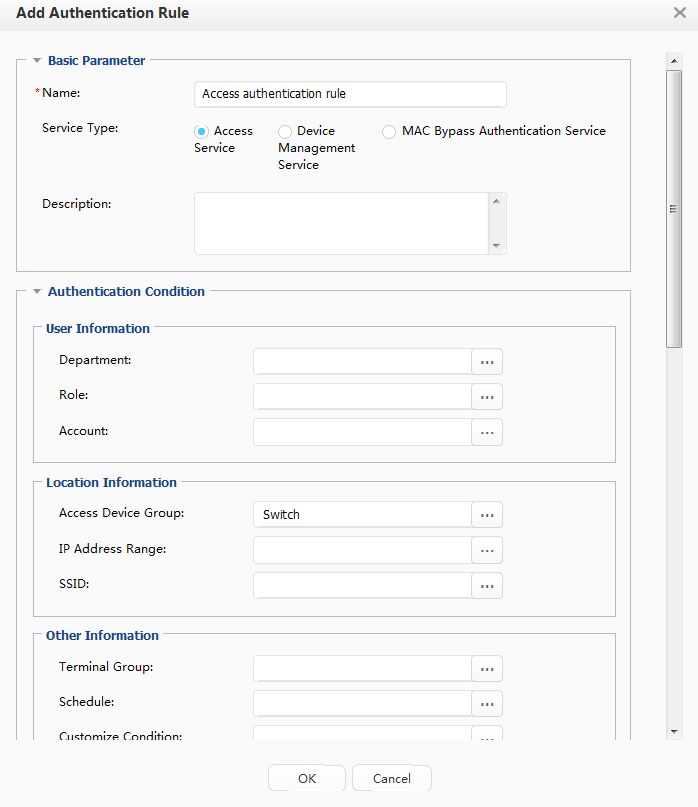
Adding an authentication rule |
Configure the conditions for users to pass the authentication. |
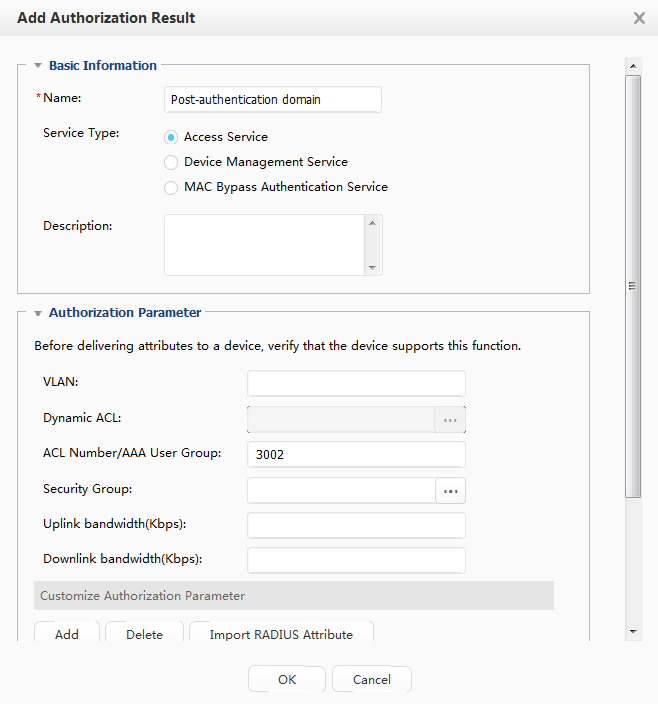
Adding an authorization result |
Create network access right profiles so that users granted with different profiles have different network access rights. |
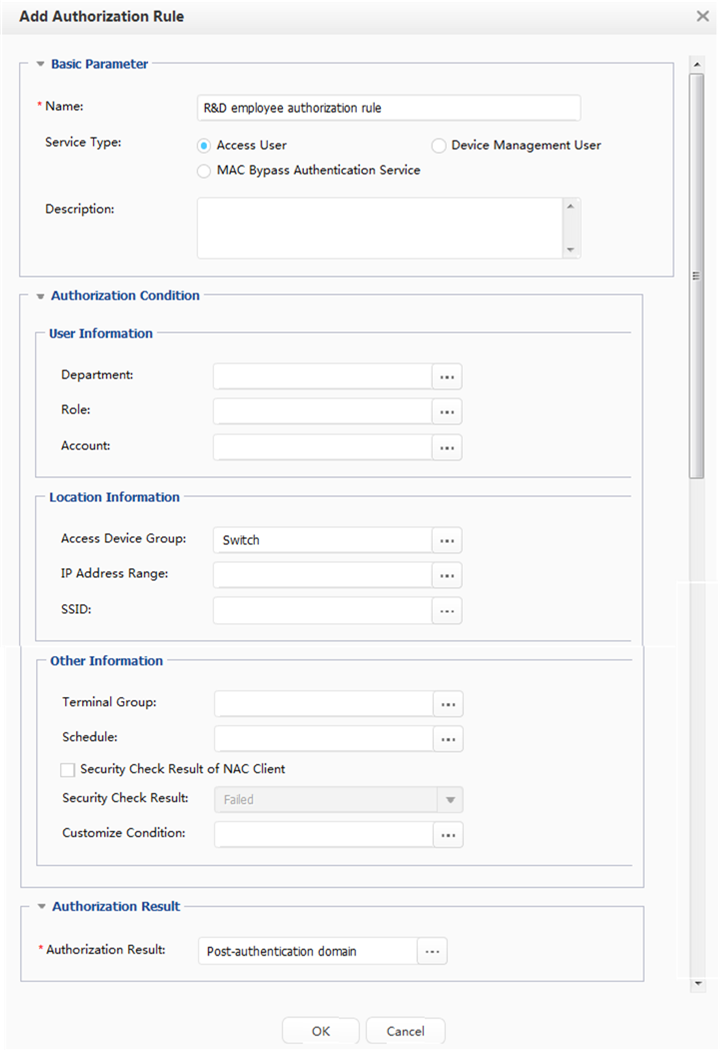
Adding an authorization rule |
Select network access right profiles and users in an authorization rule so that specified network access rights are granted to specific users. |
Configuration Notes
This configuration example applies to all switches running V200R009C00 or a later version, Huawei Agile Controller-Campus in V100R001 functions as the RADIUS server. For the Agile Controller-Campus, the version required is V100R001, V100R002, V100R003.
The RADIUS authentication and accounting shared keys and Portal shared key on the switch must be the same as those on the Agile Controller-Campus server.
By default, the switch allows the packets from RADIUS server to pass. You do not need to configure authentication-free rules for the server on the switch.
When you run the access-user arp-detect command to configure the IP address and MAC address of the user gateway as the source IP address and source MAC address of user offline detection packets, ensure that the MAC address of the gateway remains unchanged, especially in active/standby switchover scenarios. If the gateway MAC address is changed, ARP entries of terminals will be incorrect on the device, and the terminals cannot communicate with the device.
Data Plan
Item |
Data |
|---|---|
Agile Controller-Campus |
