IP Prefix List
Filtering Rules
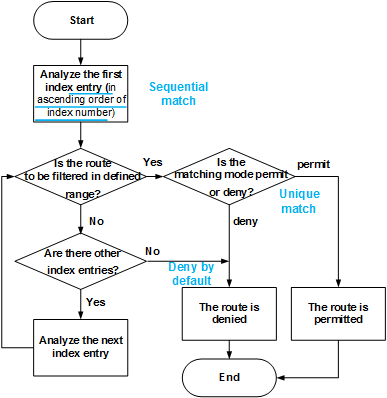
An IP prefix list can contain multiple index entries, each of which corresponds to a filtering rule. In Figure 1, the system matches routes against entries in ascending order of index number.
- If a route matches a permit entry, this route is permitted. If a route matches a deny entry, this route is denied.
- If a route does not match any entry in the IP prefix list, this route is denied.
Route filtering rules of an IP prefix list include: sequential match, unique match, and deny by default.
- Sequential match: Routes are matched against entries in ascending order of index number. If different index numbers are configured for multiple entries in the same IP prefix list, different filtering results may be obtained. Therefore, exercise caution when configuring index numbers.
- Unique match: If a route matches one entry, it no longer tries to match other entries.
- Deny by default: By default, all the routes that do not match any entry are denied. Therefore, after one or multiple deny entries are created in an IP prefix list, one entry needs to be created to permit all the other routes.
Mask Matching
One advantage of IP prefix list over ACL is that routes can be matched against their mask. The following example shows the ip ip-prefix command used to configure an IPv4 prefix list:
ip ip-prefix ip-prefix-name [ index index-number ] { permit | deny } ipv4-address mask-length [ greater-equal greater-equal-value ] [ less-equal less-equal-value ]
In this command, ipv4-address mask-length [ greater-equal greater-equal-value ] [ less-equal less-equal-value ] defines the network ID and mask range of routes to be filtered. Table 1 describes parameters in this command.
Parameter |
Description |
|---|---|
ipv4-address |
Specifies a network ID. |
mask-length |
Specifies the mask length for exact match. |
greater-equal greater-equal-value |
Indicates that the mask length must be greater than or equal to greater-equal-value. |
less-equal less-equal-value |
Indicates that the mask length must be less than or equal to less-equal-value. |
When a route to be filtered has matched a network ID, the mask length can be matched exactly or within a specified mask length.
- If both greater-equal and less-equal are not configured in the command, exact match is performed on routes. That is, only the routes with the specified mask-length are matched.
- If only greater-equal is configured in the command, the mask length range used for matching routes is [greater-equal-value, 32].
- If only less-equal is configured in the command, the mask length range used for matching routes is [mask-length, less-equal-value].
- If both greater-equal and less-equal are configured in the command, the mask length range used for matching routes is [greater-equal-value, less-equal-value].
Differences Between IP Prefix List and ACL
Both IP prefix list and ACL can be used to filter routes. ACLs can match only the network ID but not the mask (prefix length), but an IP prefix list is more flexible than ACLs because it can match both the network ID and mask, improving route matching accuracy.
The following two examples can help differentiate ACL and IP prefix list.
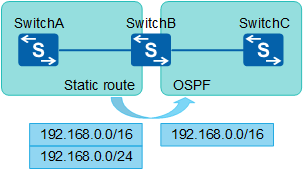
In Figure 2, SwitchB has two static routes, but only the static route 192.168.0.0/16 needs to be imported into OSPF.
Check the IP routing table of SwitchB. The following command output shows that it has two static routes 192.168.0.0/16 and 192.168.0.0/24. Now only the route 192.168.0.0/16 needs to be re-advertised into OSPF.
