WAPI
WLAN Authentication and Privacy Infrastructure (WAPI) is a Chinese national standard for WLANs, which was developed based on IEEE 802.11. WAPI provides higher security than both WEP and WPA and consists of the following:
- WLAN Authentication Infrastructure (WAI): authenticates user identities and manages keys.
- WLAN Privacy Infrastructure (WPI): protects data transmitted on WLANs and provides the encryption, data verification, and anti-replay functions.
WAPI uses the elliptic curve cryptography (ECC) algorithm, which is based on public key cryptography and the block key algorithm based on symmetric-key cryptography. The ECC algorithm is used for digital certificate authentication and key negotiation between wireless devices. The block key algorithm is used to encrypt and decrypt data transmitted between wireless devices. The two algorithms implement identity authentication, link authentication, access control, and user information encryption.
Bidirectional identity authentication
Bidirectional identity authentication prevents access from unauthorized STAs and protects a WLAN against attacks from unauthorized WLAN devices.
Digital certificate as identity information
A WAPI system has an independent certificate server. STAs and WLAN devices use digital certificates to prove their identities, improving network security. When a STA requests to join or leave a network, the administrator only needs to issue a certificate to the STA or revoke the certificate of the STA.
Well-developed authentication protocol
WAPI uses digital certificates to identify STAs and wireless devices. During identity authentication, the elliptic curve digital signature algorithm is used to verify a digital certificate. In addition, the secure message hash algorithm is used to ensure message integrity, which prevents attackers from tampering or forging information transmitted during identity authentication.
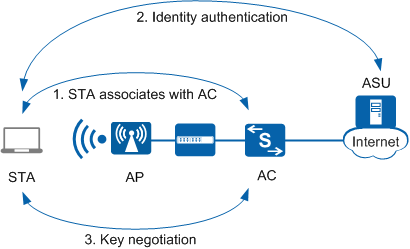
WAPI involves identity authentication and key negotiation, which begin after a STA associates with an AC, as shown in Figure 1.
Identity Authentication
WAPI provides two identity authentication modes: certificate-based mode (WAPI-CERT) and pre-shared key-based mode (WAPI-PSK).
WAPI-CERT: A STA and an AC authenticate each other's certificate. The certificates must be loaded on the STA and AC and verified by an authentication service unit (ASU). After certificate authentication is complete, the STA and AC use the temporal public key and private key to generate a base key (BK) for key negotiation.
The WAPI-CERT mode is applicable to large-scale enterprise networks or carrier networks that can deploy and maintain an expensive certificate system.
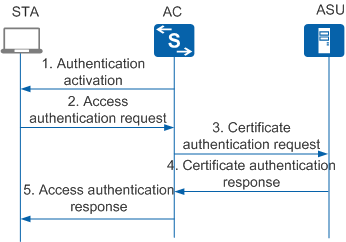
Figure 2 shows the WAPI certificate authentication process.
The WAPI certificate authentication process is as follows:
Authentication activation
When a STA requests to associate or re-associate with an AC, the AC checks whether the user is a WAPI user. If the user is a WAPI user, the AC sends an authentication activation packet to trigger the certificate authentication process.
Access authentication request
The STA sends an access authentication request carrying the STA's certificate and the system time to the AC. The system time is the access authentication request time.
Certificate authentication request
When the AC receives the access authentication request, it records the access authentication request time and sends a certificate authentication request to the ASU. The certificate authentication request carries the STA's certificate, access authentication request time, the AC's certificate, and a signature generated using the AC's private key and the preceding information.
Certificate authentication response
When the ASU receives the certificate authentication request, it authenticates the AC's signature and certificate. If the AC's signature and certificate are invalid, the authentication fails. If they are valid, the ASU authenticates the STA's certificate.
After the authentication is complete, the ASU constructs a certificate authentication response with the STA's certificate authentication result, AC's certificate authentication result, and a signature generated using the authentication results, and sends the certificate authentication response to the AC.
Access authentication response
When the AC receives the certificate authentication response, it checks the signature to obtain the STA's certificate authentication result, and controls access of the STA based on the certificate authentication result. The AC then forwards the certificate authentication response to the STA. The STA checks the signature generated by the ASU to obtain the AC's certificate authentication result, and determines whether to associate with the AC based on the result.
If the certificate authentication succeeds, the AC accepts the access request. If the certificate authentication fails, the AC disassociates the STA from the network.
WAPI-PSK: The STA and AC have the same PSK configured before authentication. The PSK is converted into a BK during authentication.
The WAPI-PSK mode does not require an expensive certificate system, so it is applicable to individual users or small-scale enterprise networks.
Key Negotiation
After the AC is authenticated by the ASU, the AC initiates key negotiation with the STA. Key negotiation consists of two stages: unicast key negotiation and multicast key negotiation.
Unicast key negotiation
The STA and AC obtain a unicast encryption key and unicast integrity key through unicast key negotiation and use these keys to ensure the security of unicast data exchanged between them.
During unicast key negotiation, the STA and AC use the KD-HMAC-SHA256 algorithm to calculate a unicast session key (USK) based on the BK. In addition to the USK, the STA and AC also negotiate the encryption key and identity key used to generate the multicast key.
