Basic Concepts of Keychains
A keychain is a set of encryption rules, called keys. A key includes an algorithm, a key string, and the send/receive time. The algorithm and key string are used to encrypt and decrypt packets. The send and receive time indicate that during the period, packets are sent and received using the algorithm and key string.
key
A key includes an algorithm, a key string, and the send/receive time. The keychain support algorithms such as MD5, SHA-1, SHA-256, HMAC-MD5, HMAC-SHA1-12, HMAC-SHA1-20, and SM3. An application must support the algorithm configured in the keychain if the keychain is applied to the application. The key string is a string configured by users.
The active time includes the active send time and the active receive time. The device dynamically changes keys by setting the send and receive time. Keys are classified into the following types:
Active send key: When the system time is within the send time range, the key is the active send key. When the application sends a packet, the algorithm and key configured by the key generate a Message Authentication Code (MAC) on the sending end.
Active receive key: When the system time is within the receive time range, the key is the active receive key. When the application receives a packet, the algorithm and key configured by the key generate a MAC on the receiving end.
Message Authentication Code
A MAC is a character string. The MAC is calculated from data packets and key string using the algorithm.
Keychain Time Mode
Keychain time has an absolute time mode and a periodic time mode.
Absolute time mode uses the Coordinated Universal Time (UTC) format.
- Daily: The key in a keychain takes effect at a specified time each day.
- Weekly: The key in a keychain takes effect on a specified day or days each week.
- Monthly: The key in a keychain takes effect on a specified day or days each month.
- Yearly: The key in a keychain takes effect in a specified month or months each year.
Default Send Key
If no key is configured in a period, no send key is active in that period. Therefore, applications do not send authentication packets to each other. A default send key can be configured to prevent this situation. When no other send keys are active, the default send key takes effect.
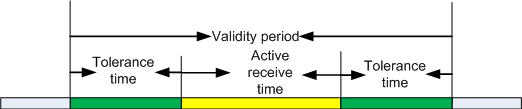
Receive Tolerance Time
When the send key on the device changes, the receive key on the receiving end must be changed. A delay may occur when keys change due to time asynchronization. Packets may be lost during this period. To prevent this situation, a smooth transit is needed in the receive key change. The smooth transit time is called the receive tolerance time.
The receive tolerance time only takes effect on the receive key and can be configured on each keychain. As shown in Figure 1, when the receive tolerance time is configured, the start receive time is advanced and the end receive time is delayed.
TCP kind-value and TCP algorithm-id
TCP applications are connected using TCP authentication. TCP uses enhanced TCP authentication options to send TCP authentication packets.
Vendors use different kind-values to represent the enhanced TCP authentication option. To enable devices of different vendors to communicate with each other, the kind-value can be configured based on the TCP type of the peer device.
There is an algorithm-id field in the enhanced TCP authentication option, indicating the type of the algorithm. The algorithm-id is not defined by the Internet Assigned Numbers Authority (IANA), so different vendors use different algorithm-id to represent algorithms. The mapping between the algorithm-id and the algorithm can be configured to enable devices of different vendors to communicate with each other.