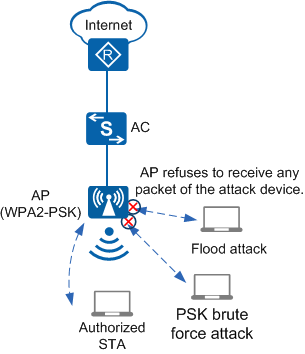
Attack Device Detection
In Figure 1, the campus wireless network uses the WPA2-PSK authentication mode. Attackers use terminals to initiate flood attacks to the wireless network and attempts to use the brute force method to decrypt the password. After detecting the attack device, the AC adds the attack device to the dynamic blacklist and does not process any packet of the device to prevent attacks.