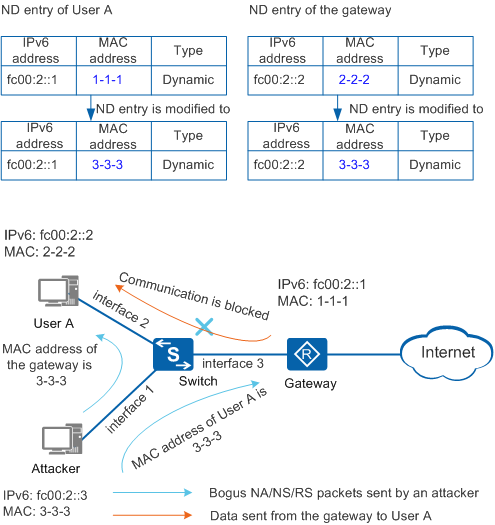
Address Spoofing Attack Defense
As shown in Figure 1, an attacker uses the address of user A to send an NA/NS/RS packet to the gateway. The gateway records an incorrect mapping for the address of user A in the ND entries. Then the attacker obtains the data sent from the gateway to user A. In addition, the attacker uses the address of gateway to send an NA/NS/RS packet to user A. User A records an incorrect mapping for the gateway. Then the attacker obtains the data sent from user A to the gateway. As a result, user A cannot receive valid packets and data of user A may be leaked.
To prevent address spoofing attacks, configure ND snooping on interface 1 and interface 3 of the Switch. Configure interface 3 that connects to the gateway as the trusted interface and enable ND packet validity check on interface 1 that connects to users. When receiving NA/NS/RS packets from interface 1, the Switch checks packet validity against the dynamic ND snooping binding table and filters out forged NA/NS/RS packets.