ARP Gateway Anti-Collision
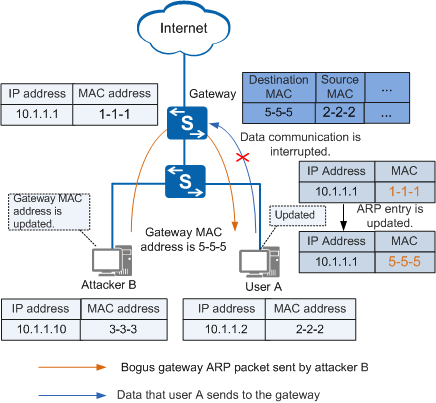
As shown in Figure 1, attacker B forges the gateway address to send a bogus ARP packet to user A. User A considers the attacker to be the gateway and records an incorrect ARP entry for the gateway. As a result, the gateway cannot receive packets from user A and their communication is interrupted.
To prevent bogus gateway attacks, enable ARP gateway anti-collision on the gateway. The gateway considers a gateway collision to have occurred when a received ARP packet meets either of the following conditions:
The source IP address in the ARP packet is the same as the IP address of the VLANIF interface matching the physical inbound interface of the packet.
The source IP address in the ARP packet is the virtual IP address of the inbound interface but the source MAC address in the ARP packet is not the virtual MAC address of the Virtual Router Redundancy Protocol (VRRP) group.

A VRRP group, also called a virtual router, serves as the default gateway for hosts on a LAN. A virtual router has a virtual MAC address that is generated based on the virtual router ID. The virtual MAC address is in the format of 00-00-5E-00-01-{VRID}(VRRP). The virtual router sends ARP Reply packets using the virtual MAC address instead of the interface MAC address.
The device generates an ARP anti-collision entry and discards the received packets with the same source MAC address and VLAN ID in a specified period. This function prevents ARP packets with the bogus gateway address from being broadcast in a VLAN.
In addition, you can enable gratuitous ARP packet sending on the device to broadcast gratuitous ARP packets to all user hosts so that the bogus ARP entries are modified. The gratuitous ARP packets are broadcast to all users so that incorrect ARP entries are corrected.