RA Attack Defense
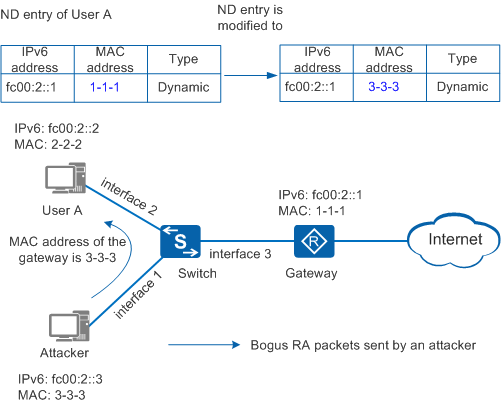
An RA packet can carry much network configuration information, including the default router, the prefix list, and whether to use the DHCPv6 server for stateful address allocation. As shown in Figure 1, an attacker sends a forged RA packet to change the network configuration on a host. Then the host cannot communicate with other hosts. Common RA attacks include:
- Forged RA packets with non-existing prefixes cause authorized hosts to modify their routing tables.
- Forged RA packets with the gateway MAC address cause authorized hosts to record incorrect ND entries for the gateway. If an attacker forges the Router Lifetime field in RA packets, authorized hosts change the default gateway (default router) to another gateway.
- If an attacker sends RA packets with a forged DHCPv6 server address and M bit, the authorized hosts use the forged IP addresses allocated by the bogus DHCPv6 server.
The Router Lifetime field in an RA packet indicates the lifetime of the sender router that functions as the default router. If the value is 0, the router cannot function as the default router but other information in the RA packet is still valid.
The M bit is the managed address configuration bit, and the value can be 0 or 1. The value 0 indicates stateless address allocation. A host uses stateless protocols such as ND to obtain an IPv6 address. The value 1 indicates stateful address allocation. A host uses stateful protocols such as DHCPv6 to obtain an IPv6 address.
To defend against RA attacks, enable ND snooping on interface 1 and interface 3 of the Switch, and configure interface 3 connecting to the gateway as a trusted interface. Then, the Switch discards RA packets received from interface 1 and processes only packets received from the trusted interface, which prevents RA attacks.

If administrators need to filter RA packets more precisely, configure IPv6 RA guard. For details, see IPv6 RA Guard Configuration.