Delivering VLANs or ACLs to Successfully Authenticated Users on Huawei Agile Controller-Campus
Overview
- ACL-based authorization is classified into:
ACL description-based authorization: If ACL description-based authorization is configured on the server, authorization information includes the ACL description. The device matches ACL rules based on the ACL description authorized by the server to control user rights. The ACL number, corresponding description, and ACL rule must be configured on the device.
The standard RADIUS attribute (011) Filter-Id is used.
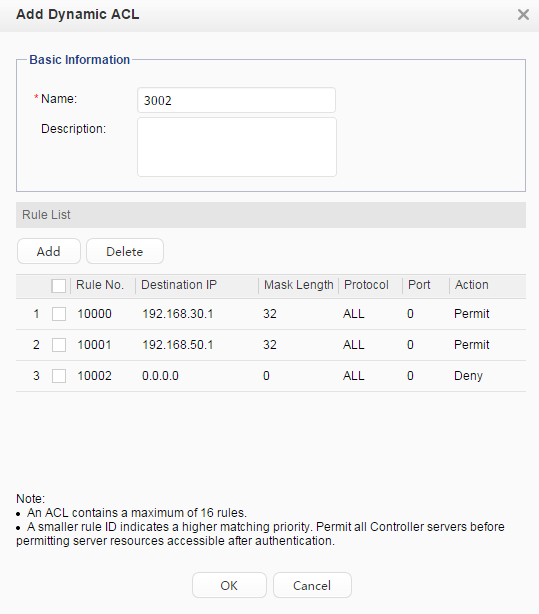
Dynamic ACL-based authorization: The server authorizes rules in an ACL to the device. Users can access network resources controlled using this ACL. The ACL and ACL rules must be configured on the server. The ACL does not need to be configured on the device.
The Huawei proprietary RADIUS attribute (26-82) HW-Data-Filter is used.
Dynamic VLAN: If dynamic VLAN delivery is configured on the server, authorization information includes the delivered VLAN attribute. After the device receives the delivered VLAN attribute, it changes the VLAN of the user to the delivered VLAN.
The delivered VLAN does not change or affect the interface configuration. The delivered VLAN, however, takes precedence over the VLAN configured on the interface. That is, the delivered VLAN takes effect after the authentication succeeds, and the configured VLAN takes effect after the user goes offline.
The following standard RADIUS attributes are used for dynamic VLAN delivery:- (064) Tunnel-Type (It must be set to VLAN or 13.)
- (065) Tunnel-Medium-Type (It must be set to 802 or 6.)
- (081) Tunnel-Private-Group-ID (For devices running versions earlier than V200R012C00, it can be the VLAN ID or VLAN description. For devices running V200R012C00 and later versions, it can be the VLAN ID, VLAN description, VLAN name, or VLAN pool.)
To ensure that the RADIUS server delivers VLAN information correctly, all the three RADIUS attributes must be used. In addition, the Tunnel-Type and Tunnel-Medium-Type attributes must be set to the specified values.

The following uses ACL number and dynamic VLAN delivery as an example. The configuration differences between ACL number delivery and dynamic ACL delivery are described in notes.
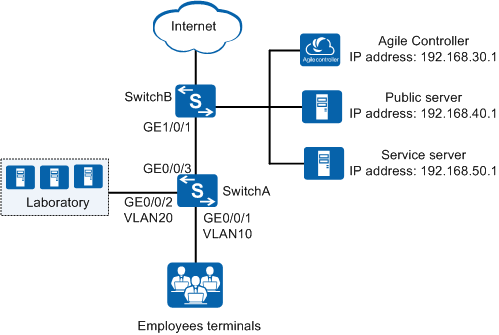
Networking Requirements
- Before passing authentication, terminals can access the public server (with IP address 192.168.40.1), and download the 802.1X client or update the antivirus database.
