Implementation of Keychains for TCP Applications
TCP Applications Send Packets Using the Keychain
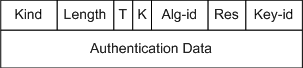
In the Bonica draft, TCP uses enhanced TCP authentication options to send TCP authentication packets. Figure 1 shows the format of the enhanced authentication option packet:
The donica draft has not been standardized, and IANA has not defined the kind value and algorithm ID. Vendors use different kind values and algorithm IDs. To enable devices of different vendors to communication with each other, you can configure the TCP kind value and the mapping between the TCP algorithm and algorithm ID.
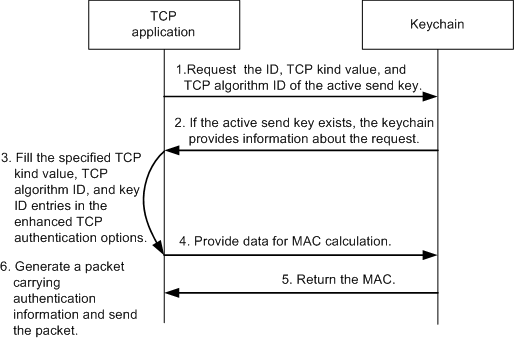
The application requests the ID, TCP kind value, and TCP algorithm ID of the active send key.
If the active send key exists, the keychain provides information about the request.
The application fills the specified TCP kind value, TCP algorithm ID, and key ID entries in the enhanced TCP authentication options.
The application provides data for MAC calculation.
The keychain module calculates the MAC based on the algorithm and key string configured for the active send key and returns the MAC.
The application fills the MAC entry in the enhanced TCP authentication options and sends the packet.
A TCP Application Receives Packets Using the Keychain
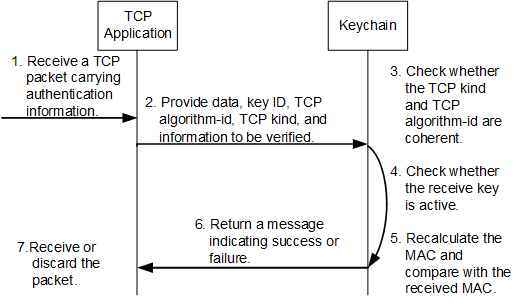
The receiving end receives a TCP packet carrying authentication information.
The receiving end provides data packets, key ID, TCP algorithm ID, TCP kind value, and the MAC to be verified for the keychain.
The keychain checks whether the TCP type value and algorithm ID in the received packet is the same as those in the local end. If not, the keychain sends a Reject packet.
The keychain module checks whether the receive key having the same key ID with the received packet is active. If the receive key is not active, the keychain sends a Reject packet.
If the receive key is active, the keychain module uses the algorithm and key string configured on the key to recalculate the MAC and checks whether the new MAC and the received MAC are the same.
A message indicating authentication success or failure is returned.
The application receives or discards the packets based on the authentication result.