Security Association
A Security Association (SA) is an agreement between two peers on certain elements. It describes how to use security services (such as encryption) between peers for secure communication. The elements include the security protocol, characteristics of data flows to be protected, encapsulation mode of data transmitted between peers, encryption and authentication algorithms, and lifetimes of keys (used for secure data conversion and transmission) and SAs.
IPSec SAs need to be established for secure data transmission between IPSec peers. An IPSec SA is identified by three parameters: security parameter index (SPI), destination IP address, and security protocol number (AH or ESP). The SPI is a 32-bit value generated to uniquely identify an SA, and is encapsulated in an AH or ESP header.
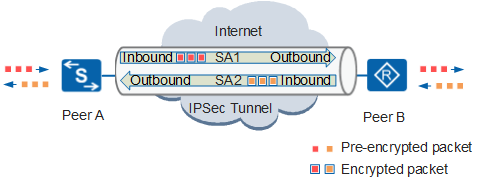
IPSec SAs are unidirectional and are generally established in pairs (inbound and outbound). Therefore, at least one pair of IPSec SAs are established between two IPSec peers to form a secure IPSec tunnel that protects data flows in both directions, as shown in Figure 1.
In addition, the number of IPSec SAs required also depends on the security protocols used to protect traffic between two peers. If either AH or ESP is used, two SAs are required to protect incoming and outgoing traffic. If both AH and ESP are used, four SAs are required, two for each protocol.
IPSec SAs can be established manually or through the Internet Key Exchange (IKE) protocol. Table 1 compares the two IPSec SAs establishment modes.
| Item | Manually Establishing IPSec SAs | Automatically Establishing IPSec SAs Through IKE |
|---|---|---|
| Configuration and update of keys used for encryption and authentication | Manually configured and updated; prone to errors High key management cost |
Generated by the Diffie-Hellman (DH) algorithm and dynamically updated Low key management cost |
| SPI value | Manually configured | Randomly generated |
| Lifetime of an IPSec SA | Valid permanently | Negotiated by two peers (SAs are dynamically updated.) |
| Security | Low | High |
| Applicable scenario | Small-sized networks | Large-, medium-, and small-sized networks |