- After passing authentication, terminals can access the service server (with IP address 192.168.50.1) and devices in the laboratory (with VLAN ID 20 and IP address segment 192.168.20.10-192.168.20.100).
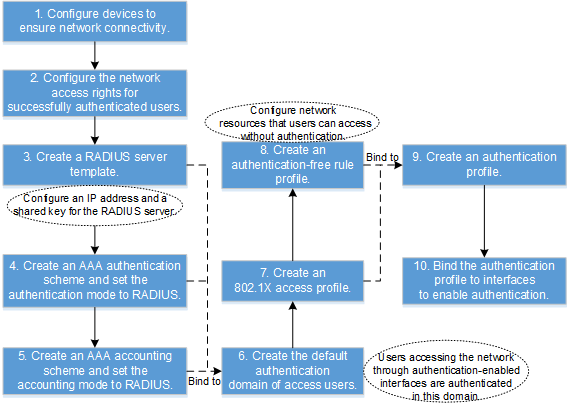
Configuration Logic
Item |
Description |
|---|---|
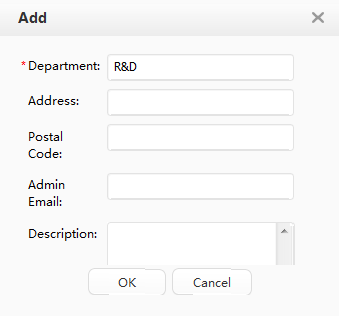
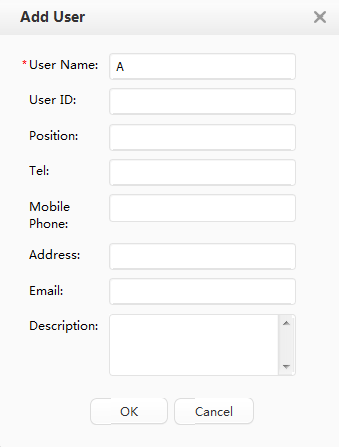
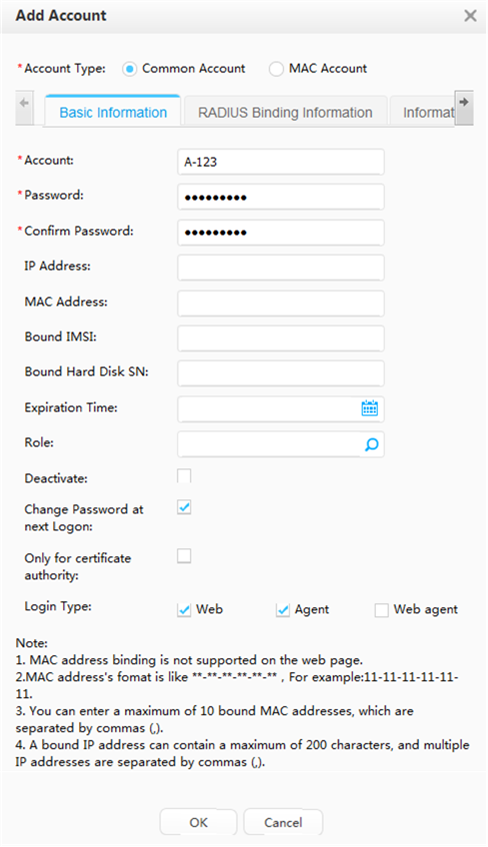
Creating a department and an account |
- |
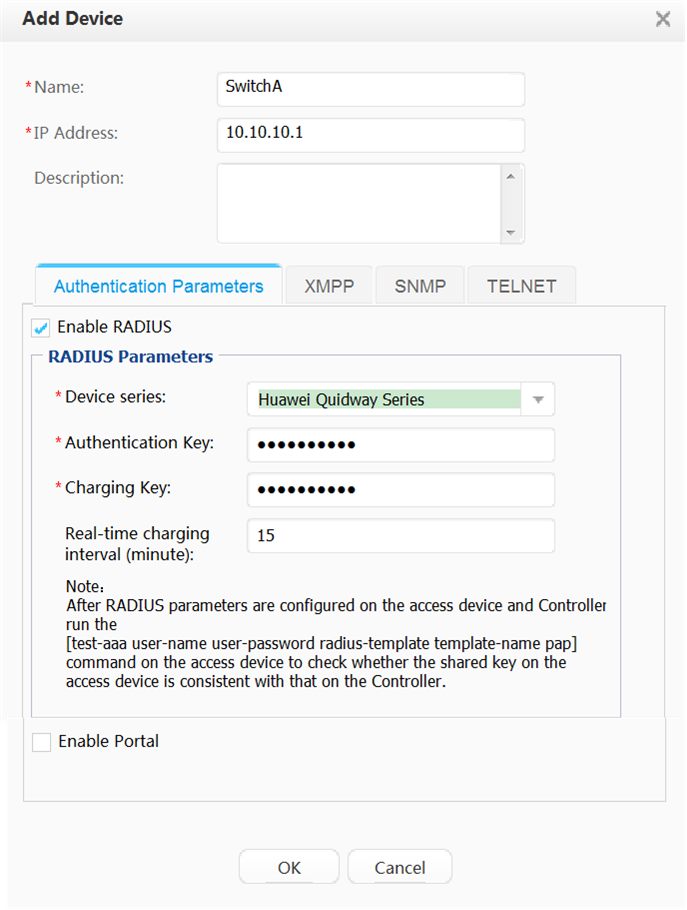
Adding switches |
