Example for Configuring a Layer 3 Switch to Work with a Firewall for Internet Access
Layer 3 Switch
Layer 3 switches provide the routing function, which indicates a network-layer function in the OSI model.
Layer 3 switches can work at Layer 2 and Layer 3 and be deployed at the access layer or aggregation layer as user gateways.
Configuration Notes
This example uses firewall configurations of USG6650 V500R001C60. For other firewall configurations, see the corresponding documentation.
- For the products and versions applicable when a switch functions as a DHCP server, see Examples for Applicable Products and Versions.
Networking Requirements
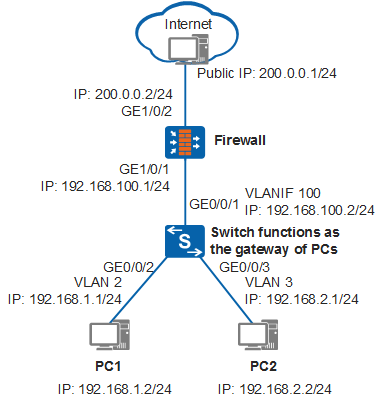
In Figure 1, a company has multiple departments that belong to different network segments, and each department needs to access the Internet. It is required that users access the Internet through the Layer 3 switch and firewall and that the Layer 3 switch function as the gateway of users.
Configuration Roadmap
The configuration roadmap is as follows:
Configure the switch as the gateway of users to allow users to communicate across network segments through VLANIF interfaces.
Configure the switch as the DHCP server to assign IP addresses to users.
Configure an interzone security policy for the firewall so that packets of different zones can be forwarded.
Configure the PAT function on the firewall to enable intranet users to access the Internet.
Procedure
- Configure the switch.
# Configure the interfaces connected to users and corresponding VLANIF interfaces.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] vlan batch 2 3 [Switch] interface gigabitethernet 0/0/2 [Switch-GigabitEthernet0/0/2] port link-type access //Set the link type of the interface to access. [Switch-GigabitEthernet0/0/2] port default vlan 2 //Add the interface to VLAN 2. [Switch-GigabitEthernet0/0/2] quit [Switch] interface gigabitethernet 0/0/3 [Switch-GigabitEthernet0/0/3] port link-type access [Switch-GigabitEthernet0/0/3] port default vlan 3 [Switch-GigabitEthernet0/0/3] quit [Switch] interface vlanif 2 [Switch-Vlanif2] ip address 192.168.1.1 24 [Switch-Vlanif2] quit [Switch] interface vlanif 3 [Switch-Vlanif3] ip address 192.168.2.1 24 [Switch-Vlanif3] quit
# Configure the interface connected to the firewall and corresponding VLANIF interface.
[Switch] vlan batch 100 [Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] port link-type access [Switch-GigabitEthernet0/0/1] port default vlan 100 [Switch-GigabitEthernet0/0/1] quit [Switch] interface vlanif 100 [Switch-Vlanif100] ip address 192.168.100.2 24 [Switch-Vlanif100] quit
# Configure the default route.
[Switch] ip route-static 0.0.0.0 0.0.0.0 192.168.100.1 //The next hop of the default route is the IP address 192.168.100.1 of the firewall interface.# Configure the DHCP server.
[Switch] dhcp enable [Switch] interface vlanif 2 [Switch-Vlanif2] dhcp select interface //DHCP uses an interface address pool to assign IP addresses to intranet users. [Switch-Vlanif2] dhcp server dns-list 114.114.114.114 223.5.5.5 //The configured DNS-list 114.114.114.114 is a public DNS server address, which is the same for carriers. In practice, the DNS-list address needs to be configured based on the DNS assigned to a carrier. [Switch-Vlanif2] quit [Switch] interface vlanif 3 [Switch-Vlanif3] dhcp select interface [Switch-Vlanif3] dhcp server dns-list 114.114.114.114 223.5.5.5 [Switch-Vlanif3] quit
- Configure the firewall.
