Routing Policy Fundamentals
Filters
A filter is the core of a routing policy and is used to define a set of matching rules. The switch provides the filters listed in Table 1.
Filter |
Applicable Scope |
Matching Rules |
|---|---|---|
Dynamic routing protocols |
Inbound interface, source or destination IP address, protocol type, and source or destination port number |
|
Dynamic routing protocols |
Source and destination IP addresses and next hop address |
|
BGP |
AS_Path attribute |
|
BGP |
Community attribute |
|
VPN |
Extended community attribute |
|
VPN |
RD attribute |
|
Dynamic routing protocols |
Destination IP address, next-hop address, cost, interface information, route type, ACL, IP prefix list, AS_Path filter, community filter, extcommunity filter, and RD filter |
The ACL, IP prefix list, AS_Path filter, community filter, extcommunity filter, and RD filter can be used only to filter routes but not modify attributes of filtered routes. A route-policy is a comprehensive filter, and it can use the matching rules of the ACL, IP prefix list, AS_Path filter, community filter, extcommunity filter, and RD filter to filter routes. In addition, attributes of filtered routes can be modified using the route-policy. The following describes these filters.
ACL
An ACL is a set of sequential filtering rules. Users can define rules based on packet information, such as inbound interfaces, source or destination IP addresses, protocol types, and source or destination port numbers, and specify an action to deny or permit packets. After an ACL is configured, the system classifies received packets based on the rules defined in the ACL and denies or permits the packets accordingly.
An ACL only classifies packets based on defined rules and can be used to filter packets only when it is applied to a routing policy.
ACLs can be configured for both IPv4 packets and IPv6 packets. Users can specify the IP address and subnet address range in an ACL to match the source IP address, destination network segment address, or next-hop address of a route.
IP Prefix List
An IP prefix list contains a group of route filtering rules. Users can specify the prefix and mask length range to match the destination network segment address or next-hop address of a route. An IP prefix list is used to filter routes that are advertised and received by dynamic routing protocols.
An IP prefix list is easier to configure and more flexible than an ACL. However, if a large number of routes with different prefixes need to be filtered, it is complex to configure an IP prefix list to filter these routes.
- Mask length: An IP prefix list filters routes based on IP address prefixes. An IP address prefix is defined by an IP address and a mask length. For example, for the route to 10.1.1.1/16, the mask length is 16 bits, and the valid prefix is 16 bits (10.1.0.0).
- Mask length range: If routes have the same IP address prefix but different masks, the prefix mask length range can be specified for exact match or for matching routes within the specified mask length range.

- If a mask is specified, all routes with this mask are permitted or denied.
- If a mask length range is specified, all routes with the mask length in this range are permitted or denied.
AS_Path Filter
An AS_Path filter is used to filter BGP routes based on AS_Path attributes contained in BGP routes. The AS_Path attribute records numbers of all ASs that a BGP route passes through from the local end to the destination in the distance-vector (DV) order. Therefore, filtering rules defined based on AS_Path attributes can be used to filter BGP routes. The matching condition of an AS_Path filter is specified using a regular expression. For example, ^30 indicates that only the AS_Path attribute starting with 30 is matched.
For details about AS_Path filter principles and applications, see AS_Path Filter Applications in BGP.
Community Filter
A community filter is used to filter BGP routes based on Community attributes contained in BGP routes. The Community attribute is a set of destination addresses with the same characteristics. Therefore, filtering rules defined based on Community attributes can be used to filter BGP routes.
In addition to well-known Community attributes, users can define community attributes using digits. The matching condition of a community filter can be specified using a community ID or regular expression.
For details about community filter principles and applications, see Community Attribute Applications in BGP.
Extcommunity Filter
VPN target: A VPN target controls route learning between VPN instances, isolating routes of VPN instances. A VPN target may be either an import or export VPN target. Before advertising a Virtual Private Network version 4 (VPNv4) or Virtual Private Network version 6 (VPNv6) route to a remote Multi-protocol Extensions for Border Gateway Protocol (MP-BGP) peer, a PE adds an export VPN target to the route. After receiving a VPNv4 or VPNv6 route, the remote MP-BGP peer compares the received export VPN target with the local import VPN target to determine which routes can be added to the routing table of the local VPN instance.
Source of Origin (SoO): If multiple CEs at a VPN site are connected to different PEs, the routes advertised from the CEs to the PEs may be re-advertised to this VPN site after the routes have traversed the backbone network. This may cause routing loops within the VPN site. To prevent routing loops, you can configure an SoO attribute to differentiate routes advertised from different VPN sites.
RD Filter
An RD filter is used to filter BGP routes based on RDs in VPN routes. RDs are used to distinguish IPv4 and IPv6 prefixes in the same address segment in VPN instances. RD filters specify matching rules regarding RD attributes.
Route-Policy
A route-policy is a complex filter. It is used to match attributes of specified routes and change route attributes when specific conditions are met. A route-policy can use the preceding six filters to define its matching rules.
Invoking Between Tools in Routing Policy
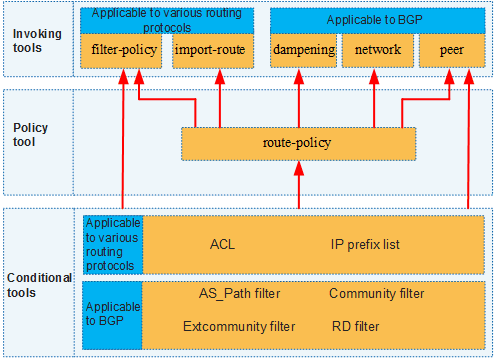
In applications, to control routes, tools used in routing policy must be used together. Figure 1 shows invoking between these tools.
InFigure 1, all the tools used in routing policy are classified into the following types:
- Conditional tool: captures required routes.
- Policy tool: performs an action on the captured routes, for example, permit, deny, and modify attributes.
- Invoking tool: applies a routing policy to a specific routing protocol to make the routing policy to take effect.

Among the invoking tools, filter-policy and peer have the policy tool function, so they can directly invoke conditional tools. Other invoking tools must invoke conditional tools through route-policy.
The invoking tool, peer, can invoke all conditional tools except ACL.