Set parameters for switches connected to the Agile Controller-Campus. |
(Optional) adding an authentication rule |
Configure the conditions for users to pass the authentication. If no authentication rule is created, the default authentication rule (that allows all users to pass the authentication) of the Agile Controller-Campus is used. |
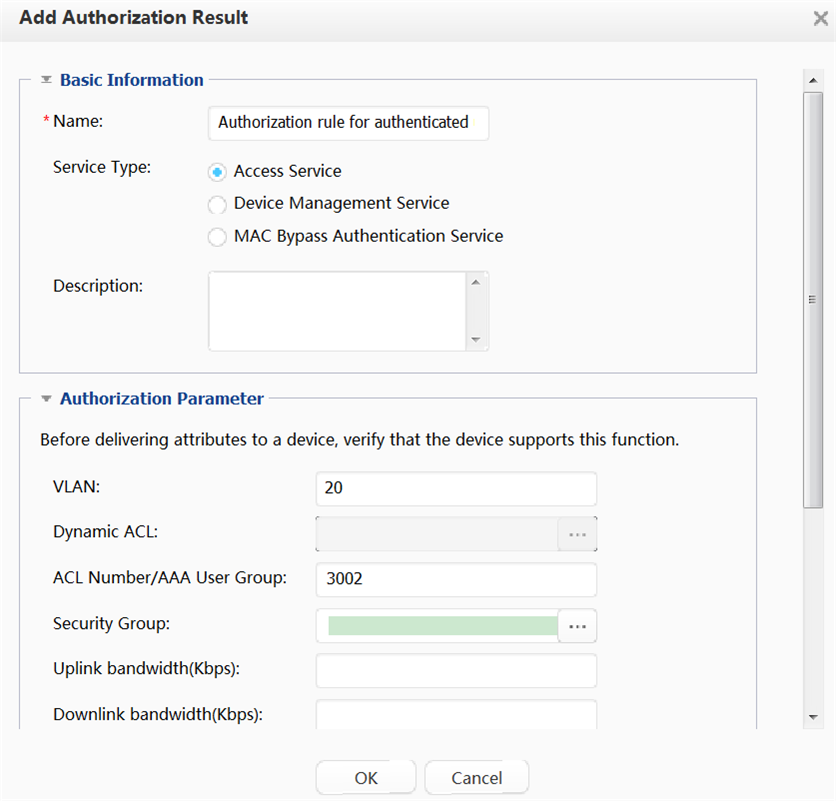
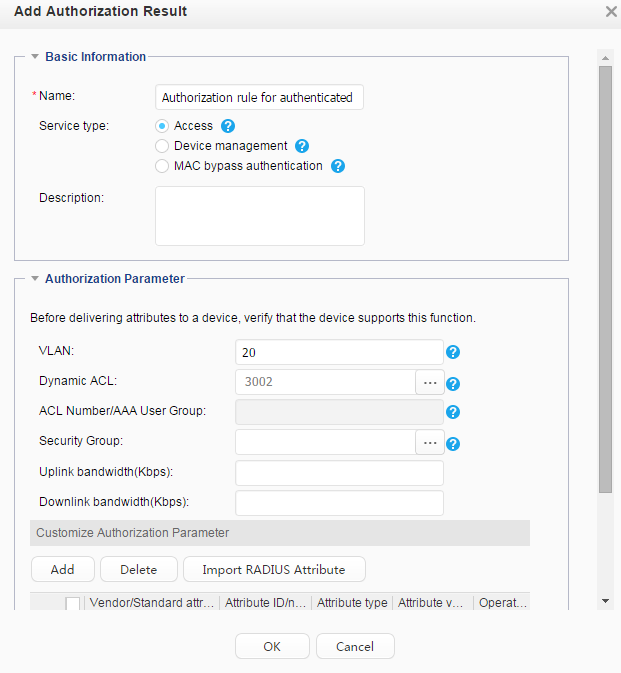
Adding an authorization result |
Create network access right profiles so that users granted with different profiles have different network access rights. |
