WPA/WPA2
WEP shared key authentication uses the RC4 symmetric stream cipher to encrypt data. This authentication method requires the same static key pre-configured on the server and client. Both the encryption mechanism and encryption algorithm can bring security risks to the network.
The Wi-Fi Alliance developed Wi-Fi Protected Access (WPA) to overcome the shortcomings of WEP before more secure policies were provided in 802.11i. WPA still uses the RC4 algorithm, but it uses an 802.1X authentication framework and supports Extensible Authentication Protocol-Protected Extensible Authentication Protocol (EAP-PEAP) and EAP-Transport Layer Security (EAP-TLS) authentication, and defines the Temporal Key Integrity Protocol (TKIP) encryption algorithm.
Later, 802.11i defined WPA2. WPA2 uses Counter Mode with CBC-MAC Protocol (CCMP), a more secure encryption algorithm than those used in WPA.
Both WPA and WPA2 support 802.1X authentication and the TKIP/CCMP encryption algorithms, ensuring better compatibility. The difference lies in the protocol packet format.
- Link authentication
- Access authentication
- Key negotiation
- Data encryption
Link Authentication
Link authentication can be completed in open system authentication or shared key authentication mode. WPA and WPA2 support only open system authentication. For details, see "Link Authentication" in STA Access.
Access Authentication
The WPA/WPA2 enterprise edition (WPA/WPA2-802.1X authentication) uses a RADIUS server and the EAP protocol for authentication. Users provide authentication information, including the user name and password, and are authenticated by an authentication server (generally a RADIUS server).
Large-scale enterprise networks usually use the WPA/WPA2 enterprise edition.

For details about 802.1X authentication, see Principles of 802.1X Authentication in the Configuration Guide - User Access and Authentication Configuration Guide.
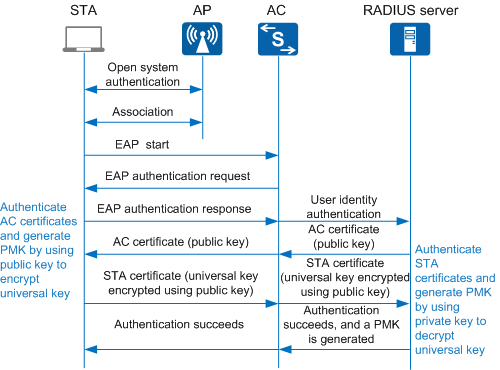
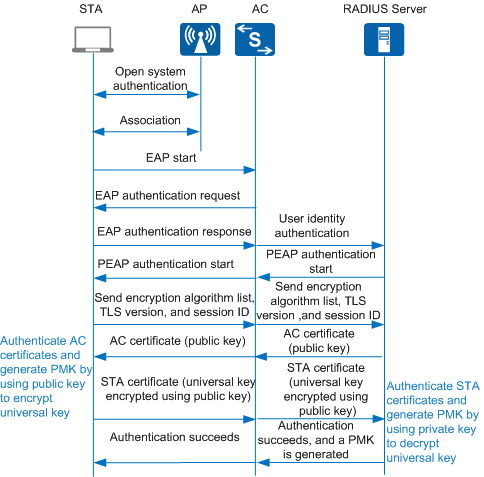
WPA/WPA2 implements 802.1X authentication using EAP-TLS and EAP-PEAP. Figure 1 and Figure 2 show the EAP-TLS 802.1X authentication and EAP-PEAP 802.1X authentication processes.
WPA/WPA2 personal edition:
A dedicated authentication server is expensive and difficult to maintain for small- and medium-scale enterprises and individual users. The WPA/WPA2 personal edition provides a simplified authentication mode: pre-shared key authentication (WPA/WPA2-PSK). This mode does not require a dedicated authentication server. Users only need to set a pre-shared key (PSK) on each WLAN node (including WLAN server, wireless router, and wireless network adapter).
A WLAN client can access the WLAN if its pre-shared key is the same as that configured on the WLAN server. The PSK is not used for encryption; therefore, it does not pose security risks like the 802.11 shared key authentication.
802.1X authentication can be used to authenticate wireless and wired users, whereas PSK authentication is specific to wireless users.