[SwitchB] display ip routing-table
Route Flags: R - relay, D - download to fib, T - to vpn-instance
-----------------------------------------------------------------------------
Routing Tables: Public Destinations : 6 Routes : 6
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.10.12.0/24 Direct 0 0 D 10.10.12.1 Vlanif10
10.10.12.1/32 Direct 0 0 D 127.0.0.1 Vlanif10
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
192.168.0.0/16 Static 60 0 D 0.0.0.0 NULL0
192.168.0.0/24 Static 60 0 D 0.0.0.0 NULL0
First, use an ACL to meet this requirement.
1. Configure a basic ACL 2001.
[SwitchB] acl 2001 [SwitchB-acl-basic-2001] rule permit source 192.168.0.0 0.0.255.255 [SwitchB-acl-basic-2001] quit
Configure node 10 in the route-policy RP to permit the route matching the basic ACL 2001 and deny all the unmatched routes.
[SwitchB] route-policy RP permit node 10 [SwitchB-route-policy] if-match acl 2001 [SwitchB-route-policy] quit
Import the static route permitted by the route-policy RP into OSPF.
[SwitchB] ospf [SwitchB-ospf-1] import-route static route-policy RP [SwitchB-ospf-1] quit
After the preceding configurations are complete, check the IP routing table of SwitchC.
<SwitchC> display ip routing-table
Route Flags: R - relay, D - download to fib, T - to vpn-instance
-----------------------------------------------------------------------------
Routing Tables: Public
Destinations : 6 Routes : 6
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.10.12.0/24 Direct 0 0 D 10.10.12.2 Vlanif10
10.10.12.2/32 Direct 0 0 D 127.0.0.1 Vlanif10
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
192.168.0.0/16 O_ASE 150 1 D 10.10.12.1 Vlanif10
192.168.0.0/24 O_ASE 150 1 D 10.10.12.1 Vlanif10
The command output shows that the two routes to 192.168.0.0 have been imported. This is because in the ACL 2001 rule permit source 192.168.0.0 0.0.255.255, 0.0.255.255 indicates a wildcard but not the mask length.
After a wildcard is converted into a binary number, 0 indicates that routes need to match this ACL, while 1 indicates that routes do not. For example, 192.168.0.0 0.0.255.255 specifies a route prefix range: 192.168.0.0 to 192.168.255.255. The two routes 192.168.0.0/16 and 192.168.0.0/24 both match the ACL 2001. Therefore, the two routes match node 10 in the route-policy RP and both are imported into OSPF. ACLs cannot ensure that only the route 192.168.0.0/16 or 192.168.0.0/24 is matched because ACLs can match only network ID but not mask.
The following uses an IP prefix list to filter the imported routes. Check whether an IP prefix list can ensure that only the route 192.168.0.0/16 is imported and the route 192.168.0.0/24 is filtered out.
Configure an IP prefix list huawei and configure node 10 to permit the route 192.168.0.0/16.
[SwitchB] ip ip-prefix huawei index 10 permit 192.168.0.0 16
Configure a route-policy RP and configure node 10 to permit the route that matches the IP prefix list huawei and deny all the unmatched routes.
[SwitchB] route-policy RP permit node 10 [SwitchB-route-policy] if-match ip-prefix huawei [SwitchB-route-policy] quit
Import the static route permitted by the route-policy RP into OSPF.
[SwitchB] ospf [SwitchB-ospf-1] import-route static route-policy RP [SwitchB-ospf-1] quit
After the preceding configurations are complete, check the IP routing table of SwitchC. The following command output shows that only the route 192.168.0.0/16 is imported into OSPF.
<SwitchC> display ip routing-table Route Flags: R - relay, D - download to fib, T - to vpn-instance ----------------------------------------------------------------------------- Routing Tables: Public Destinations : 5 Routes : 5 Destination/Mask Proto Pre Cost Flags NextHop Interface 10.10.12.0/24 Direct 0 0 D 10.10.12.2 Vlanif10 10.10.12.2/32 Direct 0 0 D 127.0.0.1 Vlanif10 127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0 127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0 192.168.0.0/16 O_ASE 150 1 D 10.10.12.1 Vlanif10