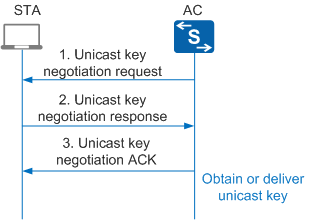
Figure 3 shows the unicast key negotiation process.
The unicast key negotiation process is as follows:
Unicast key negotiation request
After a BK is generated, the AC sends a unicast key negotiation request packet to the STA.
Unicast key negotiation response
After the STA receives the unicast key negotiation request packet, it performs the following steps:
- Checks whether this negotiation process is triggered to update the unicast key.
- If so, the STA proceeds to step b.
- If not, the STA proceeds to step c.

WAPI allows the STA to directly send a unicast key negotiation response to the AC to initiate a unicast key update.
- Checks whether the challenge of the AC is the same as the challenge that is obtained in last unicast key negotiation and saved locally. If the two challenges are different, the STA drops the unicast key negotiation request packet.
- Generates a random challenge, and then uses the KD-HMAC-SHA256 algorithm to calculate a USK and the AC's challenge used for the next unicast key negotiation based on the BK, the AC's challenge, and the STA's challenge.
- Uses the message authentication key and HMAC-SHA256 algorithm to calculate a message authentication code, and sends it to the AC with a unicast key negotiation response packet.
- Checks whether this negotiation process is triggered to update the unicast key.
Unicast key negotiation ACK
After the AC receives the unicast key negotiation response packet, it performs the following steps:
- Checks whether the AC's challenge is correct. If the AC's challenge is incorrect, the AC drops the unicast key negotiation response packet.
- Uses the KD-HMAC-SHA256 algorithm to calculate a USK and the AC's challenge used for the next unicast key negotiation based on the BK, AC's challenge, STA's challenge. The AC then calculates the local message authentication code using the message authentication key and HMAC-SHA256 algorithm, and compares the local message authentication code with that in the received unicast key negotiation response packet. If the two message authentication codes are different, the AC drops the unicast key negotiation response packet.
- Checks the WAPI information element in the response packet if this is the first unicast key negotiation after the BK is generated. If the network type is BSS, the AC checks whether the WAPI information element in the response packet is the same as that in the association request packet it received before. If they are different, the AC sends a Deauthentication frame to disassociate the STA. If the network type is IBSS (ad-hoc network), the AC checks whether the unicast key algorithm supports the information element in the response packet. If not, the AC sends a Deauthentication frame to disassociate the STA.
- Uses the message authentication key and HMAC-SHA256 algorithm to calculate a message authentication code, and sends it to the STA with a unicast key negotiation ACK packet.
Multicast key negotiation
Multicast key negotiation is performed after unicast key negotiation is complete. The AC advertises the multicast keys to the STA in this process.
The AC uses the multicast encryption key and multicast integrity key derived from the multicast master key (MMK) to encrypt broadcast or multicast data it sends, and sends a multicast key advertisement packet to the STA. The STA obtains the multicast encryption key and multicast integrity key from the multicast key advertisement packet to decrypt the broadcast or multicast data it receives.
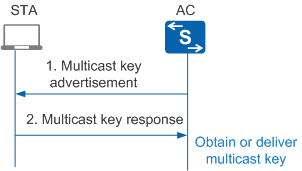
Figure 4 shows the multicast key negotiation process.
The multicast key negotiation process is as follows:
Multicast key advertisement
The AC uses the random number algorithm to calculate an MMK, encrypts the MMK using the negotiated unicast key, and sends an advertisement packet to notify the STA of the MMK.
Multicast key response
After the STA receives the multicast key advertisement packet, it performs the following steps:
- Calculates the checksum using the message authentication key identified by the unicast key identifier, and compares the checksum with the message authentication code. If the checksum is different from the message authentication code, the STA drops the multicast key advertisement packet.
- Checks whether the key advertisement identifier is increasing. If not, the STA drops the multicast key advertisement packet.
- Decrypts the multicast key to obtain the 16-byte master key and uses the KD-HMAC-SHA256 algorithm to extend it to 32 bytes. The first 16 bytes indicate the encryption key, and the last 16 bytes indicate the integrity key.
- Saves the key advertisement identifier and sends a multicast key response packet to the AC.
- After the AC receives the multicast key response packet, it performs the following steps:
- Calculates the checksum using the message authentication key identified by the unicast key identifier, and compares the checksum with the message authentication code. If the checksum is different from the message authentication code, the AC drops the multicast key response packet.
- Compares fields (such as key advertisement identifier) in the multicast key response packet with corresponding fields in the multicast key advertisement packet it has sent. If all the fields are the same, the multicast key negotiation is successful. Otherwise, the AC drops the multicast key response packet.
Key Update
WAPI features a dynamic key negotiation mechanism, but there may still be security risks if a STA uses the same encryption key for a long time. To enhance security, WAPI provides a time-based key update mechanism.
Time-based key update: The unicast and multicast keys of a STA have an aging time (configured using a command). When the aging time of the current unicast or multicast key expires, the STA and AC negotiate a new unicast or multicast key.