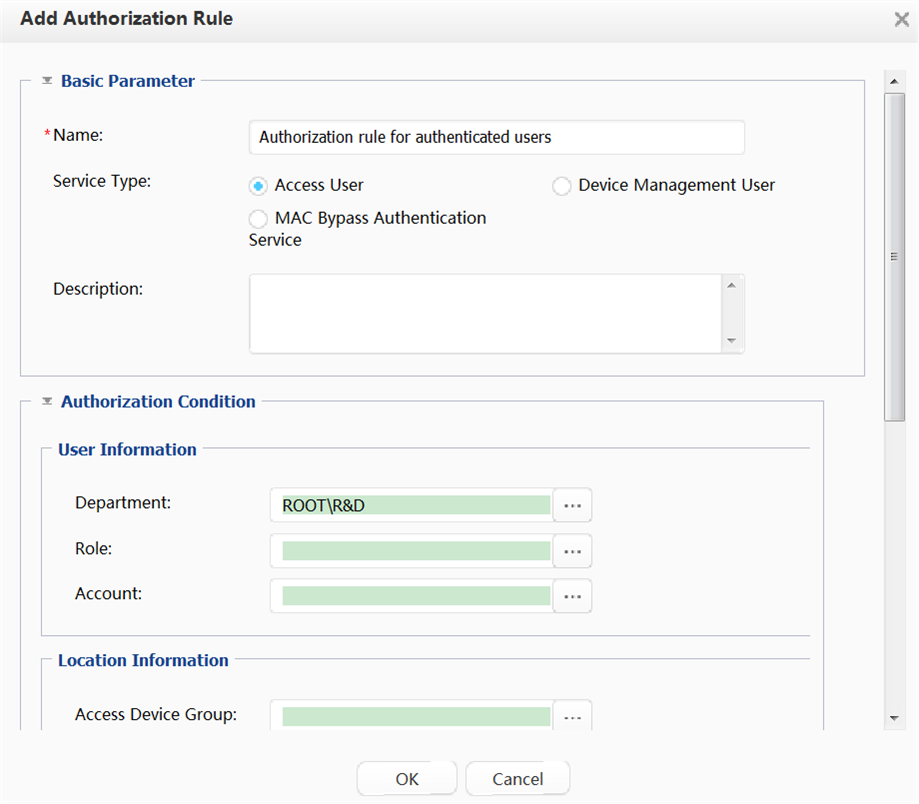
Adding an authorization rule |
Select network access right profiles and users in an authorization rule so that specified network access rights are granted to specific users. |
Configuration Notes
This configuration example applies to all switches running V200R009C00 or a later version, Huawei Agile Controller-Campus in V100R001 functions as the RADIUS server. For the Agile Controller-Campus, the version required is V100R001, V100R002, V100R003.