IP address: 192.168.100.100 |
Post-authentication domain server |
IP address: 192.168.102.100 |
Aggregation switch (SwitchA) |
|
Access switch (SwitchC) |
User VLAN ID: 200 |
Access switch (SwitchD) |
User VLAN ID: 200 |
Item |
Data |
|---|---|
RADIUS scheme |
|
ACL number of the post-authentication domain |
3002 |
Item |
Data |
|---|---|
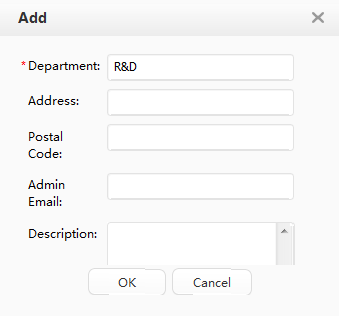
Department |
R&D department |
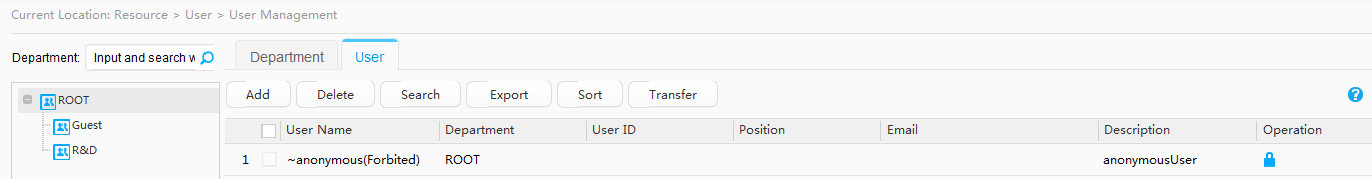
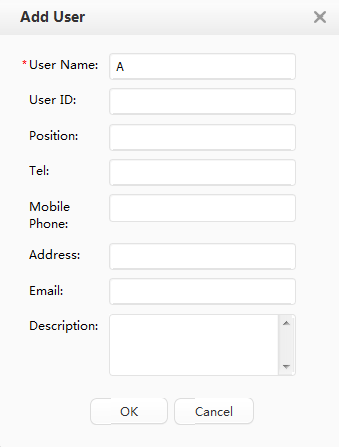
Access user |
User name: A Wired access account: A-123 Password: Huawei123 |
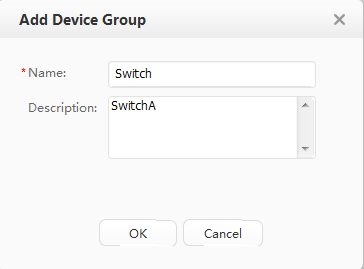
Device group |
Wired device group: Switch |
| Switch IP address | SwitchA: 192.168.10.10 |
RADIUS authentication key |
Huawei@2014 |
Charging Key |
Huawei@2014 |
Procedure
- Configure the access switches.
- Configure the aggregation switch.
- Configure the Agile Controller-Campus.
- Verify the configuration.
- An employee can only access the Agile Controller-Campus server before passing the authentication.
- After passing the authentication, the employee can access resources in the post-authentication domain.
- After the employee passes the authentication, run the display access-user command on the switch. The command output shows information about the online employee.
Configuration Files
SwitchA configuration file
# sysname SwitchA # vlan batch 100 200 # authentication-profile name p1 dot1x-access-profile d1 mac-access-profile m1 # domain isp # access-user arp-detect vlan 200 ip-address 192.168.200.1 mac-address 2222-1111-1234 # radius-server template rd1 radius-server shared-key cipher %#%#FP@&C(&{$F2HTlPxg^NLS~KqA/\^3Fex;T@Q9A](%#%# radius-server authentication 192.168.100.100 1812 weight 80 radius-server accounting 192.168.100.100 1813 weight 80 # dot1x-access-profile name d1 # mac-access-profile name m1 mac-authen username fixed A-123 password cipher %#%#'Fxw8E,G-81(A3U<^HH9Sj\:&hTdd>R>HILQYLtW%#%# # acl number 3002 rule 1 permit ip destination 192.168.102.100 0 rule 2 deny ip # aaa authentication-scheme abc authentication-mode radius accounting-scheme acco1 accounting-mode radius accounting realtime 15 domain isp authentication-scheme abc accounting-scheme acco1 radius-server rd1 # interface Vlanif100 ip address 192.168.10.10 255.255.255.0 # interface Vlanif200 ip address 192.168.200.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 200 authentication-profile p1 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 200 authentication-profile p1 # interface GigabitEthernet0/0/6 port link-type trunk port trunk allow-pass vlan 100 # ip route-static 192.168.100.0 255.255.255.0 192.168.10.10 ip route-static 192.168.102.0 255.255.255.0 192.168.10.10 # returnSwitchC configuration file
# sysname SwitchC # vlan batch 200 # l2protocol-tunnel user-defined-protocol 802.1x protocol-mac 0180-c200-0003 group-mac 0100-0000-0002 # interface GigabitEthernet0/0/1 port link-type access port default vlan 200 l2protocol-tunnel user-defined-protocol 802.1x enable # interface GigabitEthernet0/0/2 port link-type access port default vlan 200 l2protocol-tunnel user-defined-protocol 802.1x enable # interface GigabitEthernet0/0/3 port link-type trunk port trunk allow-pass vlan 200 l2protocol-tunnel user-defined-protocol 802.1x enable # return