PKI Working Mechanism
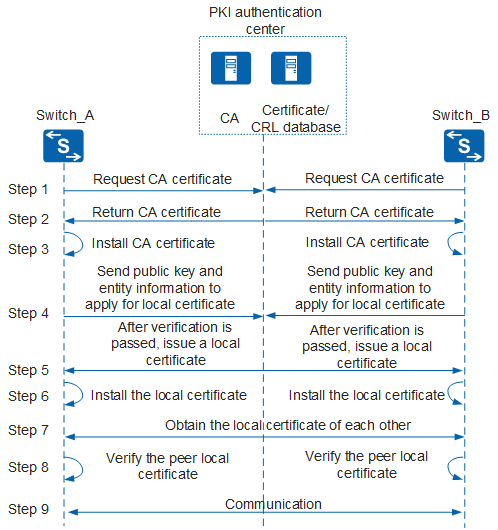
On a PKI network, a PKI entity applies for a local certificate from the CA and the applicant device authenticates the certificate. Figure 1 shows the PKI working process.
A PKI entity applies for a CA certificate (CA server's certificate) from the CA.
When receiving the application request, the CA sends its own certificate to the PKI entity.
The PKI entity installs the CA certificate.
If the PKI entity uses SCEP for certificate application, it computes a digital fingerprint by using the hash algorithm on the received CA certificate, and compares the computed fingerprint with that pre-defined for the CA server. If the fingerprints are the same, the PKI accepts the CA certificate; otherwise, it discards the CA certificate.
The PKI entity sends a certificate enrollment message (including the public key carried in the configured key pair and PKI entity information) to the CA.
If the PKI entity uses SCEP for certificate application, it encrypts the enrollment message using the CA certificate's public key and signs the message using its own private key. If the CA server requires a challenge password, the enrollment message must contain a challenge password, which must be the same as the CA's challenge password.
If the PKI entity uses CMPv2 to apply for a local certificate, it uses an external identity certificate (local certificate issued by another CA) or MAC to authenticate the certificate.External identity certificate
The PKI entity uses the CA certificate's public key to encrypt the enrollment message and the external identity certificate's private key for digital signature.
MAC
The PKI entity uses the CA certificate's public key to encrypt the enrollment message and the message must contain the MAC reference value and secret value (the values must be the same as those of the CA).
The CA receives the enrollment message from the PKI entity.
If the PKI entity uses SCEP to apply for a local certificate, the CA uses its own private key to decrypt the enrollment message and the PKI entity's public key to decrypt the digital signature, and verifies the digital fingerprint. When the fingerprints are the same, the CA verifies the PKI entity's identity information. When the PKI entity's identity information passes verification, the CA accepts the application and issues a local certificate to the PKI entity. The CA uses the PKI entity's public key to encrypt the certificate and its own private key to digitally sign the certificate, and sends the certificate to the PKI entity. At the same time, the CA also sends the certificate to the certificate/CRL database.
If the PKI entity uses CMPv2 to apply for a local certificate, the CA can use two modes:External identity certificate
The CA uses its own private key to decrypt the enrollment message and external identity certificate's public key to decrypt the digital signature, and verifies the digital fingerprint. When the fingerprints are the same, the CA verifies the PKI entity's identity information. When the PKI entity's identity information passes verification, the CA accepts the application and issues a local certificate to the PKI entity. The CA uses the public key in the PKI entity's external identity certificate to encrypt the certificate and its own private key to digitally sign the certificate, and sends the certificate to the PKI entity. At the same time, the CA also sends the certificate to the certificate/CRL database.
MAC
The CA uses its own private key to decrypt the enrollment message and verifies the MAC reference value and secret value. When the reference value and secret value are the same as those on the CA server, the CA verifies the PKI entity's identity information. When the PKI entity's identity information passes verification, the CA accepts the application and issues a local certificate to the PKI entity. The CA then uses the PKI entity's public key to encrypt the certificate, and issues the certificate to the PKI entity. At the same time, the CA also sends the certificate to the certificate/CRL database.
The PKI entity receives the certificate from CA.
If the PKI entity has applied for a local certificate using SCEP, the PKI entity uses its own private key to decrypt the certificate and the CA's public key to decrypt the digital signature, and verifies the digital fingerprint. If the digital fingerprint is the same as its local one, the PKI entity accepts and installs the local certificate.
If the PKI entity has applied for a local certificate using CMPv2:External identity certificate
The PKI entity uses the external identity certificate's private key to decrypt the certificate and the CA's public key to decrypt the digital signature, and verifies the digital fingerprint. If the digital fingerprint is the same as its local one, the PKI entity accepts and installs the local certificate.
MAC
The PKI entity uses its own private key to decrypt the certificate and verifies the MAC reference value and secret value. If the reference value and secret value are the same as the local ones, the PKI entity accepts and installs the local certificate.
The PKI entities in a communication session need to obtain and install each other's local certificates. The PKI entities can download the peer's local certificates through HTTP. In special scenarios, such as IPSec application, the PKI entities actively send their local certificates to the peer.
After the peer's local certificate is installed on the local end, the local end uses CRL or OCSP to check whether the peer certificate is valid.
The PKI entities use the public keys in peer certificates for secure communication only after they confirm that the peer certificates are valid.
If an RA is available in a PKI system, the PKI entities also need to download the RA's certificate. The RA verifies the local certificate enrollment messages from PKI entities, and forwards the messages to the CA after verifications are passed.