# Configure an IP address for the interface connected to the switch.
<USG> system-view [USG] interface gigabitethernet 1/0/1 [USG-GigabitEthernet1/0/1] ip address 192.168.100.1 255.255.255.0 [USG-GigabitEthernet1/0/1] quit
# Configure an IP address for the interface connected to the Internet.
[USG] interface gigabitethernet 1/0/2 [USG-GigabitEthernet1/0/2] ip address 200.0.0.2 255.255.255.0 //The IP address of the interface connected to the Internet is on the same network segment as the public IP address. [USG-GigabitEthernet1/0/2] quit# Configure a default route and a return route.
[USG] ip route-static 0.0.0.0 0.0.0.0 200.0.0.1 //Configure a static default route with the next hop pointing to the public IP address 200.0.0.1. [USG] ip route-static 192.168.0.0 255.255.0.0 192.168.100.2 //Configure a return route with the next hop pointing to the IP address 192.168.100.2 of the switch's uplink interface.
# Configure security zones.
[USG] firewall zone trust //Configure a trust zone. [USG-zone-trust] add interface gigabitethernet 1/0/1 [USG-zone-trust] quit [USG] firewall zone untrust //Configure an untrust zone. [USG-zone-untrust] add interface gigabitethernet 1/0/2 [USG-zone-untrust] quit
# Configure a security policy to allow inter-zone access.[USG6600] security-policy [USG6600-policy-security] rule name policy1 [USG6600-policy-security-rule-policy1] source-zone trust [USG6600-policy-security-rule-policy1] destination-zone untrust [USG6600-policy-security-rule-policy1] source-address 192.168.0.0 mask 255.255.0.0 [USG6600-policy-security-rule-policy1] action permit [USG6600-policy-security-rule-policy1] quit [USG6600-policy-security] quit
# Configure a PAT address pool to allow interface address translation.[USG6600] nat address-group addressgroup1 [USG6600-address-group-addressgroup1] mode pat [USG6600-address-group-addressgroup1] route enable [USG6600-address-group-addressgroup1] section 0 200.0.0.2 200.0.0.2 //Translated public IP address [USG6600-address-group-addressgroup1] quit# Configure a PAT policy so that source IP addresses are automatically translated when devices on a specified network segment of an internal network access the Internet.[USG6600] nat-policy [USG6600-policy-nat] rule name policy_nat1 [USG6600-policy-nat-rule-policy_nat1] source-zone trust [USG6600-policy-nat-rule-policy_nat1] destination-zone untrust [USG6600-policy-nat-rule-policy_nat1] source-address 192.168.0.0 mask 255.255.0.0 //Source IP address that can be translated using PAT [USG6600-policy-nat-rule-policy_nat1] action nat address-group addressgroup1 [USG6600-policy-nat-rule-policy_nat1] quit [USG6600-policy-nat] quit [USG6600] quit - Check the configuration.
Configure an IP address 192.168.1.2/24 and a gateway address 192.168.1.1 for PC1, and configure an IP address 192.168.2.2/24 and a gateway address 192.168.2.1 for PC2.
Configure an IP address 200.0.0.1/24 and a gateway address 200.0.0.2 for external network.
After the configurations are complete, PC1 and PC2 can ping the external network IP address 200.0.0.1/24 and access the Internet.
