Security Protocols
AH and ESP are the two IP-based transport-layer protocols used by IPSec to provide security services such as authentication and encryption.

Efficient VPN supports only the ESP protocol.
AH
AH is used to authenticate, but not encrypt, IP traffic. An AH header is appended to the standard IP header in each data packet, as described in Encapsulation Modes. AH provides data origin authentication and data integrity check that is performed on an entire IP packet. The sender performs hash calculation on data packets and the authentication key. Upon receipt of data packets carrying the calculation result, the receiver also performs hash calculation and compares the calculation result with that received from the sender. Any changes to the data during transmission will invalidate the calculation result.
ESP
ESP provides encryption and optional authentication. An ESP header is appended to the standard IP header in each data packet, and an ESP trailer and ESP Authentication Data are appended to each data packet, as described in Encapsulation Modes. ESP encrypts the IP payload and then encapsulates it into a data packet to ensure data confidentiality. ESP protects the IP header only in tunnel mode.
Table 1 compares AH and ESP.
Security Feature |
AH |
ESP |
|---|---|---|
Protocol number |
51 |
50 |
Data integrity check |
Supported (checking the entire IP packet) |
Supported (not checking the IP header in transport mode; checking the entire IP packet in tunnel mode) |
Data origin authentication |
Supported |
Supported |
Data encryption |
Not supported |
Supported |
Anti-replay |
Supported |
Supported |
IPSec NAT traversal (NAT-T) |
Not supported |
Supported |
AH and ESP can be used together when high security is required.
AH Header and ESP Header
AH header
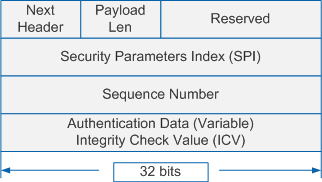
Figure 1 shows the format of an AH header, and Table 2 describes fields in the AH header.
Field |
Length |
Description |
|---|---|---|
Next Header |
8 bits |
This field identifies the type of the payload following the AH header. In transport mode, the Next Header field is the number of the protected upper-layer protocol (TCP or UDP) or ESP. In tunnel mode, the Next Header field is the number of the IP or ESP protocol. NOTE:
When AH and ESP are used together, the Next Header following an AH header is an ESP header. |
Payload Len |
8 bits |
This field specifies the length of the AH header in 32-bit words (4-byte units) minus 2. The default value is 4. |
Reserved |
16 bits |
This field is reserved for future use and defaults to 0. |
SPI |
32 bits |
This field uniquely identifies an IPSec SA. |
Sequence Number |
32 bits |
This field is a counter that monotonically increments from 1. It uniquely identifies a packet to prevent replay attacks. |
Authentication Data |
Integral multiple of 32 bits. It is 96 bits in common cases. |
This field contains the result of Integrity Check Value (ICV) calculation, which is used by the receiver for data integrity check. Authentication algorithms include MD5, SHA1, and SHA2. NOTE:
The MD5 and SHA1 authentication algorithms have security risks. The SHA2 algorithm is recommended. |
ESP header
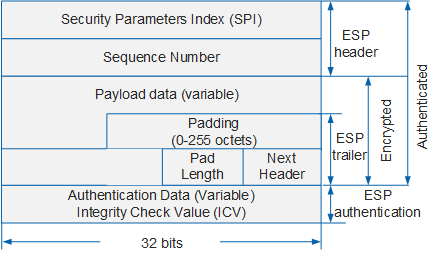
Figure 2 shows the format of an ESP header, and Table 3 describes fields in the ESP header.
Field |
Length |
Description |
|---|---|---|
SPI |
32 bits |
This field uniquely identifies an IPSec SA. |
Sequence Number |
32 bits |
This field is a counter that monotonically increments from 1. It uniquely identifies a packet to prevent replay attacks. |
Payload data |
- |
This field contains the protected variable-length data content in the original IP packet. The type of content protected by ESP is identified by the Next Header field. |
Padding |
- |
This field extends the payload data to a size that fits the encryption's cipher block size. The Padding field length depends on the payload data length and algorithm. |
Pad Length |
8 bits |
This field specifies the length of the Padding field. The value 0 indicates no padding. |
Next Header |
8 bits |
This field identifies the type of the payload following the ESP header. In transport mode, the Next Header field is the number of the protected upper-layer protocol (TCP or UDP). In tunnel mode, the Next Header field is the number of the IP protocol. |
Authentication Data |
Integral multiple of 32 bits. It is 96 bits in common cases. |
This field contains the result of ICV calculation, which is used by the receiver for data integrity check. Authentication algorithms are the same as those of AH. The authentication function of ESP is optional. If data check is enabled, an ICV value is appended to encrypted data. |