802.1X Authentication
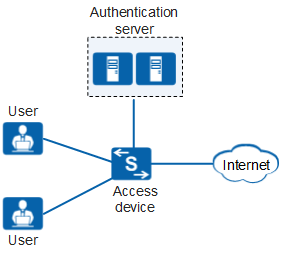
As shown in Figure 1, users' network access needs to be controlled to ensure network security. Only authenticated users are allowed to access network resources authorized by the administrator.
The user terminal is a PC with 802.1X client software installed
on it. The user can use the 802.1X client software to initiate an
authentication request to the access device. After exchanging information
with the user terminal, the access device sends the user information
to the authentication server for authentication. If the authentication
succeeds, the access device sets the interface connected to the user
to the Up state and allows the user to access the network. If the
authentication fails, the access device rejects the user's access
request.

802.1X authentication results in the change of the interface state, but does not involve IP address negotiation or assignment. 802.1X authentication is the simplest authentication solution. However, the 802.1X client software must be installed on the user terminal.