PSK authentication requires that a STA and an AC be configured with the same PSK. The STA and AC authenticate each other through key negotiation. During key negotiation, the STA and AC use their PSKs to decrypt the message sent from each other. If the messages are successfully decrypted, the STA and AC have the same PSK. If they use the same PSK, PSK authentication is successful; otherwise, PSK authentication fails.
Key Negotiation
802.11i defines two key hierarchies: pairwise key hierarchy and group key hierarchy. The pairwise key hierarchy protects unicast data exchanged between STAs and APs. The group key hierarchy protects broadcast or multicast data exchanged between STAs and APs.
During key negotiation, a STA and an AC use the pairwise master key (PMK) to generate a pairwise transient key (PTK) and a group temporal key (GTK). The PTK is used to encrypt unicast packets, and the GTK is used to encrypt multicast and broadcast packets.
In 802.1X authentication, a PMK is generated in the process shown in Figure 1.
- In PSK authentication, the method to generate a PMK varies according to the form of the PSK, which is configured using a command:
- If the PSK is a hexadecimal numeral string, it is used as the PMK.
- If the PSK is a character string, the PMK is calculated using a hash algorithm based on the PSK and service set identifier (SSID).
Key negotiation consists of unicast key negotiation and multicast key negotiation.
Unicast key negotiation
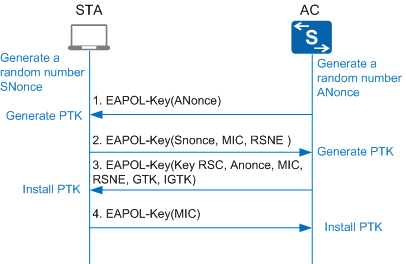
Key negotiation is completed through a four-way handshake between a STA and an AC, during which the STA and AC send EAPOL-Key frames to exchange information, as shown in Figure 3.The unicast key negotiation process consists of the following steps:
- The AC sends an EAPOL-Key frame with a random value (ANonce) to the STA.
- The STA calculates the PTK using its own MAC addresses and the MAC address of the AC, the PMK, ANonce, and SNonce, and sends an EAPOL-Key frame to the AC. The EAPOL-Key frame carries the SNonce, robust security network (RSN) information element, and message integrity code (MIC) of the EAPOL-Key frame. The AC calculates the PTK using the MAC addresses of its own and the STA, PMK, ANonce, and SNonce, and validates the MIC to determine whether STA's PMK is the same as its own PMK.
- The AC sends an EAPOL-Key frame to the STA to request the STA to install the PTK. The EAPOL-Key frame carries the ANonce, RSN information element, MIC, and encrypted GTK.
- The STA sends an EAPOL-Key frame to the AC to notify the AC that the PTK has been installed and will be used. The AC installs the PTK after receiving the EAPOL-Key frame.
Multicast key negotiation
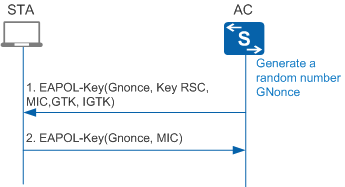
Multicast key negotiation is completed through a two-way handshake. The two-way handshake begins after the STA and AC generate and install a PTK through a four-way handshake. Figure 4 shows the two-way handshake process.The multicast key negotiation process consists of the following steps:
- The AC calculates the GTK, uses the unicast key to encrypt the GTK, and sends an EAPOL-Key frame to the STA.
- After the STA receives the EAPOL-Key frame, it validates the MIC, decrypts the GTK, installs the GTK, and sends an EAPOL-Key ACK frame to the AC. After the AC receives the EAPOL-Key ACK frame, it validates the MIC and installs the GTK.
Data Encryption
WPA and WPA2 support the TKIP and CCMP encryption algorithms.
TKIP
Unlike WEP, which uses a static shared key, TKIP uses a dynamic key negotiation and management mechanism. Each user obtains an independent key through dynamic negotiation. User keys are calculated using the PTK generated in key negotiation, the MAC address of the sender, and the packet sequence number.
TKIP uses MICs to ensure the integrity of frames received on the receiver and validity of data sent by the sender and receiver. This mechanism protects information integrity. A MIC is calculated using the MIC key generated during key negotiation, the destination MAC address, source MAC address, and data frame.
CCMP
While WEP and TKIP use a stream cipher algorithm, CCMP uses an Advanced Encryption Standard (AES) block cipher. The block cipher algorithm overcomes defects of the RC4 algorithm and provides a higher level of security.