Rogue Device Detection and Containment
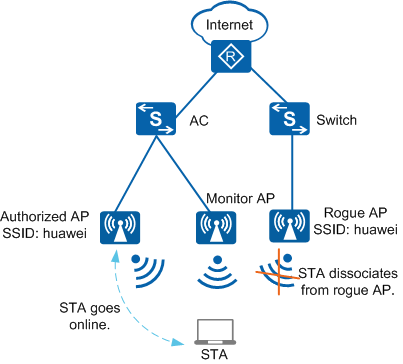
In Figure 1, an employee connects to a rogue fat AP from the campus network or uses simulation software to simulate a fat AP and deceive users into connecting to the corresponding SSID. After WIDS and WIPS are configured, the AC identifies the rogue AP. The monitor AP then uses the rogue AP's identity information to broadcast a Deauthentication frame. After STAs associating with the rogue AP receive the Deauthentication frame, they disassociate from the rogue AP. This countermeasure prevents STAs from associating with the rogue AP.