Configuration Files
- Switch configuration file
# sysname Switch # vlan batch 2 to 3 100 # dhcp enable # interface Vlanif2 ip address 192.168.1.1 255.255.255.0 dhcp select interface dhcp server dns-list 114.114.114.114 223.5.5.5 # interface Vlanif3 ip address 192.168.2.1 255.255.255.0 dhcp select interface dhcp server dns-list 114.114.114.114 223.5.5.5 # interface Vlanif100 ip address 192.168.100.2 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type access port default vlan 100 # interface GigabitEthernet0/0/2 port link-type access port default vlan 2 # interface GigabitEthernet0/0/3 port link-type access port default vlan 3 # ip route-static 0.0.0.0 0.0.0.0 192.168.100.1 # return
- USG configuration file
# interface GigabitEthernet1/0/1 ip address 192.168.100.1 255.255.255.0 # interface GigabitEthernet0/0/2 ip address 200.0.0.2 255.255.255.0 # firewall zone trust set priority 85 add interface GigabitEthernet1/0/1 # firewall zone untrust set priority 5 add interface GigabitEthernet0/0/2 # ip route-static 0.0.0.0 0.0.0.0 200.0.0.1 ip route-static 192.168.0.0 255.255.0.0 192.168.100.2 # nat address-group addressgroup1 0 mode pat route enable section 0 200.0.0.2 200.0.0.2 # security-policy rule name policy1 source-zone trust destination-zone untrust source-address 192.168.0.0 mask 255.255.0.0 action permit # nat-policy rule name policy_nat1 source-zone trust destination-zone untrust source-address 192.168.0.0 mask 255.255.0.0 action nat address-group addressgroup1 # return
Examples for Applicable Products and Versions
Series |
Product Model |
Software Version |
|---|---|---|
S2700 |
S2720-EI |
V200R009C00, V200R010C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
S2750-EI |
V200R005C00SPC300, V200R006C00, V200R007C00, V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00 |
|
S3700 |
S3700-SI, S3700-EI |
V100R006C05 |
S3700-HI |
V200R001C00 |
|
S5700 |
S5700-LI |
V200R005C00SPC300, V200R006C00, V200R007C00, V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00 |
S5700S-LI |
V200R005C00SPC300, V200R006C00, V200R007C00, V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00 |
|
S5700-SI |
V200R001C00, V200R002C00, V200R003C00, V200R005C00 |
|
S5700-EI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00&C01&C02&C03) |
|
S5700-HI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00SPC500&C01&C02) |
|
S5710-X-LI |
V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00 |
|
S5710-EI |
V200R001C00, V200R002C00, V200R003C00, V200R005(C00&C02) |
|
S5710-HI |
V200R003C00, V200R005(C00&C02&C03) |
|
S5720-LI, S5720S-LI |
V200R010C00, V200R011C00, V200R011C10, V200R012(C00&C20), V200R013C00, V200R019C00, V200R019C10 |
|
S5720-SI, S5720S-SI |
V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5720I-SI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5720-EI |
V200R007C00, V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5720-HI |
V200R006C00, V200R007(C00&C10), V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5730-HI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5730-SI |
V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5730S-EI |
V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5731-H |
V200R013C02, V200R019C00, V200R019C10 |
|
S5731-S, S5731S-S |
V200R019C00, V200R019C10 |
|
S5731S-H |
V200R019C00, V200R019C10 |
|
S5732-H |
V200R019C00, V200R019C10 |
|
S5735-L, S5735S-L |
V200R019C00, V200R019C10 |
|
S5735S-L-M |
V200R019C00, V200R019C10 |
|
S5735-S, S5735S-S |
V200R019C00, V200R019C10 |
|
S5700 |
S5735-S-I |
V200R019C10 |
S6700 |
S6700-EI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00&C01&C02) |
S6720-LI, S6720S-LI |
V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-SI, S6720S-SI |
V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-EI |
V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720S-EI |
V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-HI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6730-H |
V200R013C02, V200R019C00, V200R019C10 |
|
S6730-S, S6730S-S |
V200R019C00, V200R019C10 |
|
S6730S-H |
V200R019C10 |
|
S7700 |
S7703, S7706, S7712 |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005C00, V200R006C00, V200R007C00, V200R008C00, V200R009C00, V200R010C00, V200R011C10, V200R012C00, V200R013C00, V200R013C02, V200R019C00, V200R019C10 |
S7703 PoE |
V200R013C00, V200R019C00, V200R019C10 |
|
S7706 PoE |
V200R013C00, V200R019C00, V200R019C10 |
|
S9700 |
S9703, S9706, S9712 |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005C00, V200R006C00, V200R007(C00&C10), V200R008C00, V200R009C00, V200R010C00, V200R011C10, V200R012C00, V200R013C00 |