When the device supports UCL groups, using UCL groups to configure authorization rules is recommended. For details, see section "AAA Configuration" > "Configuring Authorization Rules" in the Configuration Guide - User Access and Authentication.
When you run the access-user arp-detect command to configure the IP address and MAC address of the user gateway as the source IP address and source MAC address of user offline detection packets, ensure that the MAC address of the gateway remains unchanged, especially in active/standby switchover scenarios. If the gateway MAC address is changed, ARP entries of terminals will be incorrect on the device, and the terminals cannot communicate with the device.
Data Plan
Item |
Data |
|---|---|
RADIUS scheme |
|
Resources accessible to users before authentication |
Access rights to the public server are configured using an authentication-free rule. The name of the authentication-free rule profile is default_free_rule. |
Resources accessible to users after authentication |
Access rights to the laboratory are granted using a dynamic VLAN. The VLAN ID is 20. Access rights to the service server are granted using an ACL number. The ACL number is 3002. |
Item |
Data |
|---|---|
Department |
R&D department |
Access user |
User name: A Wired access account: A-123 Password: Huawei123 |
Switch IP address |
SwitchA: 10.10.10.1 |
RADIUS authentication key |
Huawei@123 |
RADIUS accounting key |
Huawei@123 |
Procedure
- Configure access switch SwitchA.
- Configure the Agile Controller-Campus.
- Verify the configuration.
- An employee can only access the Agile Controller-Campus server and public server before passing authentication.
- An employee can access the Agile Controller-Campus server, public server, service server, and laboratory after passing authentication.
- After the employee passes authentication, run the display access-user command on the switch. The command output shows information about the online employee.
Configuration File
#
sysname SwitchA
#
vlan batch 10 20
#
authentication-profile name p1
dot1x-access-profile d1
free-rule-template default_free_rule
access-domain huawei force
#
access-user arp-detect vlan 10 ip-address 192.168.1.10 mac-address 2222-1111-1234
#
radius-server template rd1
radius-server shared-key cipher %^%#FP@&C(&{$F2HTlPxg^NLS~KqA/\^3Fex;T@Q9A](%^%#
radius-server authentication 192.168.30.1 1812 weight 80
radius-server accounting 192.168.30.1 1813 weight 80
#
acl number 3002
rule 1 permit ip destination 192.168.30.1 0
rule 2 permit ip destination 192.168.50.1 0
rule 3 deny ip
#
free-rule-template name default_free_rule
free-rule 10 destination ip 192.168.40.0 mask 255.255.255.0
#
aaa
authentication-scheme abc
authentication-mode radius
accounting-scheme acco1
accounting-mode radius
accounting realtime 15
domain huawei
authentication-scheme abc
accounting-scheme acco1
radius-server rd1
#
interface Vlanif10
ip address 192.168.1.10 255.255.255.0
#
interface GigabitEthernet0/0/1
port link-type hybrid
port hybrid pvid vlan 10
port hybrid untagged vlan 10
authentication-profile p1
#
interface GigabitEthernet0/0/2
port link-type hybrid
port hybrid untagged vlan 20
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 10 20
#
interface LoopBack1
ip address 10.10.10.1 255.255.255.0
#
dot1x-access-profile name d1
#
return