Implementation of Keychains for a Non-TCP Application
The keychain provides authentication for application-layer protocols. A keychain only takes effect after it is applied to applications. Based on processing procedures, the keychain can be applied to non-TCP applications and TCP applications.
A Non-TCP Application Sends Packets Using the Keychain
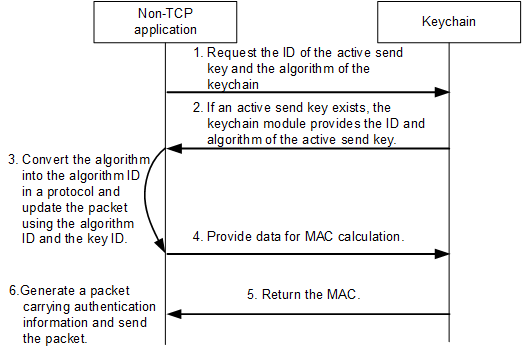
The application requests the ID of the active send key and the algorithm of the keychain.
If an active send key exists, the keychain module provides the ID and algorithm of the active send key. If no active send key exists, the application sends the packet without encryption.
After receiving the ID and algorithm of the active send key, the application converts the algorithm into the algorithm ID in a protocol and encapsulates the algorithm ID and the key ID in the packet.
The application provides data for MAC calculation.
The keychain module calculates the MAC using the algorithm and key defined by the active send key and returns the MAC to the application.
The application generates a packet carrying authentication information and sends the packet.
A Non-TCP Application Receives Packets Using the Keychain
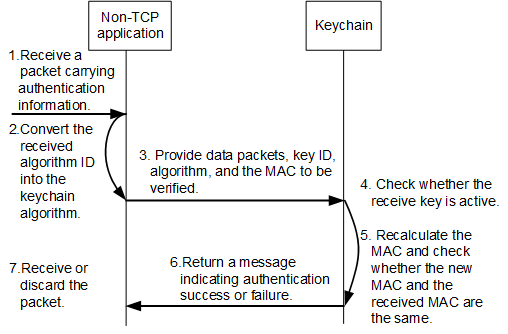
The receiving end receives a packet carrying authentication information.
The application on the receiving end converts the received algorithm ID into the keychain algorithm.
The application on the receiving end provides data packets, key ID, algorithm, and the MAC to be verified.
The keychain module checks whether the receive key having the same key ID with the received packet is active. If the receive key is not active, the keychain sends a Reject packet.
If the receive key is active, the keychain module uses the algorithm and key string configured on the key to recalculate the MAC and checks whether the new MAC and the received MAC are the same.
A message indicating authentication success or failure is returned.
The application receives or discards the packets based on the authentication result.